RFQ Scam Targets Vendors
Sending fraudulent purchase orders for goods and services is a common tactic attackers use to receive free merchandise. In this attack, attackers are impersonating the United States Transportation Command Office of Small Business Programs and sending an RFQ in order to steal goods from their targets.
Summary of Attack Target
- Platform: Office 365
- Email Security Bypassed: Proofpoint
- Payload: Attachment
- Technique: Impersonation
Overview of the RFQ Scam
The method of operation starts with the attacker emailing the vendor for a specific set of merchandise. The email impersonates the United States Transportation Command Office of Small Business Programs, which has an official domain of “ustranscom.mil”, but this email was sent from a “mall.mil” domain that does not have a public listed server. The reply-to domain "mil-mail.us" is different and is registered to a fake account just a day before the email was sent. Additionally, the sender is purported to be the point of contact for the Office of Small Business Programs, but the email and phone number provided do not match public records.
The email doesn’t address a specific person, but states the intent to procure a large order of a specific IT related product from the supplier, which are 27 HP Elitebook laptops.
After the vendor responds, an official-looking purchase order is delivered containing the logo, contact information, and most importantly, the delivery information for where the goods are to be shipped. The order form has contact information on behalf to USTRANSCOM with a mismatched signature and a phone number. The attackers request that the items be sent within three weeks.
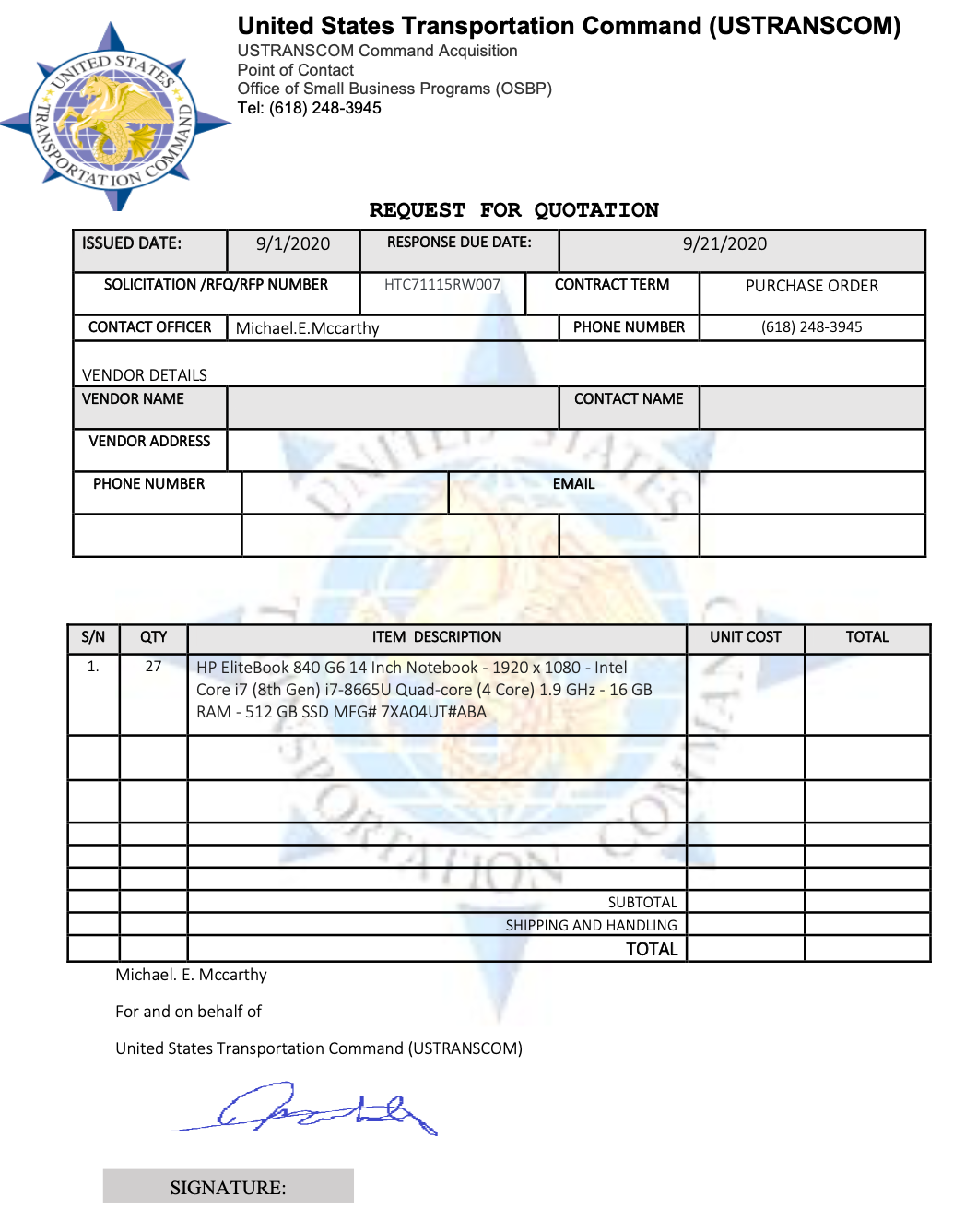
If recipients are tricked into fulfilling the request, the goods are shipped to an address that is unrelated to the party they are impersonating, and no payment will be made for them. While this is a different type of attack than a traditional fake invoice or payment fraud attack, it still provides valuable money to the attackers, who can sell the high-priced items once they have been delivered.
