Microsoft Renewal Scam Leads to Financial Loss
Microsoft Office offers one-time purchase and subscription plans and has numerous official resellers for its products. Scammers use this fact as an opportunity to impersonate Microsoft and their resellers in order to steal sensitive user data, as well as for financial gain. In these attacks, cybercriminals impersonate renewal emails from Microsoft to steal sensitive user information and money.
Summary of Attack Target
- Platform: Office 365
- Email Security Bypassed: Proofpoint
- Payload: Malicious Link
- Technique: Impersonation
Overview of the Microsoft Renewal Scam
In both of these email attacks, the attackers impersonate a notification from Microsoft. The messages state that the recipient must renew their Microsoft Office subscription through the links provided. In the first attack, the recipient is told that they need to renew their Microsoft 365 subscriptions and is asked to click on a link to do so.
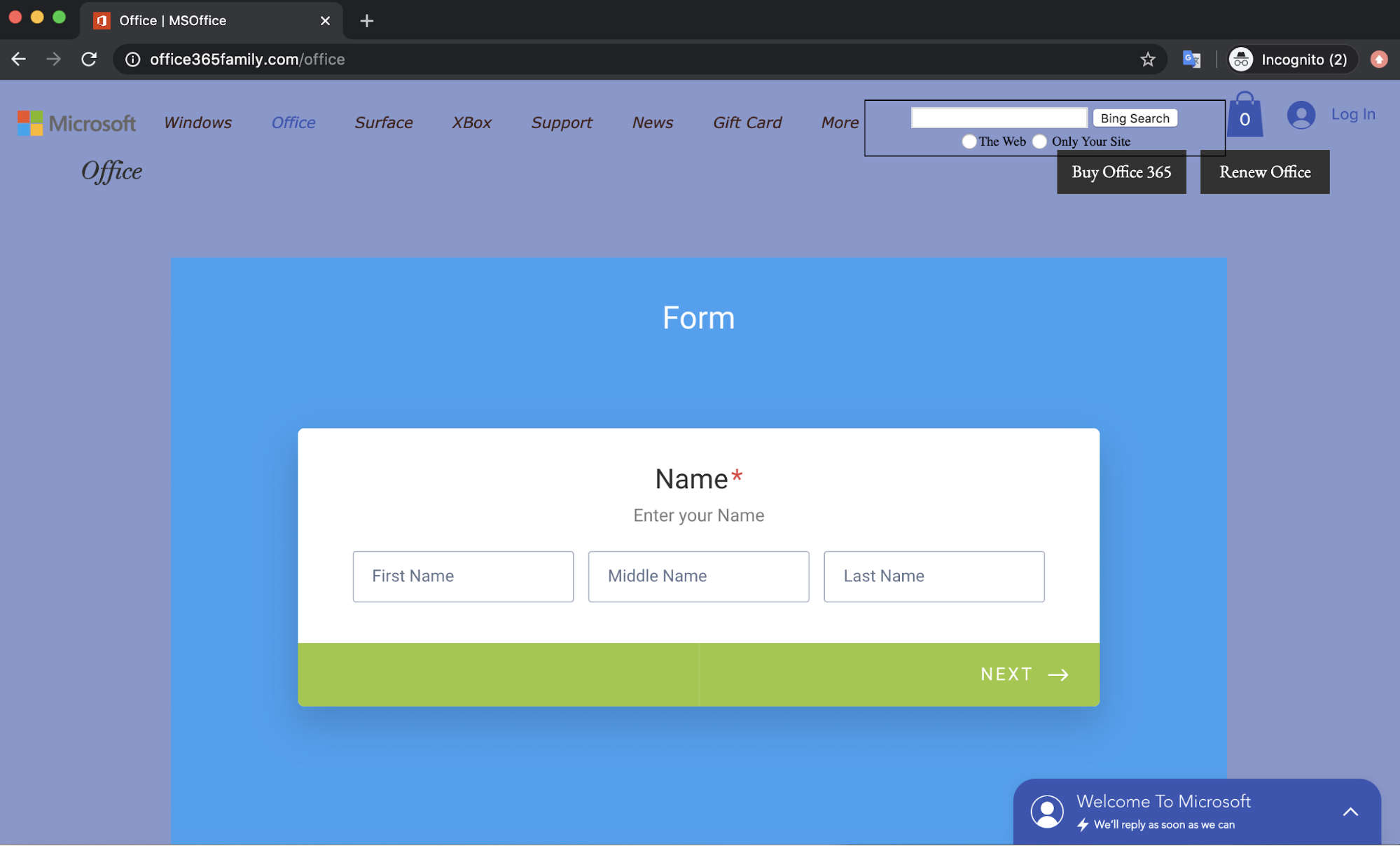
When recipients click, they are directed to a credential phishing page hosted on “office365family.com” which is registered by Wix, a commercial website builder. There is a submission form for sensitive user information, and includes fields for addresses and credit card information.
