Calendar Invite Used to Access Bank Accounts
Financial institutions are common targets for attackers because of the amount of money in their control. Access to a user’s sensitive information would allow an attacker to commit identity theft, as well as steal any money associated with the account. Many of these companies have stringent regulations and security in order to protect users and their financial holdings. However, attackers are continually finding ways to compromise users’ accounts.
In this attack, attackers impersonate a company's security team to send out phishing attacks contained within calendar application invites.
Summary of Attack Target
- Platform: Office 365
- Email Security Bypassed: FireEye
- Victims: Employees
- Payload: Phishing
- Technique: Impersonation
Overview of the Calendar Invite Phishing Attack
Email Attack: This attack impersonates a Wells Fargo Security Team member, stating that the user has been sent a new security key to protect their account. The body of the message urges the user to open the attachment and follow the instructions or risk having their account suspended.
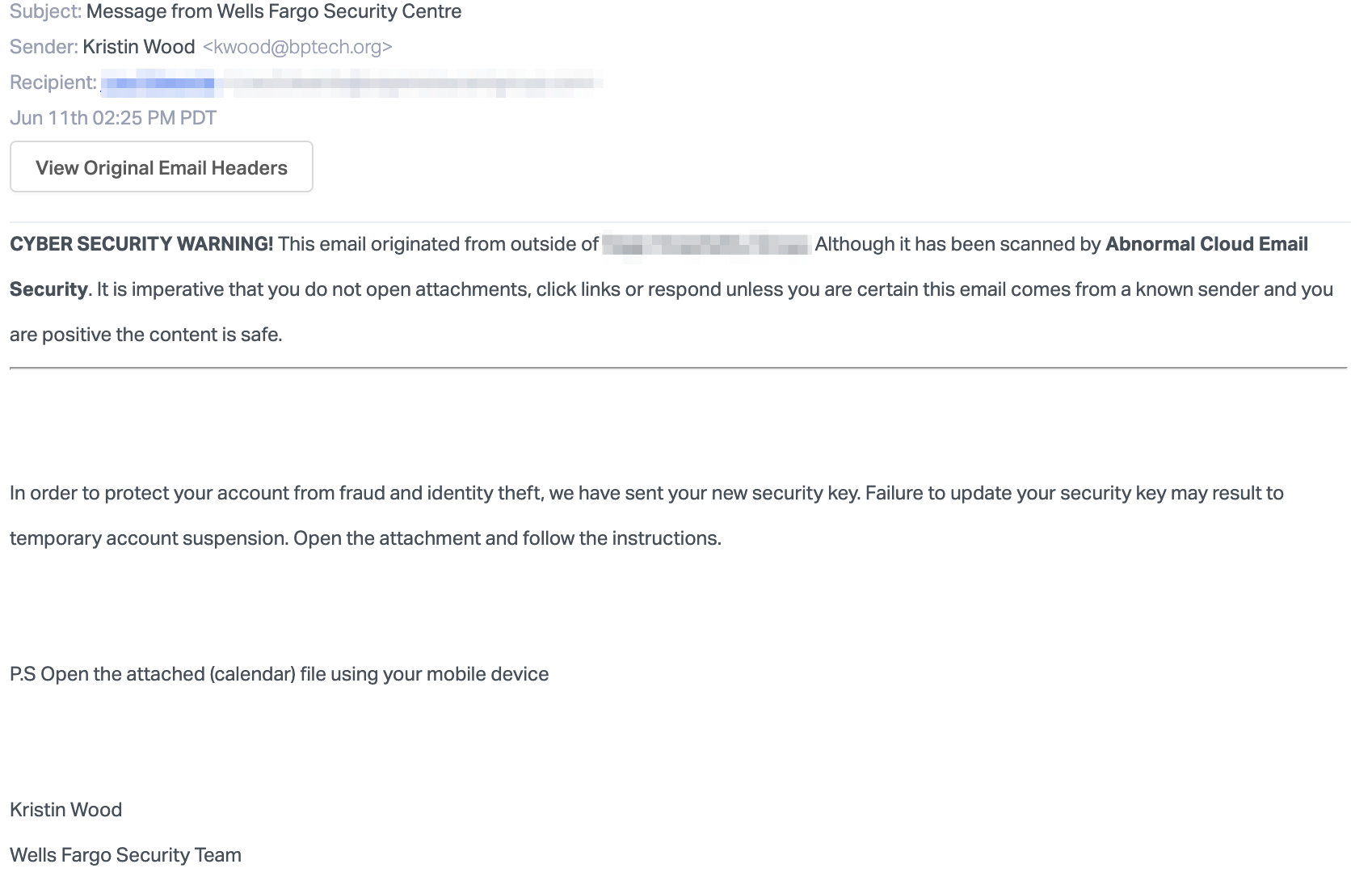
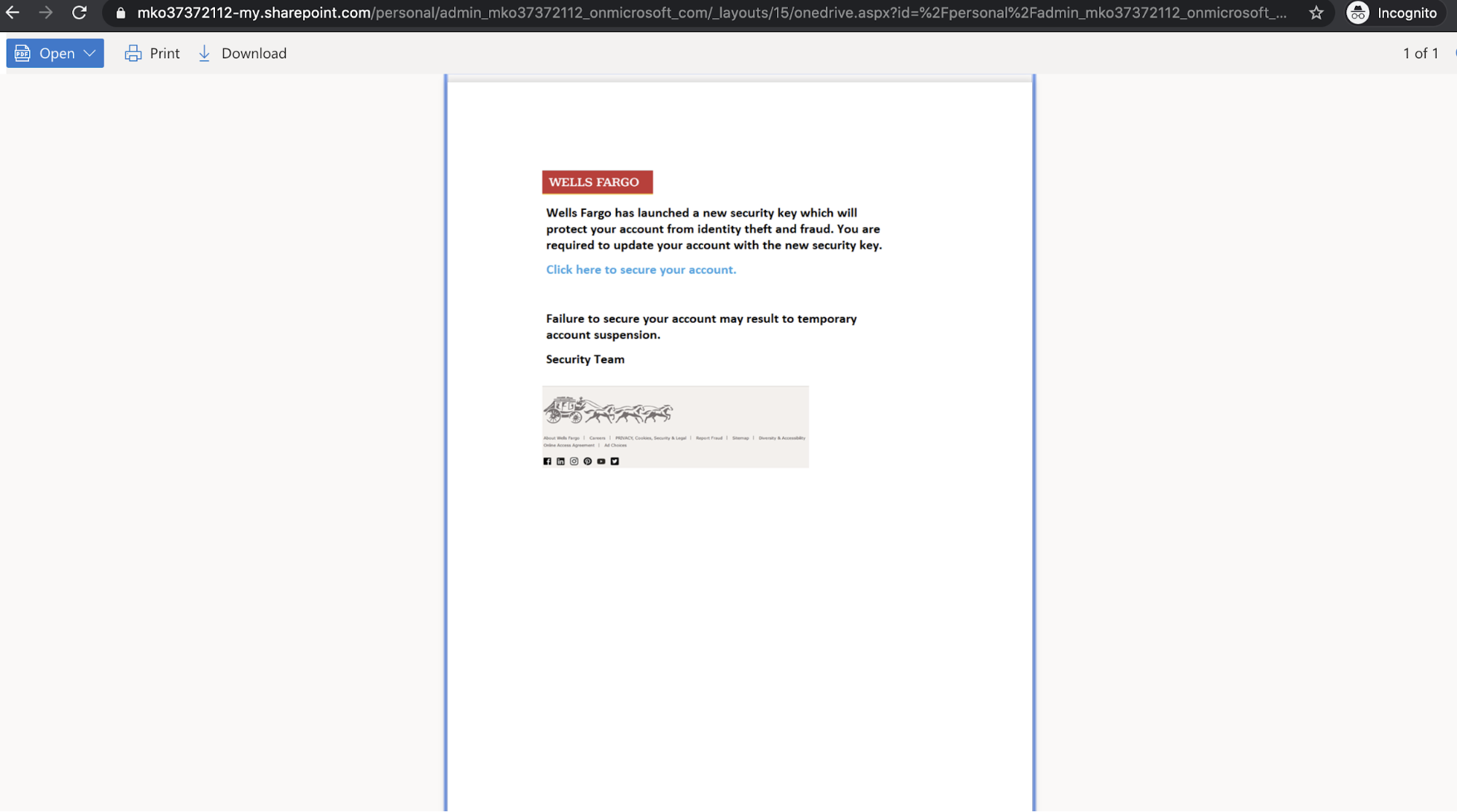
Interestingly, the attackers point out that the attachment in the message is an ICS file, utilized by calendar applications to store scheduling information. Contained within the event description is a link to a SharePoint page, which directs the users to click on another link to secure their account.
This link leads to a fake phishing page for Wells Fargo, where users are prompted to enter sensitive information such as their username, password, PIN, and account numbers.
