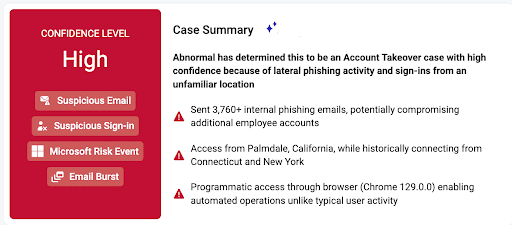
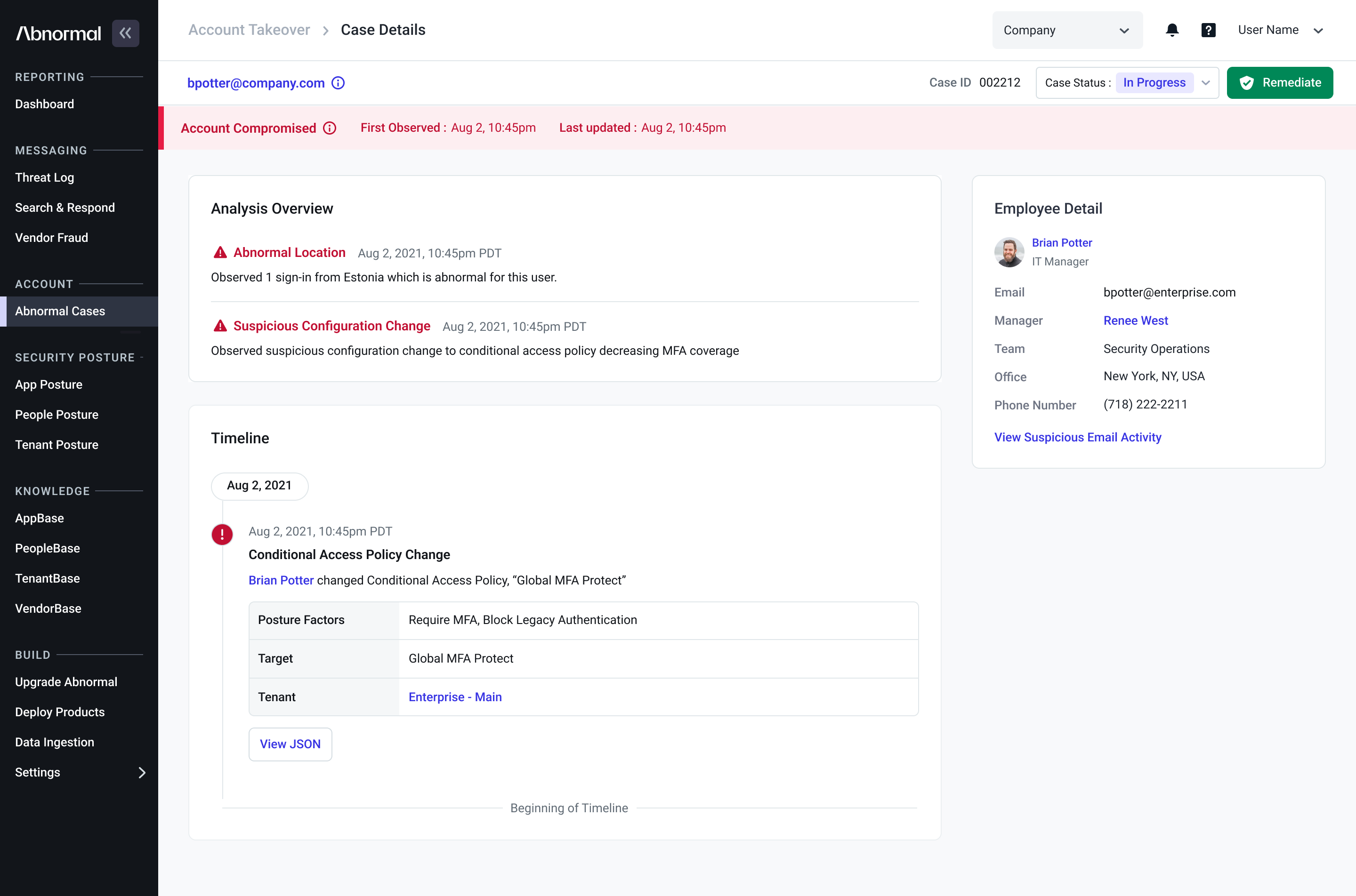
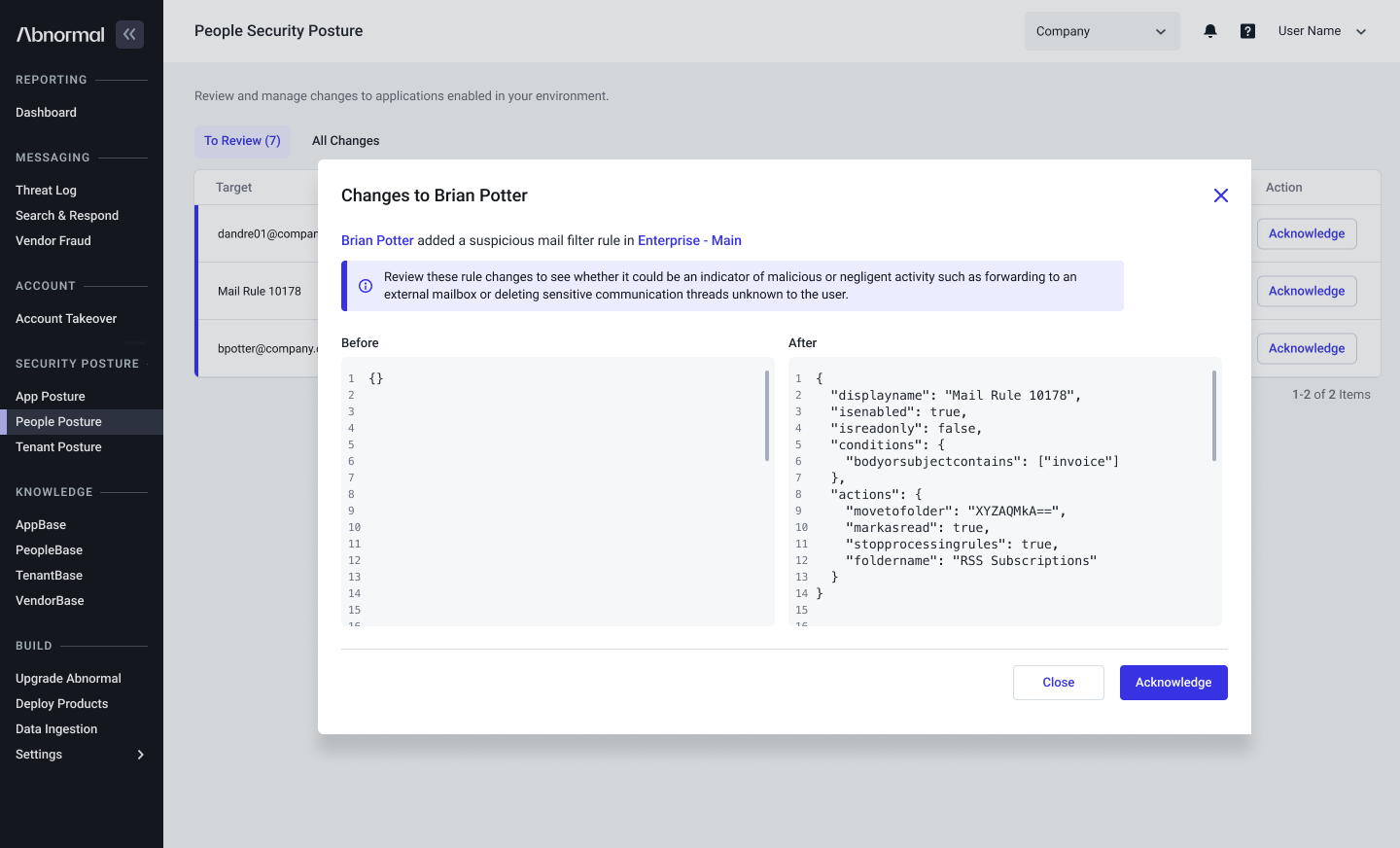
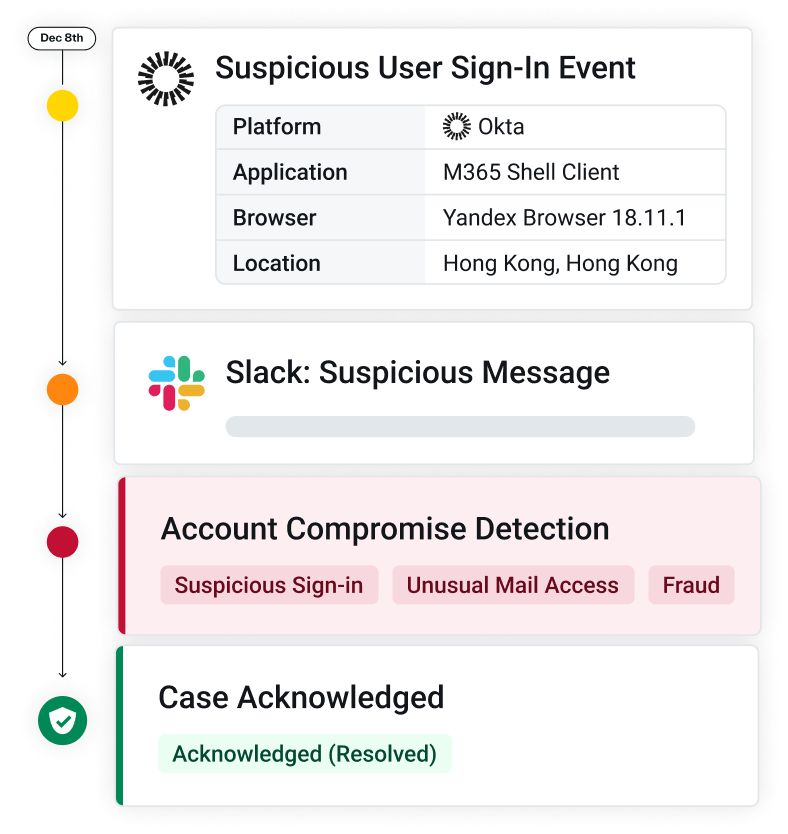
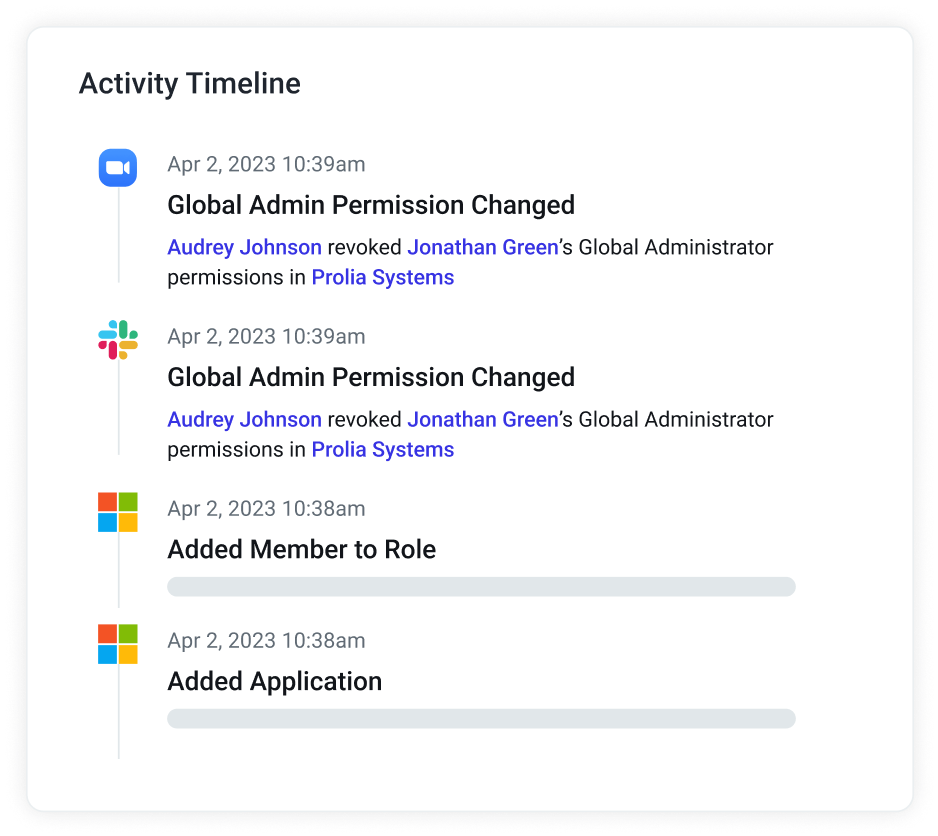
