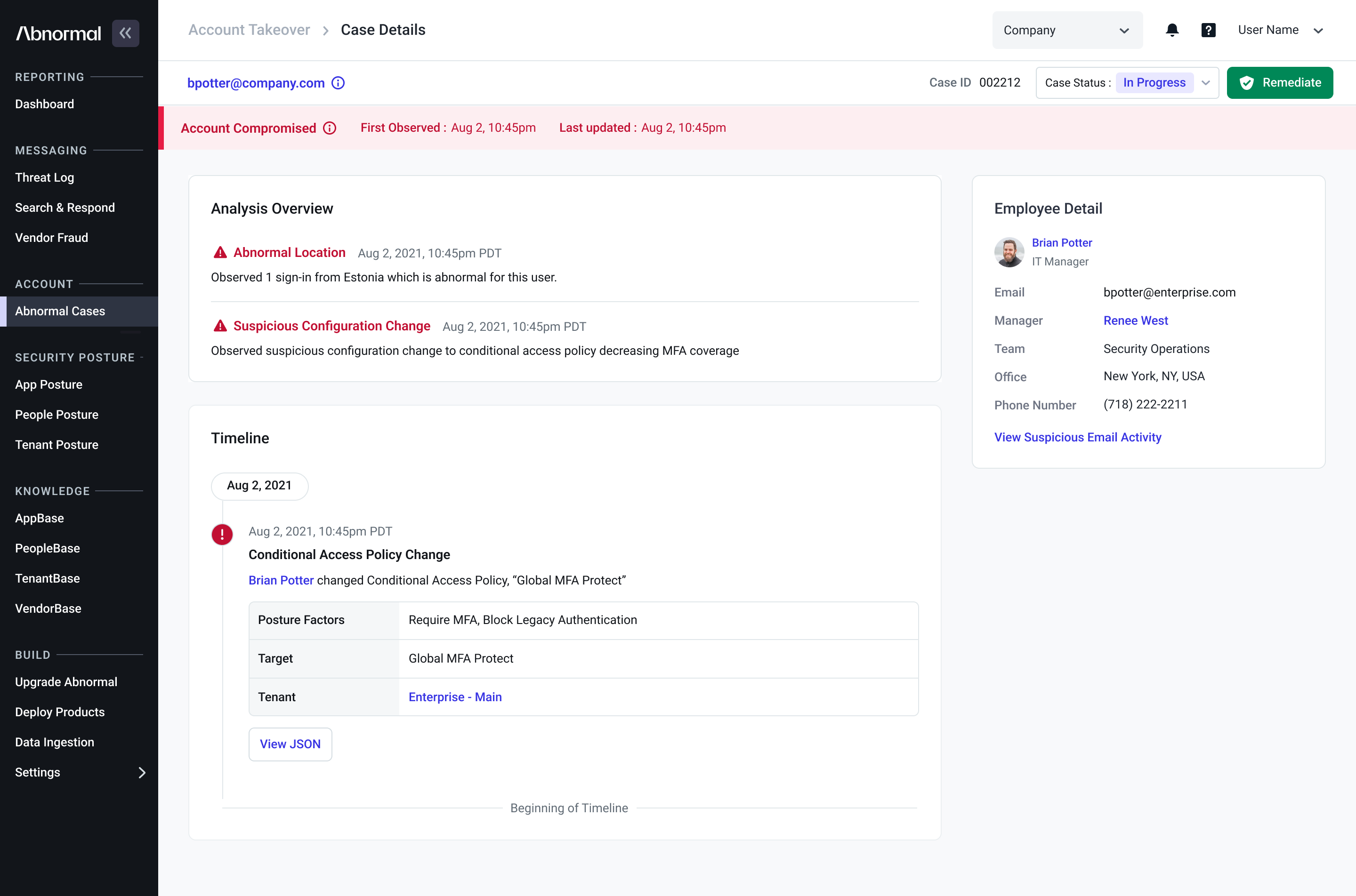
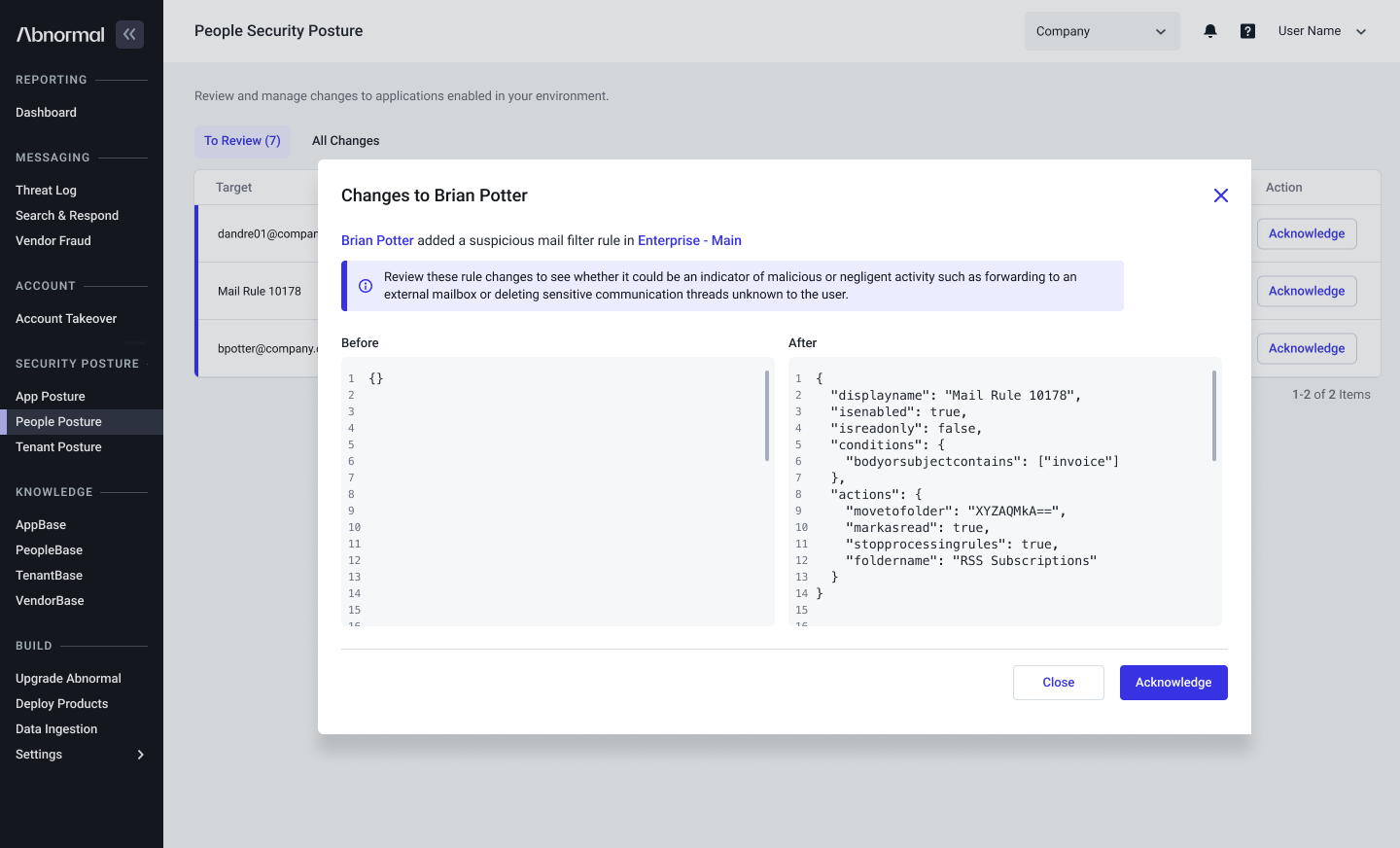