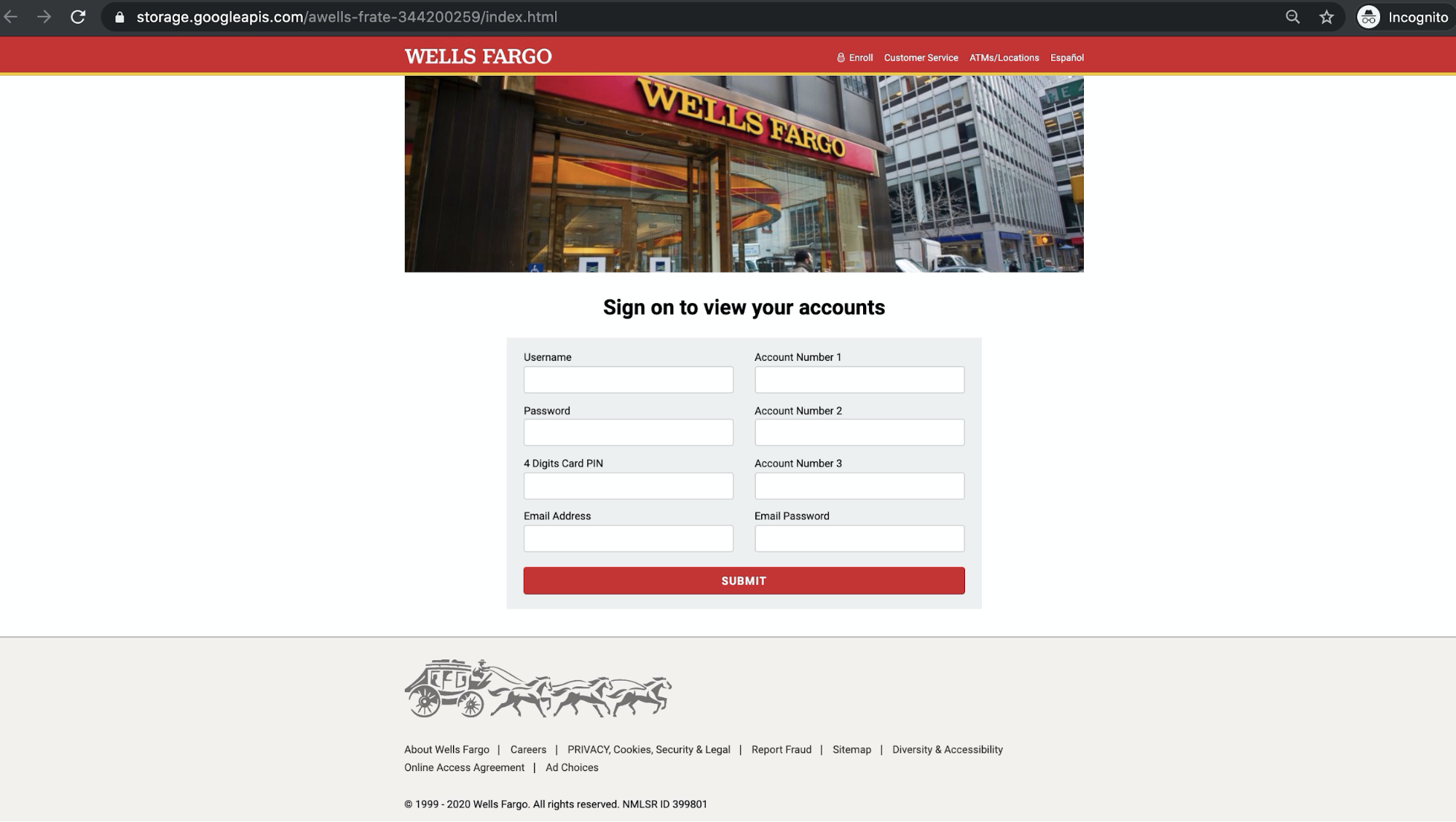
Any credentials and information submitted through the form will be sent directly to the attacker, who can then use this information to take over the victims’ banking details and transfer funds out of their accounts.
Why the Calendar Invite Attack is Effective
The email pretends that the user must update their security key as soon as possible, or risk their account being suspended. It urges the user to quickly open the attachment and follow the instructions. In addition, the malicious link was hidden inside of the description of an ICS calendar invite file, which are often thought of to be benign.