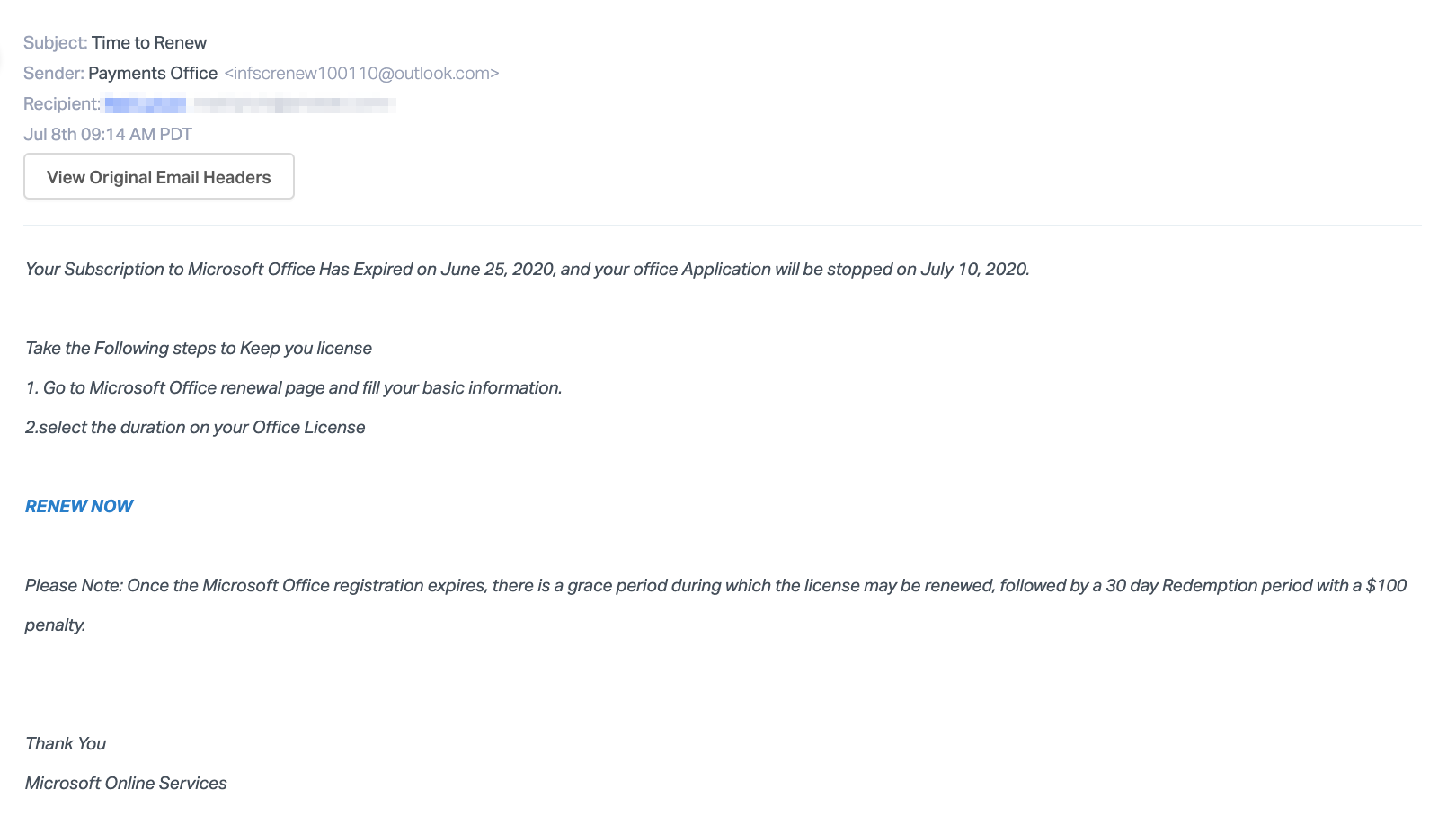
The second attack is similar in that it tells the recipient that their subscription to Microsoft Office has expired and they must click on a link to renew it now. The email also notes that they are in a grace period and there will be a $100 penalty to renew it later.