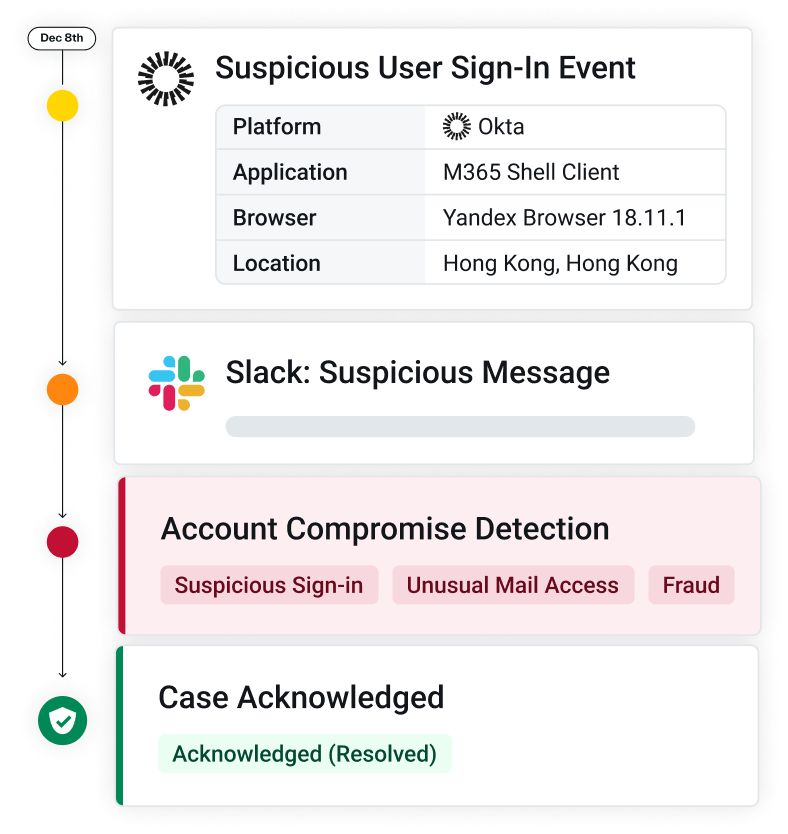
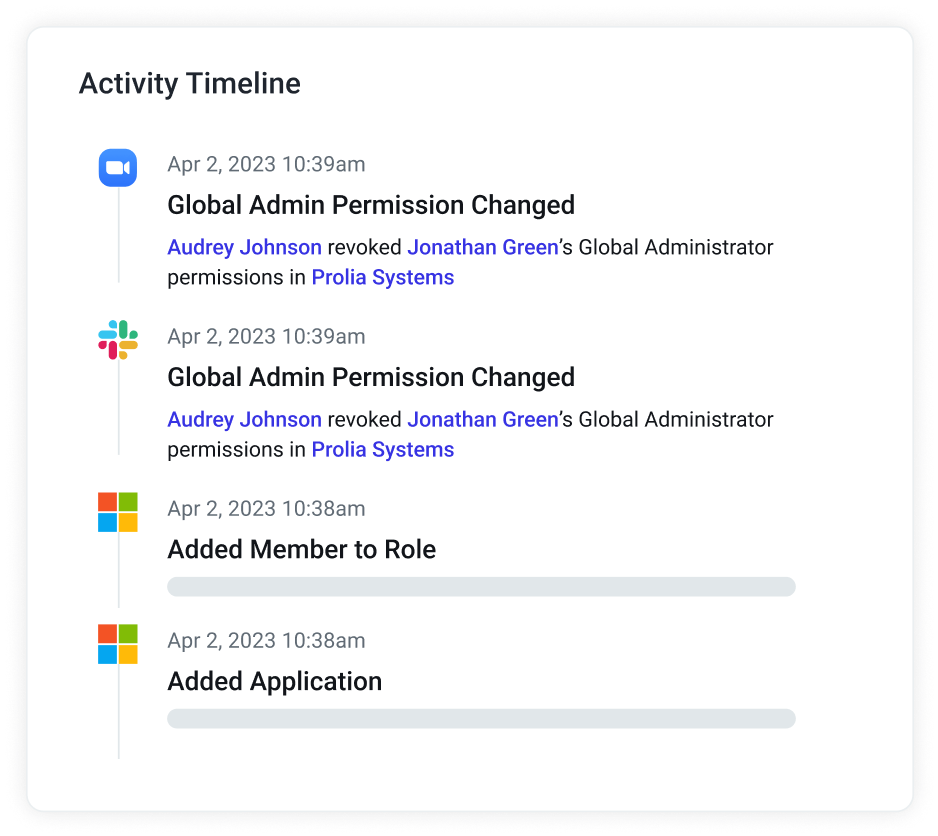