Why RFQs Scams are Effective
In this attack, the cybercriminals sends an email that appears to be from USTRANSCOM and even has the official logo on the RFQ form to appear legitimate. The email domain the message was sent from was recently registered, and the registrant information is not consistent with the impersonated party. The domain is first hosted on “mall.mil” and then the reply-to domain "mil-mail.us" in order to mimic a “ustranscom.mil” domain. This is likely to instill a sense of confidence in the recipient that the request is originating from a government entity.
In addition, this is a relatively new type of cybercrime, as it does not directly provide money to the attacker. The attacker may be hoping that the recipient is unaware of this type of scam and will complete the order as asked.
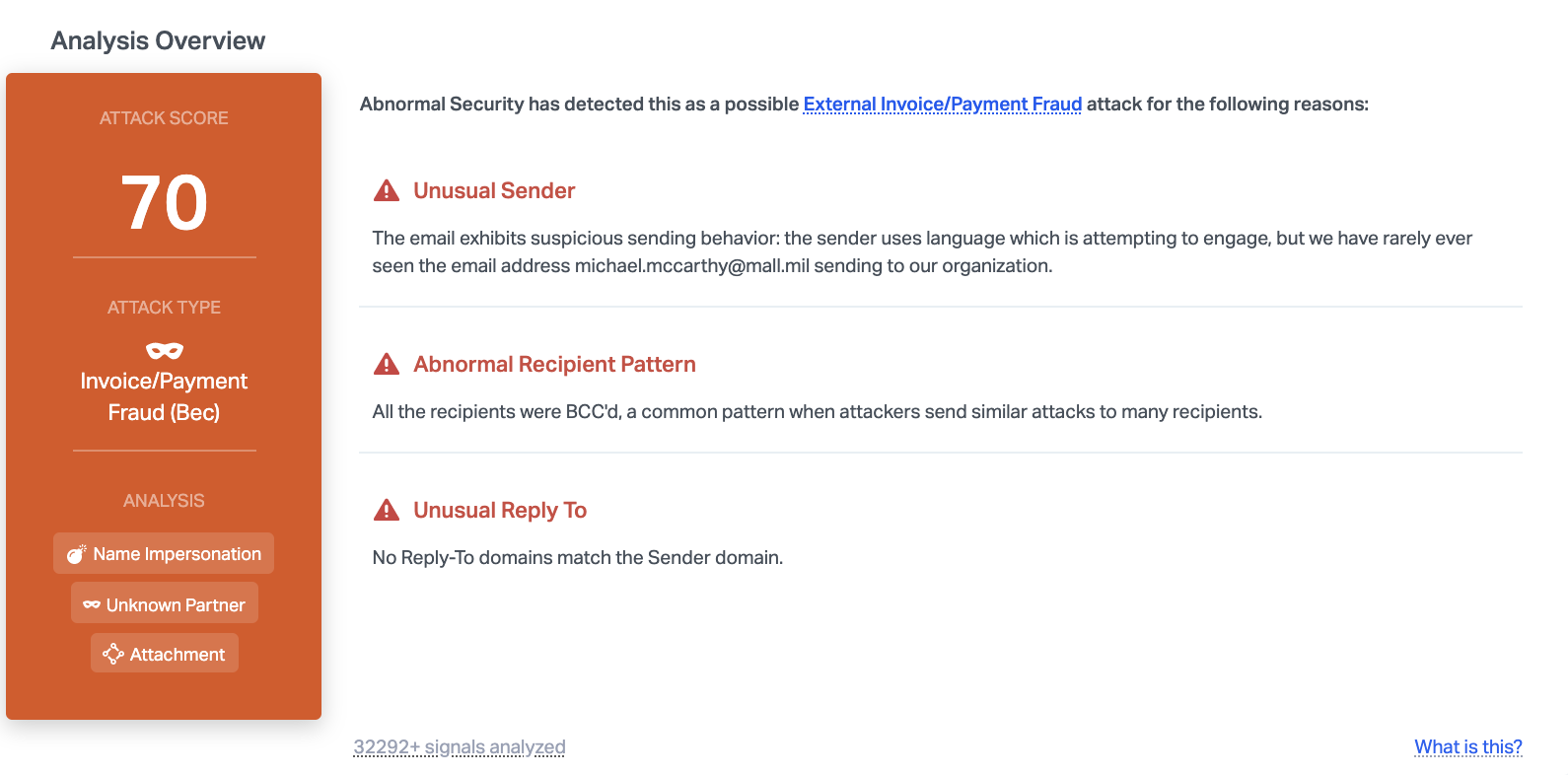
Abnormal is able to detect this malicious email due to the unusual sender, the unusual reply-to address, and the fact that all recipients were BCC'ed, a common pattern in cyber attacks. In addition, the content of the email indicates that it may be related to financial fraud. Combined together, this provides enough information to understand that this email is malicious, and it is blocked before reaching inboxes.
Discover how to protect your employees from RFQ scams by requesting a demo of Abnormal today.






