BB&T Bank Impersonated in Financial Phishing Campaign
Because they contain the keys to the financial kingdom and allow attackers direct access to money, banks tend to be some of the most impersonated organizations. In this attack, attackers mimic an automated notification from BB&T in order to steal recipients' online banking login credentials.
Summary of Attack Target
- Platform: Office 365
- Victims: Employees
- Payload: Malicious Link
- Technique: Impersonation
Overview of the Bank Impersonation Attack
Cybercriminals are increasing their efforts in an especially vulnerable time to access liquid funds from bank accounts. This attack features an impersonation of a well-known bank with realistic login pages and disguised URLs to launch a phishing attack on an unsuspecting user.
The initial email impersonates an automated notification from BB&T. Within the body of the email is a brief message stating that the user has been locked out of their account from too many login attempts. The message provides a text-embedded link that redirects the user to a phishing landing page.
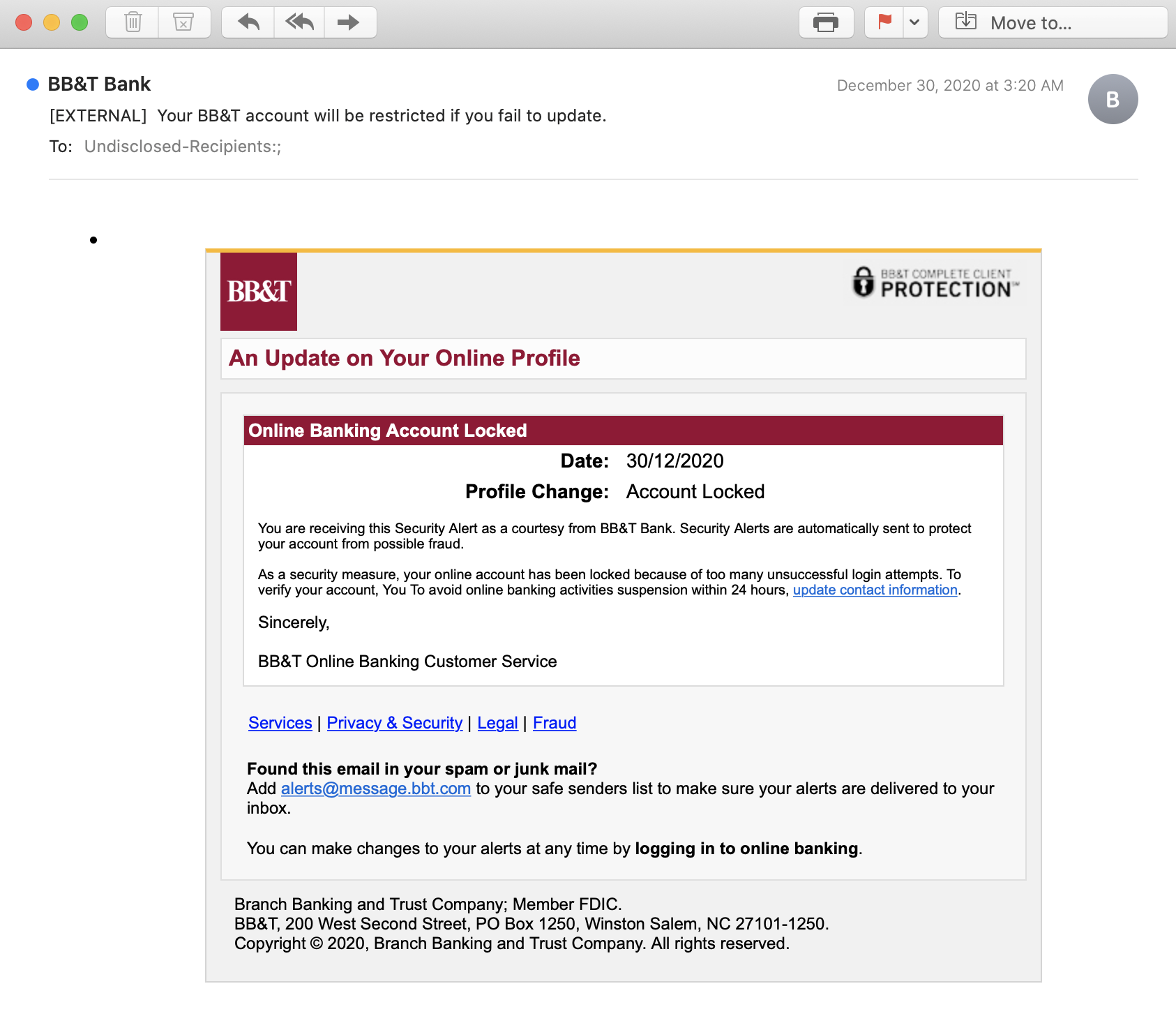
After a user clicks on the link, the page is redirected to a URL hosted on “mongolian-appraisal[.]000webhostapp[.]com.” The domain from the embedded link before the first redirect “ht[.]ly/rSgN30rqCSq” is registered to the Libyan Spider Network. Further, the IP originates from a commercially available VPN service, which is a strong indication that this is not a legitimate landing page for BB&T.
