WebEx Impersonated in Credential Phishing Attack
Companies have largely transitioned to working from home where they can in response to the current pandemic and are relying on conferencing software such as Cisco WebEx. Attackers are taking advantage of this transition to impersonate collaboration and enterprise software in order to steal user credentials.
In this attack, attackers mimic a notification from Cisco WebEx in order to steal the credentials of employees.
Summary of Attack Target
- Platform: Office 365
- Email Security Bypassed: MessageLabs
- Victims: Employees
- Payload: Malicious Link
- Technique: Impersonation
Overview of the WebEx Phishing Attack
The attacker sent an email impersonating an automated email from Cisco WebEx, copying the formatting and graphics used by real emails from this company. It claims that the user is unable to use this service and that the user account is currently locked. To unlock their account, they must sign in with the provided link.
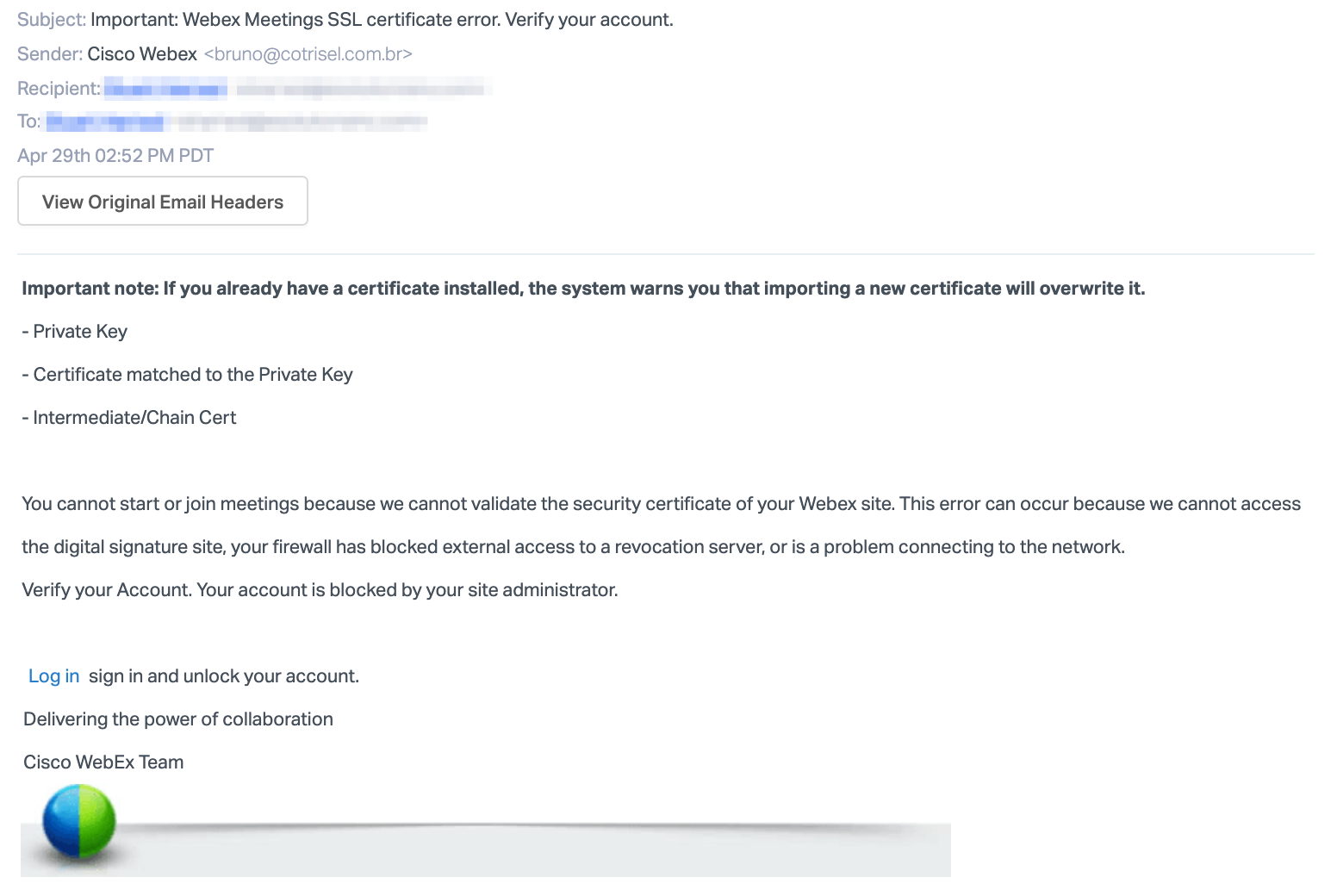
The email includes a SendGrid link that redirects to a phishing credentials site hosted at “https://app-login-webex.com/”. Because the link includes the WebEx information, it is very convincing—especially considering how similar it looks to the real login page.