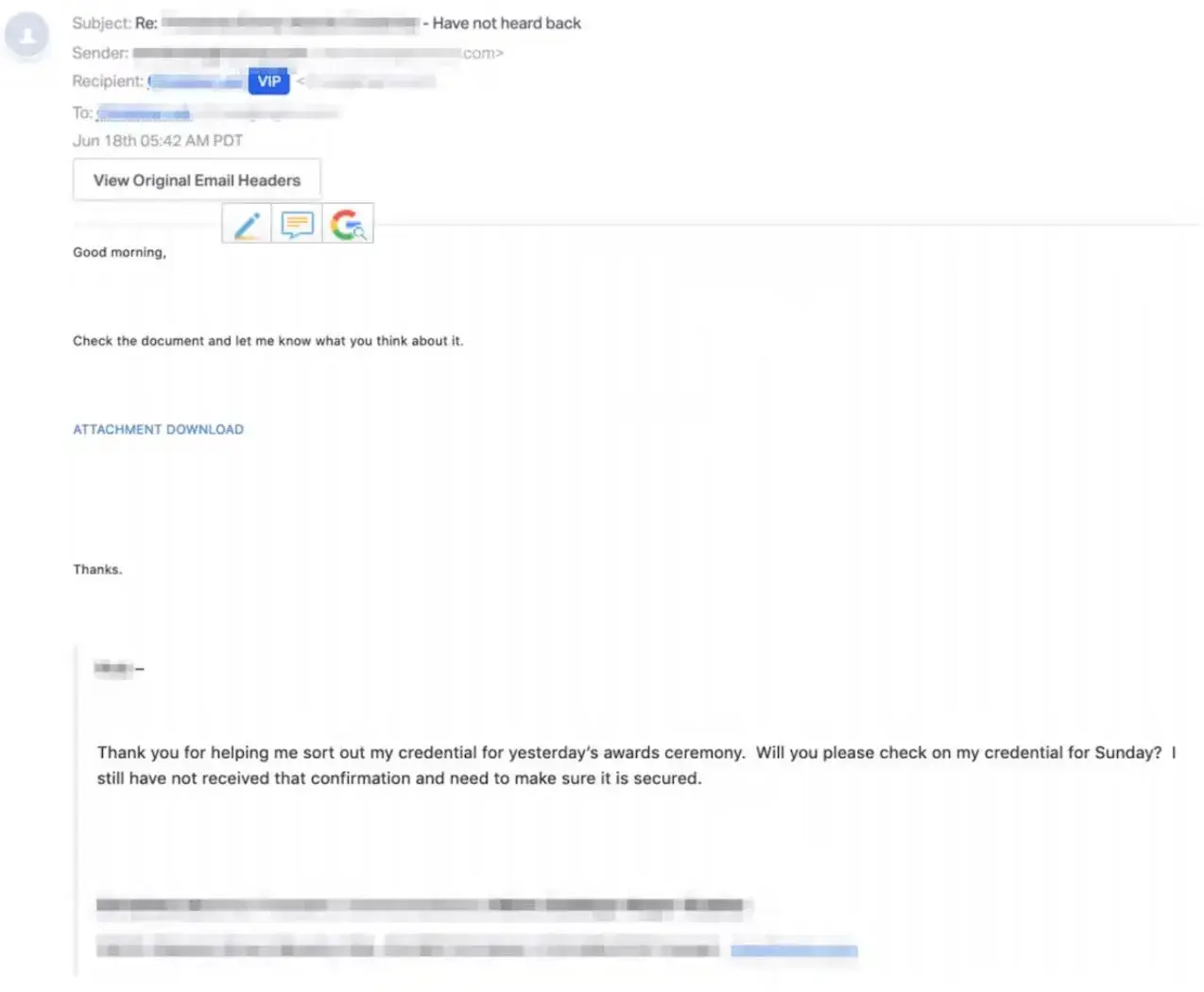
Adopting new technology can feel like a leap, but we’ve made it seamless with our phased rollout for GenAI auto-responses. What’s changed?