Nonetheless, the landing page appears legitimate and an unsuspecting user concerned about a bank suspension may not notice that the link has changed from one owned by the bank.
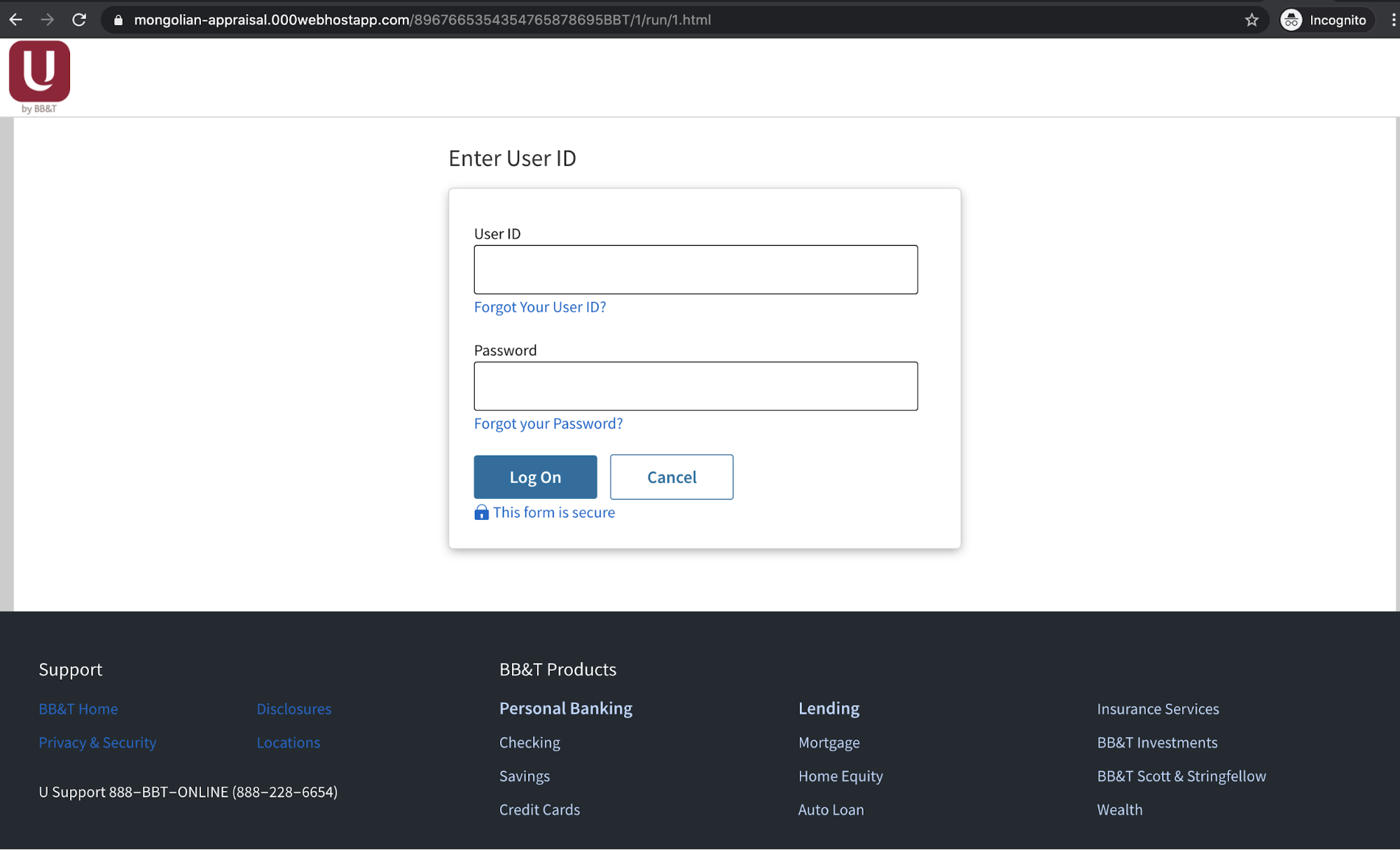

For those unlucky to be targeted, the attackers went through an extra step and required that users enter a CAPTCHA code in order to access the account, adding to the legitimacy of the interaction. Once recipients enter their username and password, they provide attackers with their personal banking information, which can then be used for fraudulent purposes, including the transfer of all money out of the account.