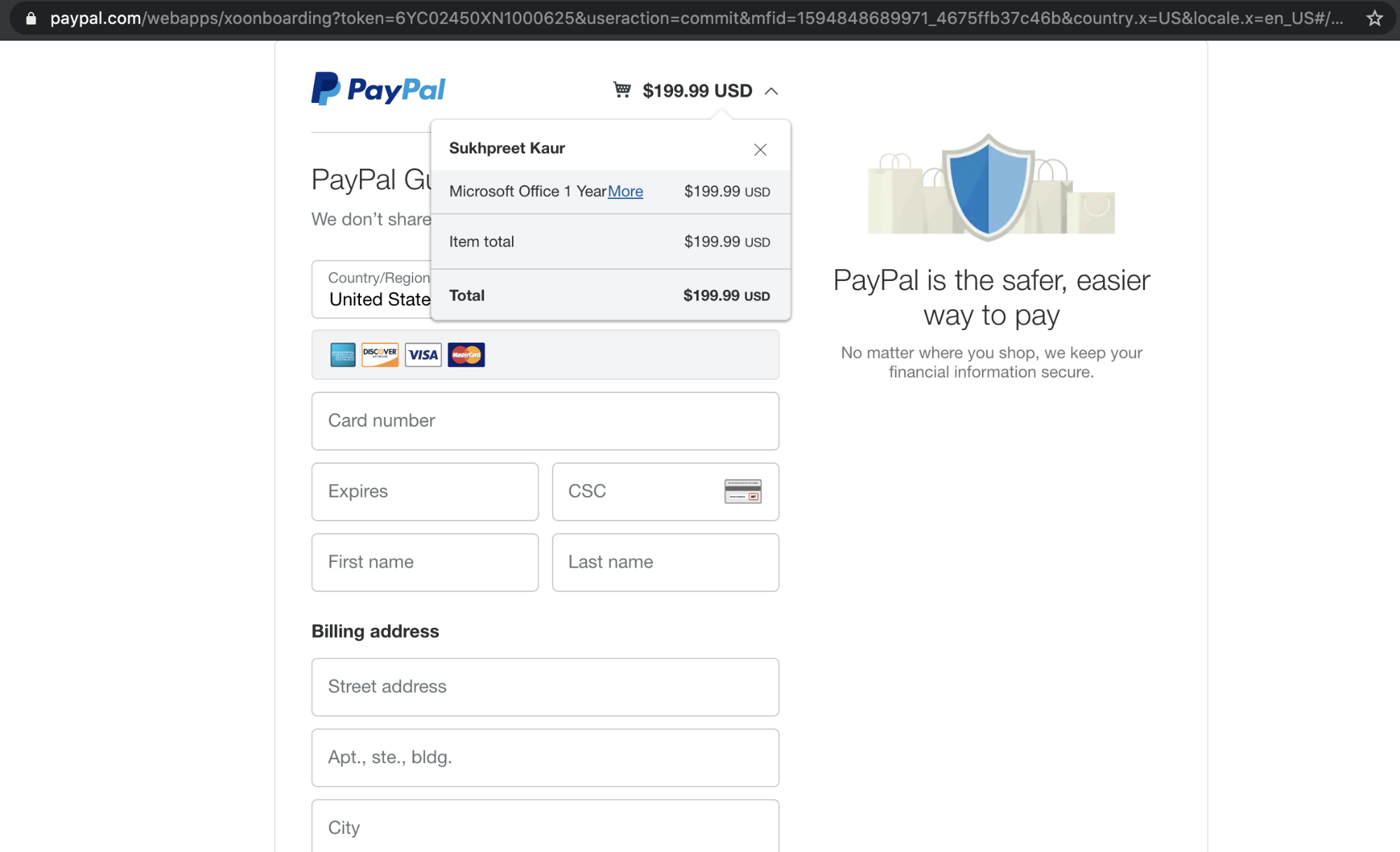
The link directs to a PayPal statement, which is an unknown individual’s PayPal account—not Microsoft. In fact, if the recipient were to conduct a search, they would discover that although Microsoft does accept PayPal, the payment option is added to the recipient's Office account, not directly from the PayPal website. If the recipient were to pay from the link provided, they likely be out $199.99 and would not receive the subscription renewal.
Though these attacks ask for different information—personal account details versus money—they are both malicious attempts to take advantage of unsuspecting users. If the recipient were to fall victim to either attack, they risk exposing their sensitive information and financial loss.
Why the Microsoft Renewal Scam is Effective
In both of these cases, the email body of each message appears to be an automated notification from Microsoft. By convincing the recipient that the messages are from an official source, recipients are more likely to follow the instructions contained in the message. As Microsoft Office is an essential subscription for both personal and professional use, the recipient will quickly try to renew this service. Both email attacks give the recipient two days before the deadline, with one of the attacks threatening a financial penalty if the deadline is not met. The sense of urgency the emails create could lead recipients to overlook suspicious signals, like the concealed link without verifying whether the URL is safe.
In addition, the payload link in one of the attacks is hosted on “office365family.com”, using the Office 365 brand name in the URL in order to convince the recipient that it may be an official Microsoft web page. It uses similar imagery, copies the Microsoft website footer, and uses the same official links. However, the inconsistent fonts as well as the many broken header links on this webpage indicate that this website is fraudulent. One important thing to note in both of these attacks is that they originate from email hosting services. These services are easy to create and send widespread attack campaigns from.
In the other attack, the email links to an authentic PayPal webpage. One might be convinced that this is a safe correspondence because of this real PayPal link. However, one thing to note is that there is no verification of what is being paid for. Though the details of the transaction note “Microsoft Office”, payment is made to an unknown individual, with no guaranteed transfer of goods.
Abnormal stops both of these emails before they reach user inboxes due to a variety of clues, including the suspicious sender, the brand impersonation attempts, and the fact that the links are suspicious. Combined with the suspicious language in the email, the platform can determine that the email is malicious and prevent it from taking advantage of unsuspecting users who would be included to keep their Office 365 subscriptions.
To learn more about how Abnormal can protect you and your employees from Microsoft spoofs, see a demo of the platform.