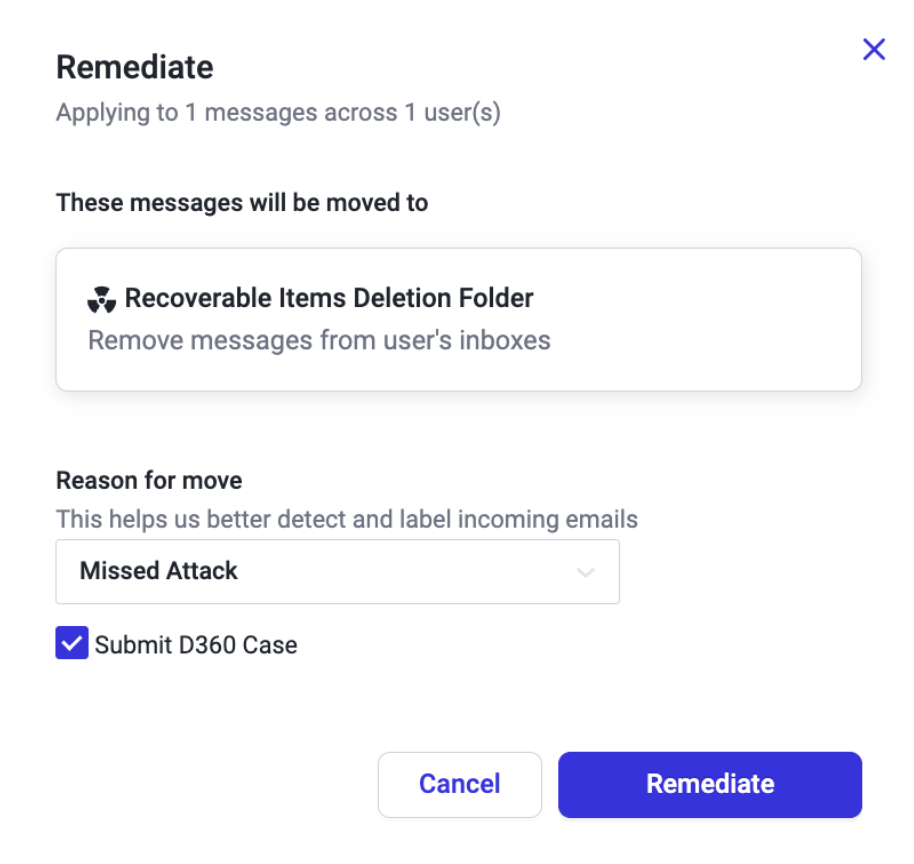
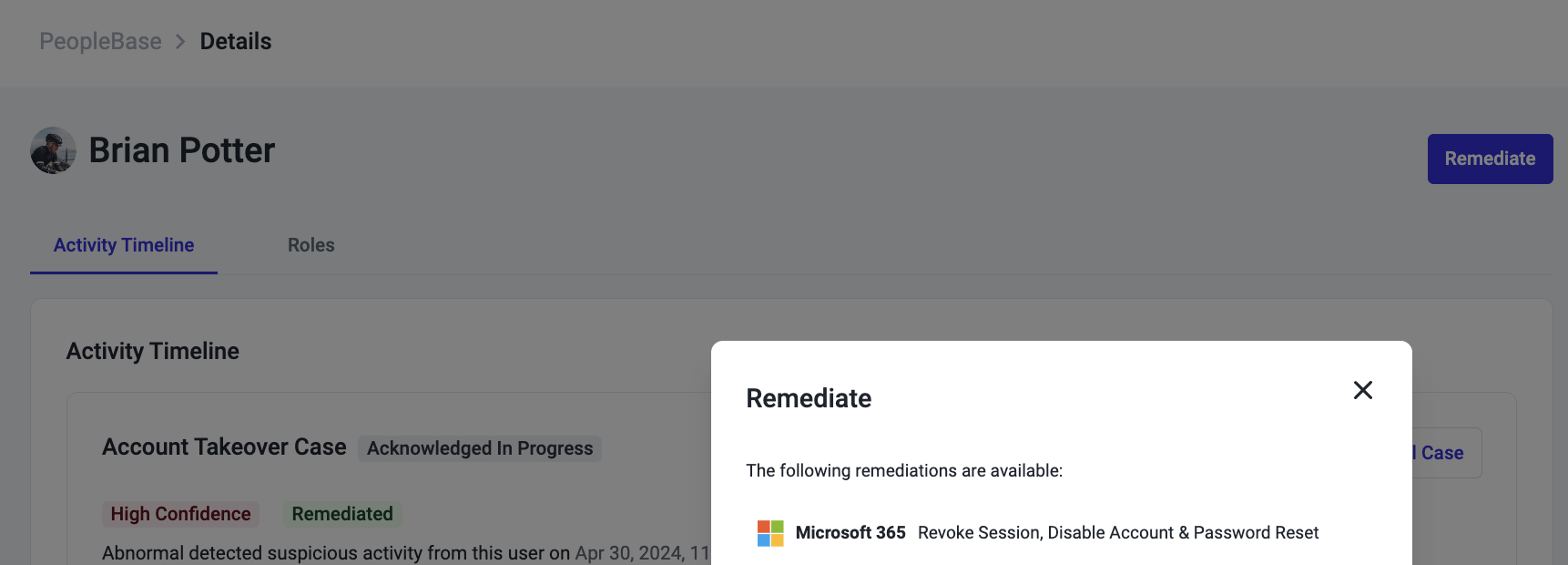
You can now enable GenAI auto-responses for up to 50 users, giving you the opportunity to test, familiarize yourself with the functionality, and meet change control requirements before transitioning your entire organization. This intentional subsetting approach ensures a smooth rollout and helps build confidence in the power of GenAI responses.