Adding further complications, the message instructs users to open the attached file using their mobile device. Here, the attacker is attempting to exploit a setting where the event will automatically be added to a user’s calendar. Most of these programs will send an automatic notification to the user and attackers hope that potential victims will click on the event and follow the malicious link. As a result, these attacks are more likely to be seen by recipients
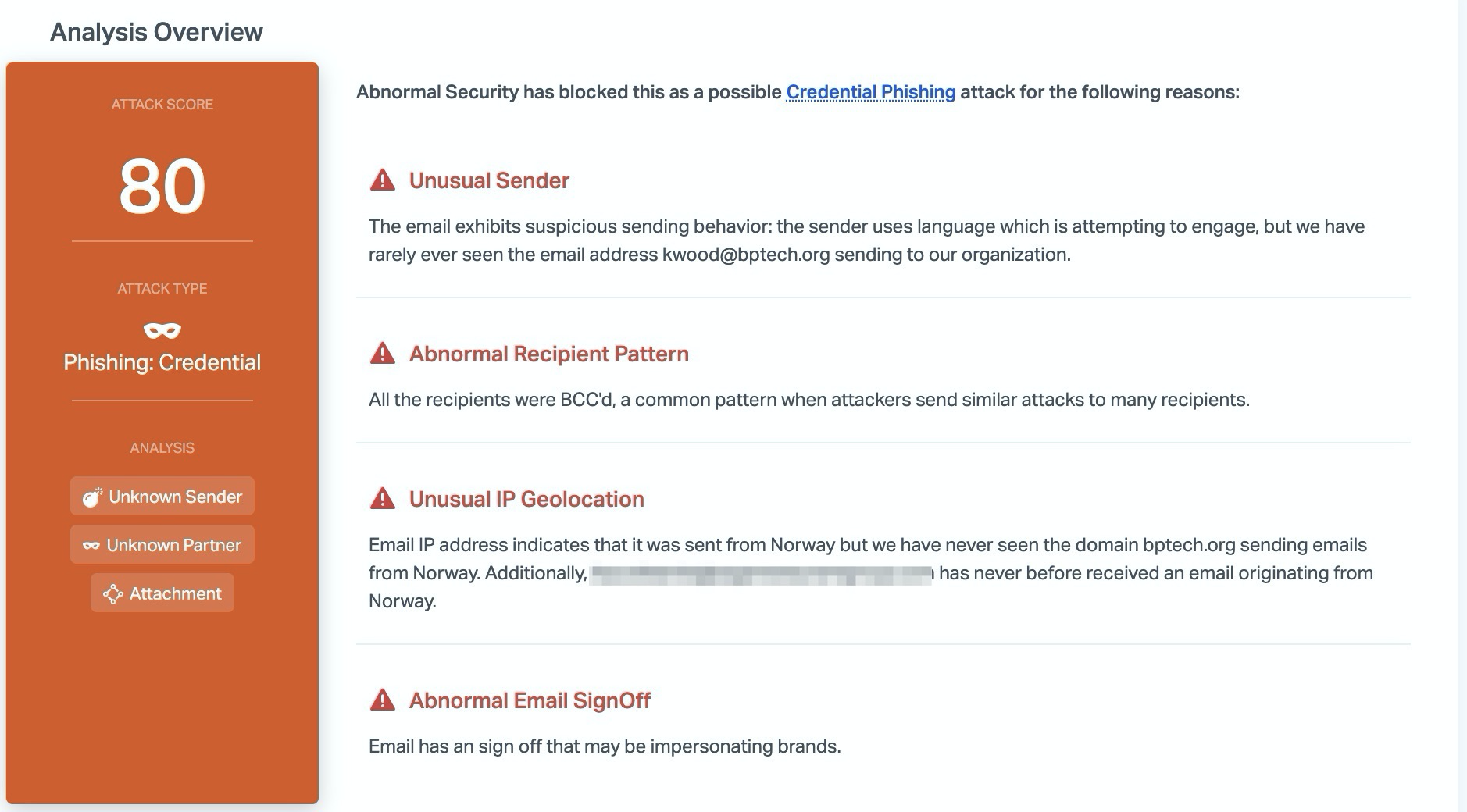
Abnormal stops this attack due to the unusual sender, the unusual IP geolocation, and the abnormal email signoff that indicates that the email is impersonating a brand. Combined with the link pattern and the impersonated landing page, Abnormal can determine that this email is malicious and stops it before hitting inboxes.
To see how to protect your users and your company banking information, schedule a demo of Abnormal today.