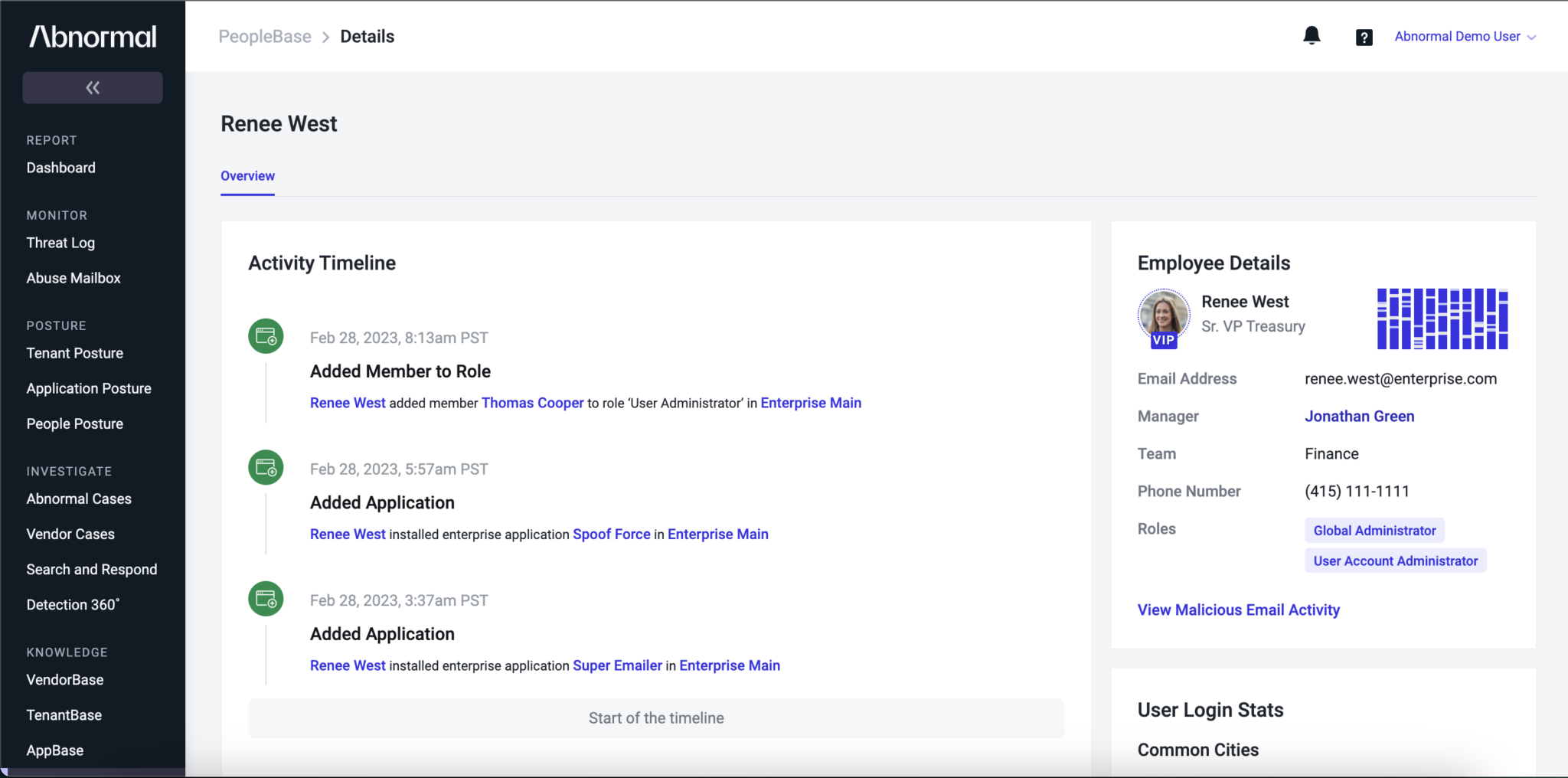
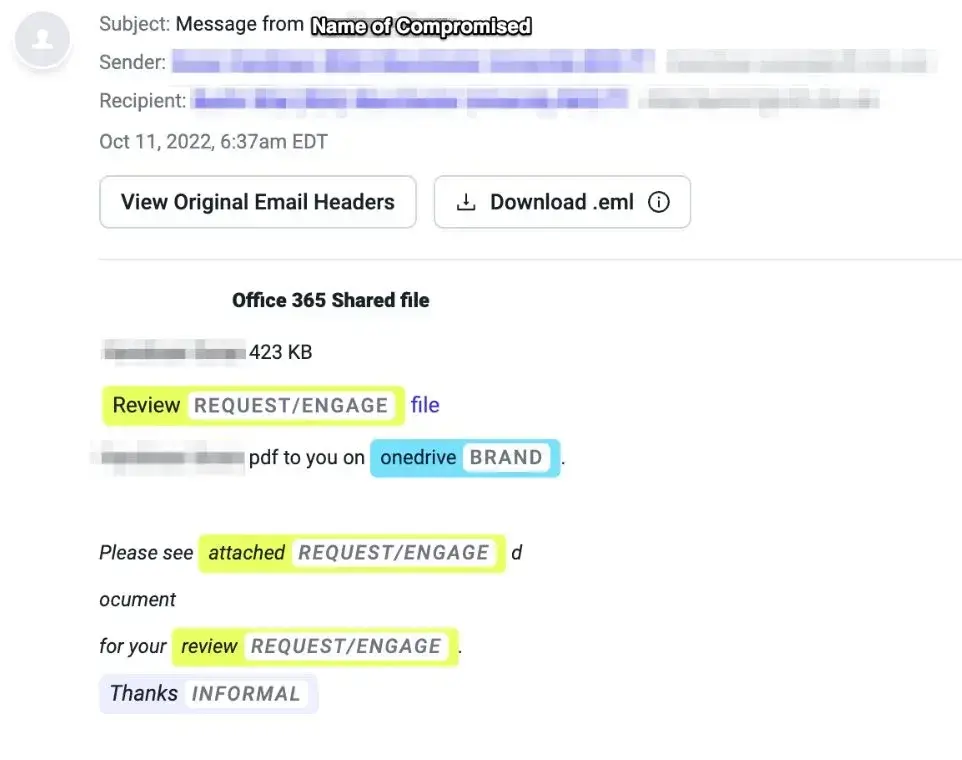
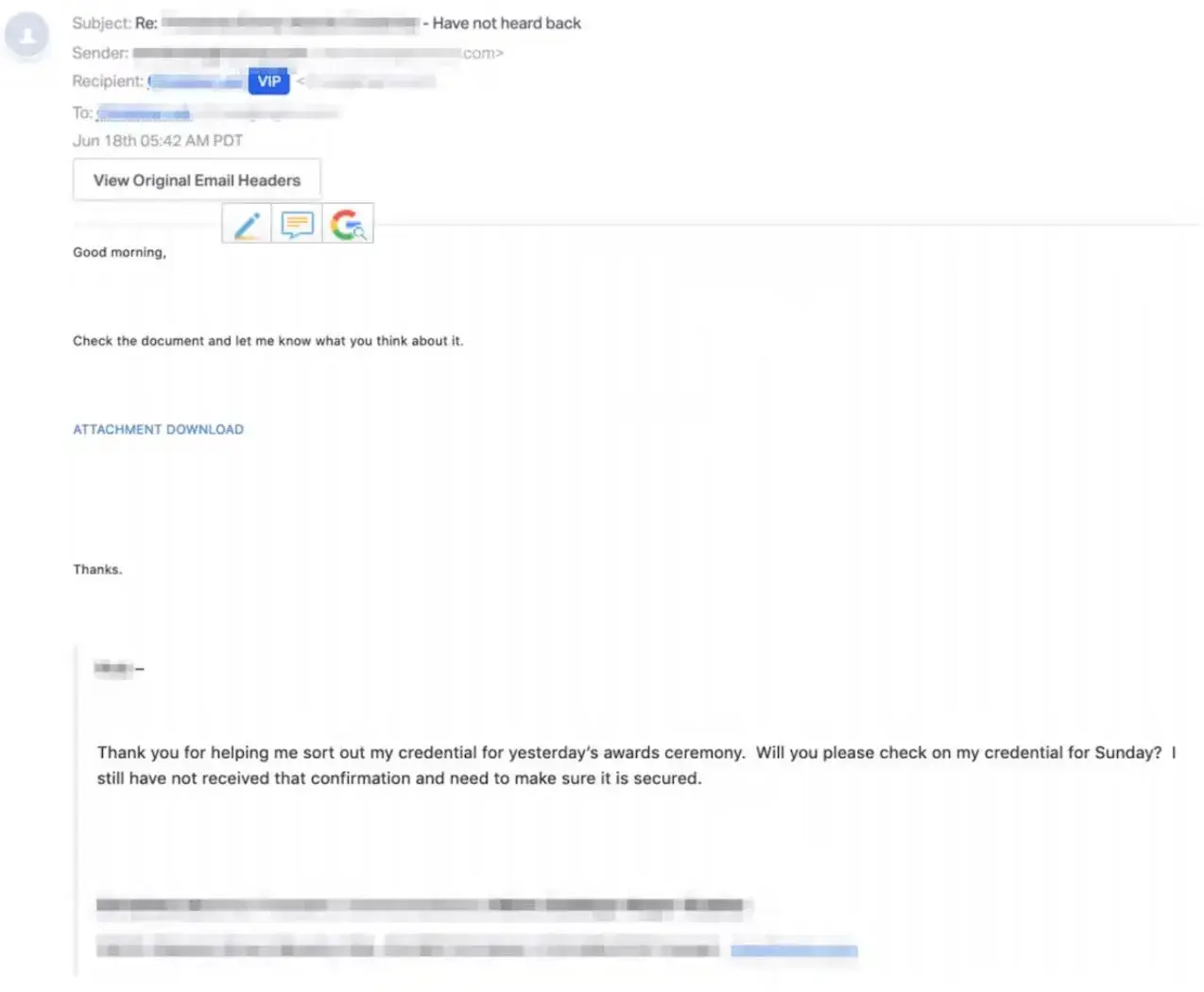
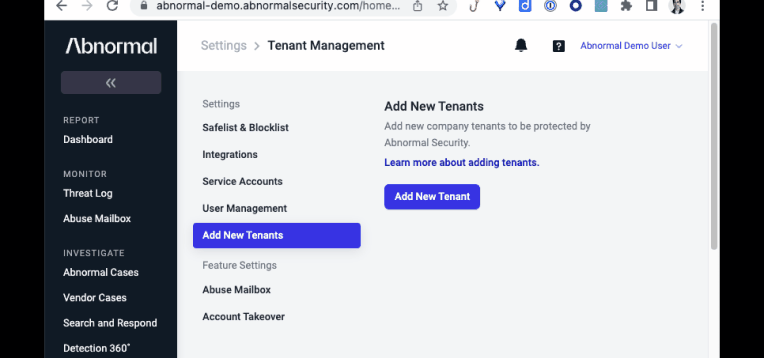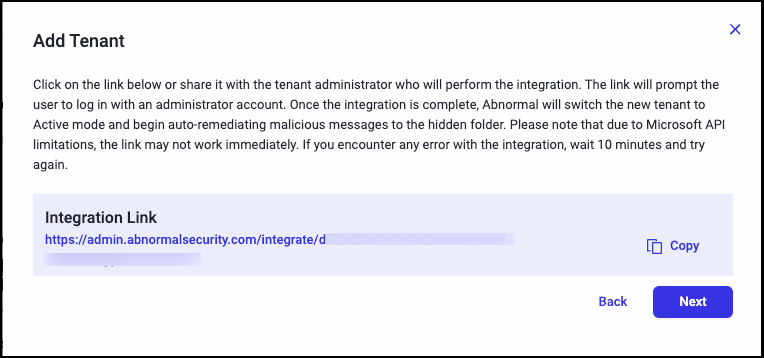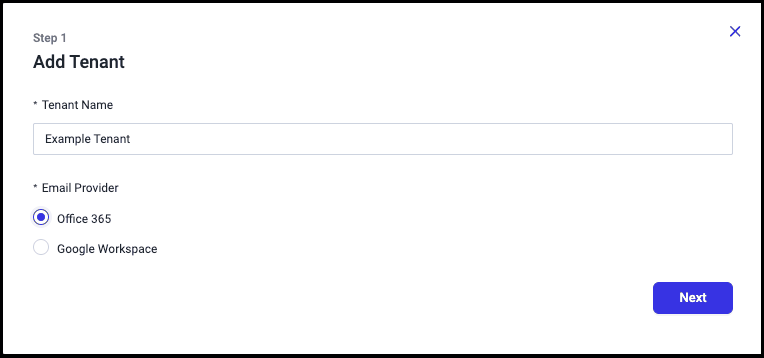
Investigating account compromise requires a precise understanding of attacker behaviors and tactics. With GenAI Case Summaries, you now get a clear, plain-language explanation of every ATO Case—automatically.
Out with the old descriptions that could often lack clarity of language and in with the new, AI-powered paradigm. Each Case includes a concise headline detailing attacker activity, a bulleted summary of tactics and key signals used in determining compromise, and user-specific context highlighting how this pattern of activity deviates from typical user behaviors.
Whether it’s high, medium, or low confidence, the summary helps you understand what happened and why it matters—fast.
There’s nothing to enable—GenAI Case Summaries are available in the portal today, so you can start making sense of suspicious activity without the guesswork.