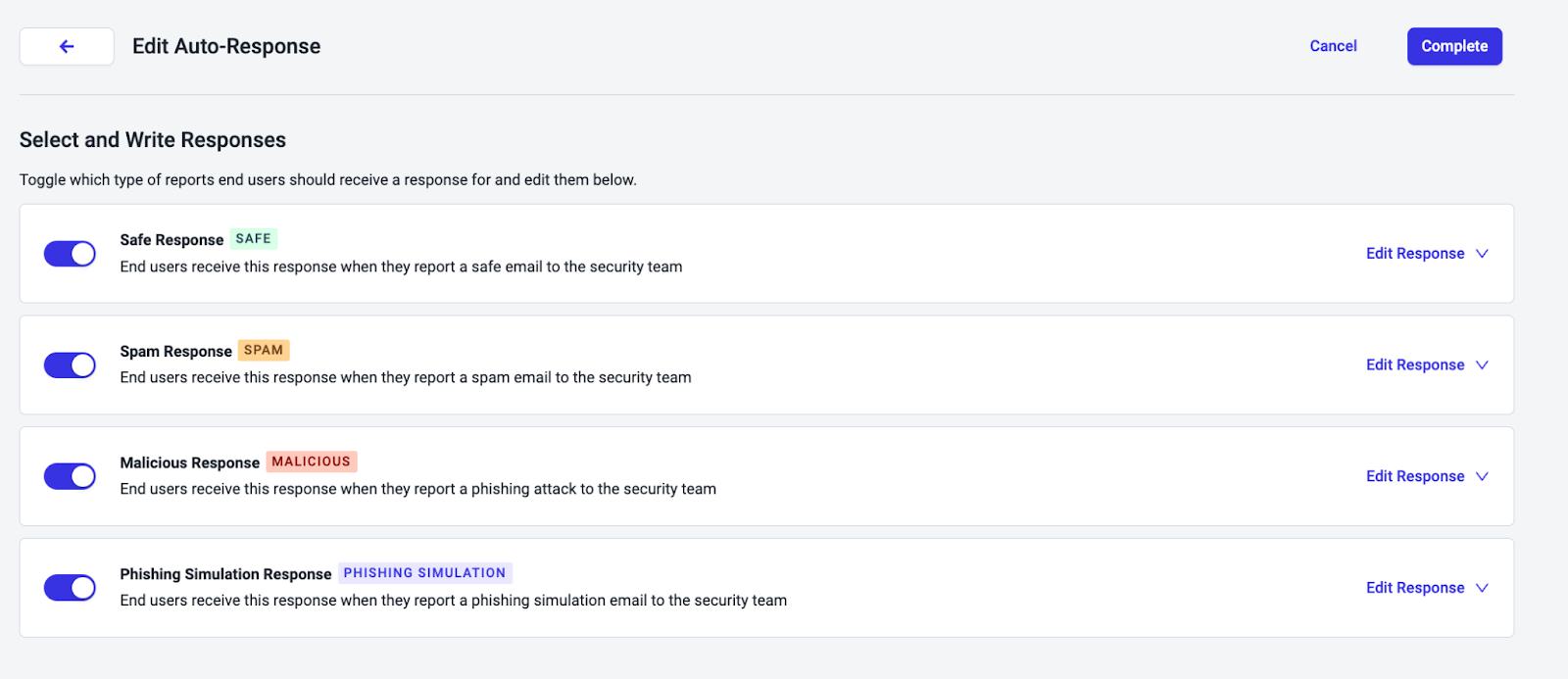
Ready to take the first step toward full-scale adoption? With Abnormal’s AI Security Mailbox settings, enabling GenAI Responses for select users has never been easier.