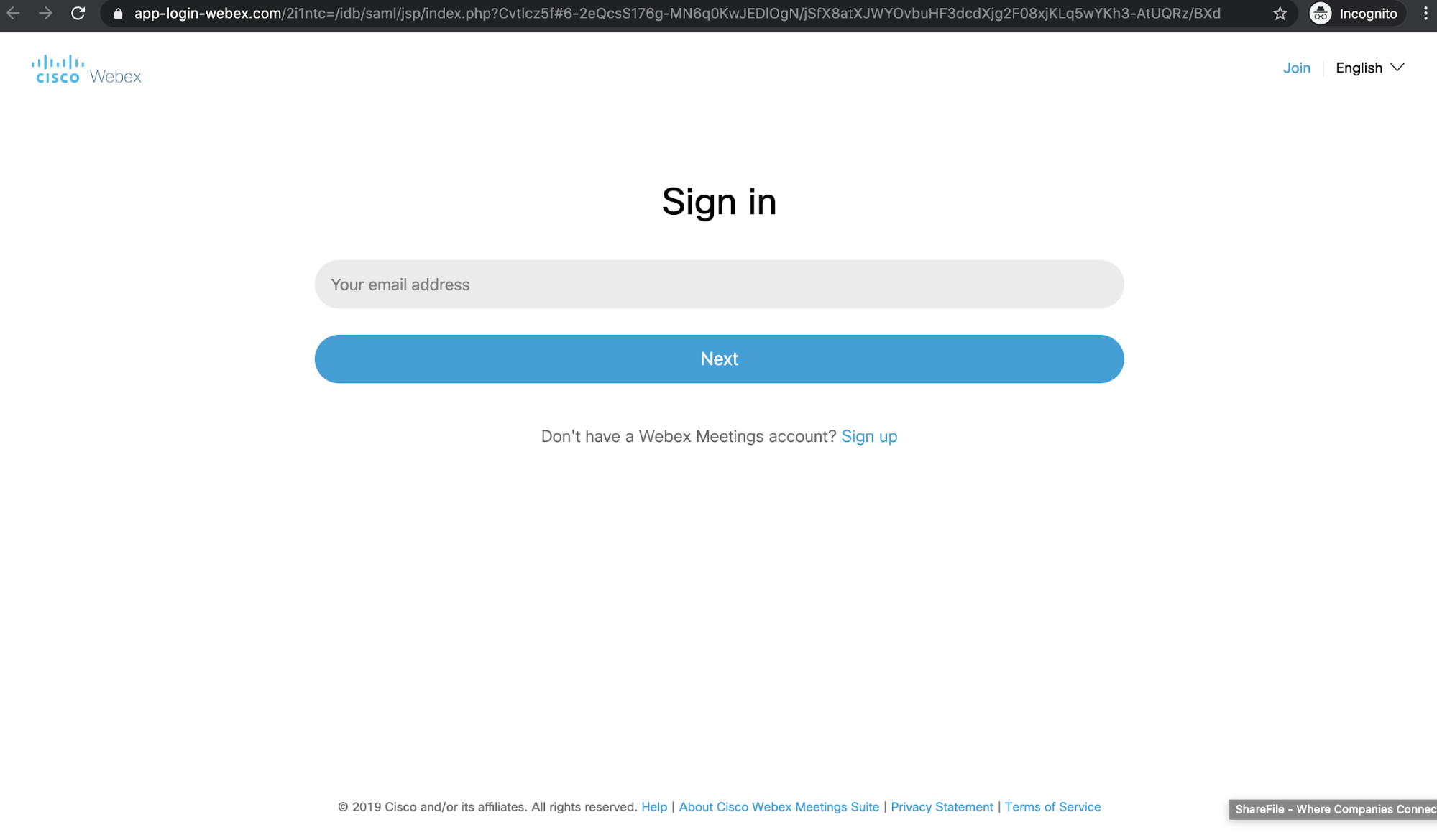
The domain of this webpage has been recently registered by a registrar in the Czech Republic, and is not affiliated with Webex or Cisco more broadly. Attackers likely control this website and use it to steal user credential information.

Should recipients fall victim to this attack, their Cisco WebEx account—as well as other personal information stored on the account—would be at risk. The attacker could use the compromised user account to send further attacks within the organization and to external partners.
Why the WebEx Impersonation Attack is Effective
The attack states that the user account has been locked, and they cannot host or join meetings until the situation is remedied by unlocking their account through the link provided. The attacker injects a sense of urgency, as the use of WebEx as a meeting software has become a vital tool for business correspondence, especially during the current work-from-home situation.