Why the Attack is Effective
Banks often send email notifications regarding online banking activity. The email looks like a simple, legitimate request to update contact information and the landing page appears nearly identical to what a user would expect after clicking on the link. The attackers take an extra step, asking the recipient to complete an additional security verification step, simulating the experience of logging into their account and hoping to remove doubt about legitimacy.
And while the email appears to be automated, the urgency comes from the indication that the recipient has been locked out of their account from too many unsuccessful login attempts. This is the honeypot, provoking fear in the recipient that someone else is attempting to log in to their account and prompting them to take immediate action.
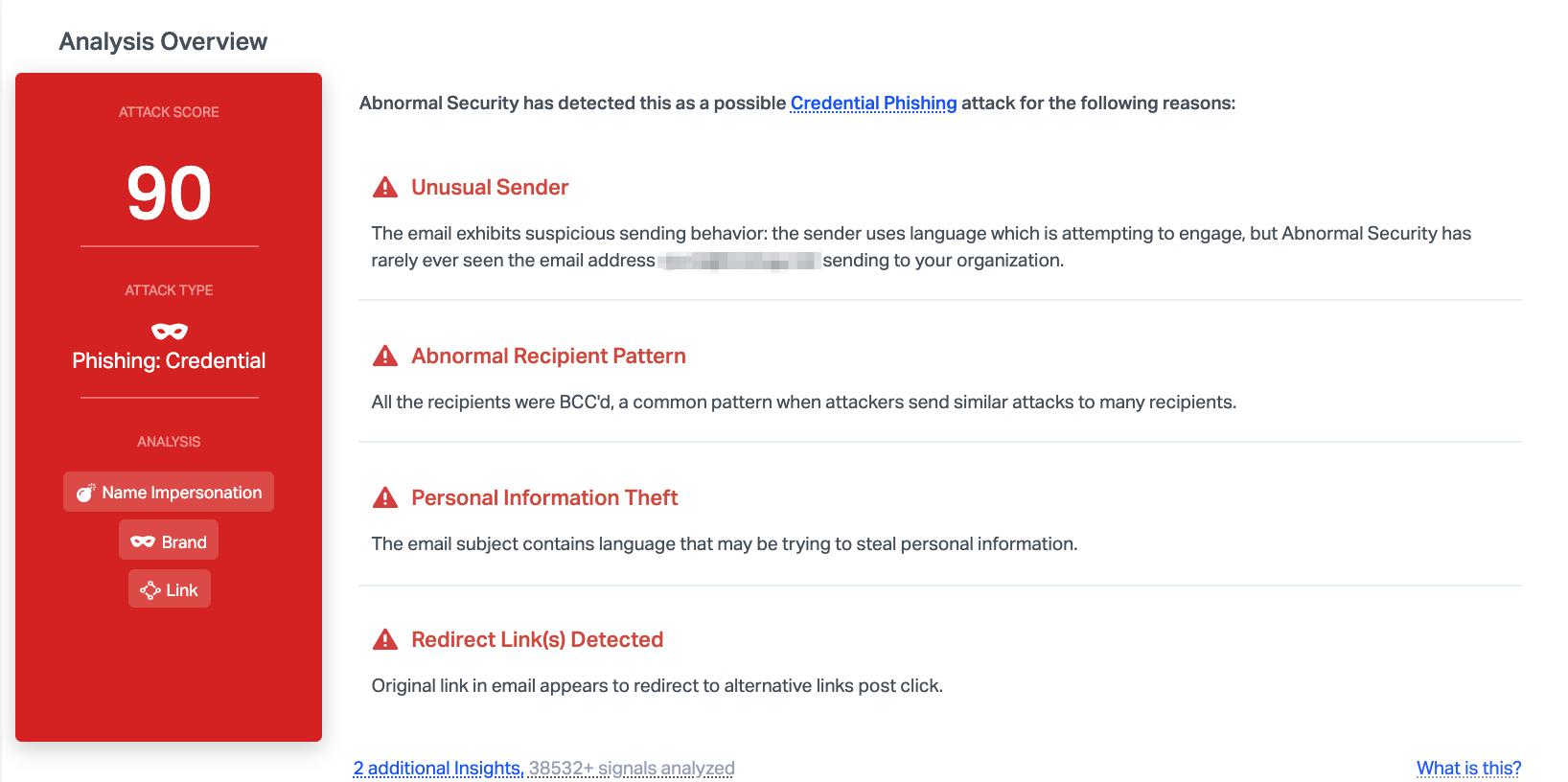
Abnormal Security detected this as a credential phishing attack based on a number of factors, including the unusual sender information and the redirect links detected. We also noticed that all recipients are BCC'd, a common pattern for attacks and uncommon for legitimate automated messages. Combined together, this indicates that the attack is malicious and we can block it before it reaches user inboxes.
To learn more about how Abnormal prevents all types of credential phishing attacks, request a short demo with an Email Security Specialist.