Making it harder to detect, the email and landing page that the attacker created were convincing. The email was spoofed to appear like an automated notification from Webex, using the logo of the company to appear authentic. The landing page was almost identical to the real login page, and the URL even imitates the platform’s name. The URL is also wrapped in text, and sent via a SendGrid Link. The attacker does this to conceal the real URL, and the user would be unable to distinguish whether the link is authentic until they clicked on it. Attackers likely expected that recipients would not scrutinize the link and assume the landing page was valid.
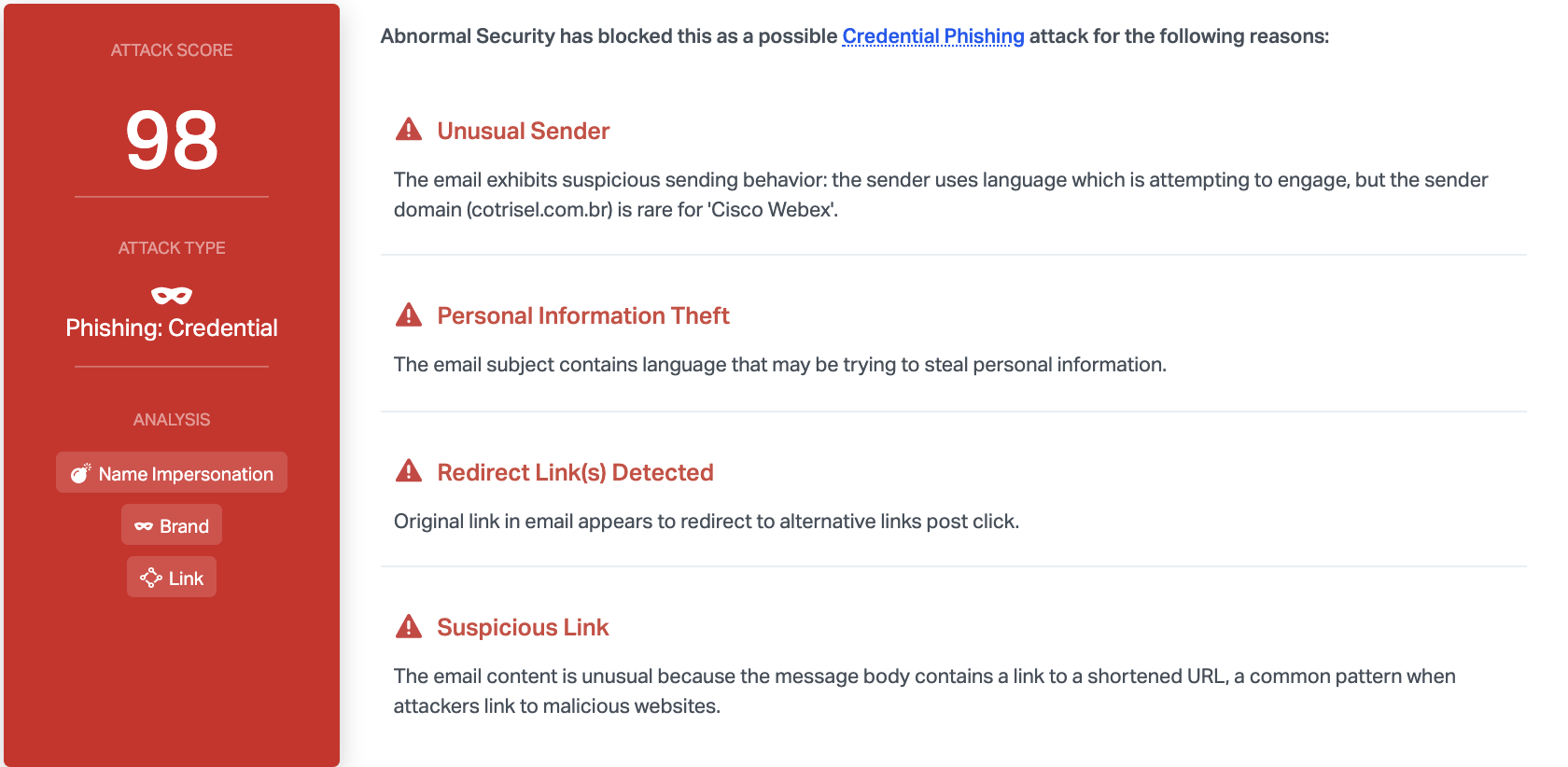
Abnormal is able to detect this attack due to the unusual sender, the redirect links detected, and the link to a the shortened URL. We also notice that the content contains language that may be trying to steal information like credentials. Combined, it quickly becomes clear that this email is malicious, and Abnormal can block it before it reaches inboxes.
Discover how Abnormal can protect your organization from impersonation emails by seeing a demo today.






