Microsoft Teams Impersonated in Office 365 Phishing Attack
Attackers often impersonate well-known brands, and Microsoft is typically one of the most impersonated, given that access to any Microsoft account opens the possibility of accessing ongoing email threats, sensitive documents, and other Microsoft programs. In addition, Microsoft Teams has seen a massive increase in users as a result of the shift to remote work given the ongoing COVID-19 pandemic. In a recent attack, the chat platform was impersonated in a credential phishing attack, attempting to steal Office 365 login credentials.
Summary of Attack
- Platform: Microsoft Office 365
- Victims: Employees
- Payload: Malicious Link
- Technique: Impersonation Email
About the Microsoft Teams Impersonation Attack
Since the onset of the COVID-19 outbreak and the shift to remote work, there has been a remarkable increase in the usage of collaboration software. This particular attack impersonates Microsoft Teams—one of the leading collaboration software tools in widespread use.
These attackers crafted convincing emails that impersonate automated notification emails from Microsoft Teams. The landing pages that host both attacks look identical to the real web pages, and the imagery used is copied from actual notifications and emails from this provider.
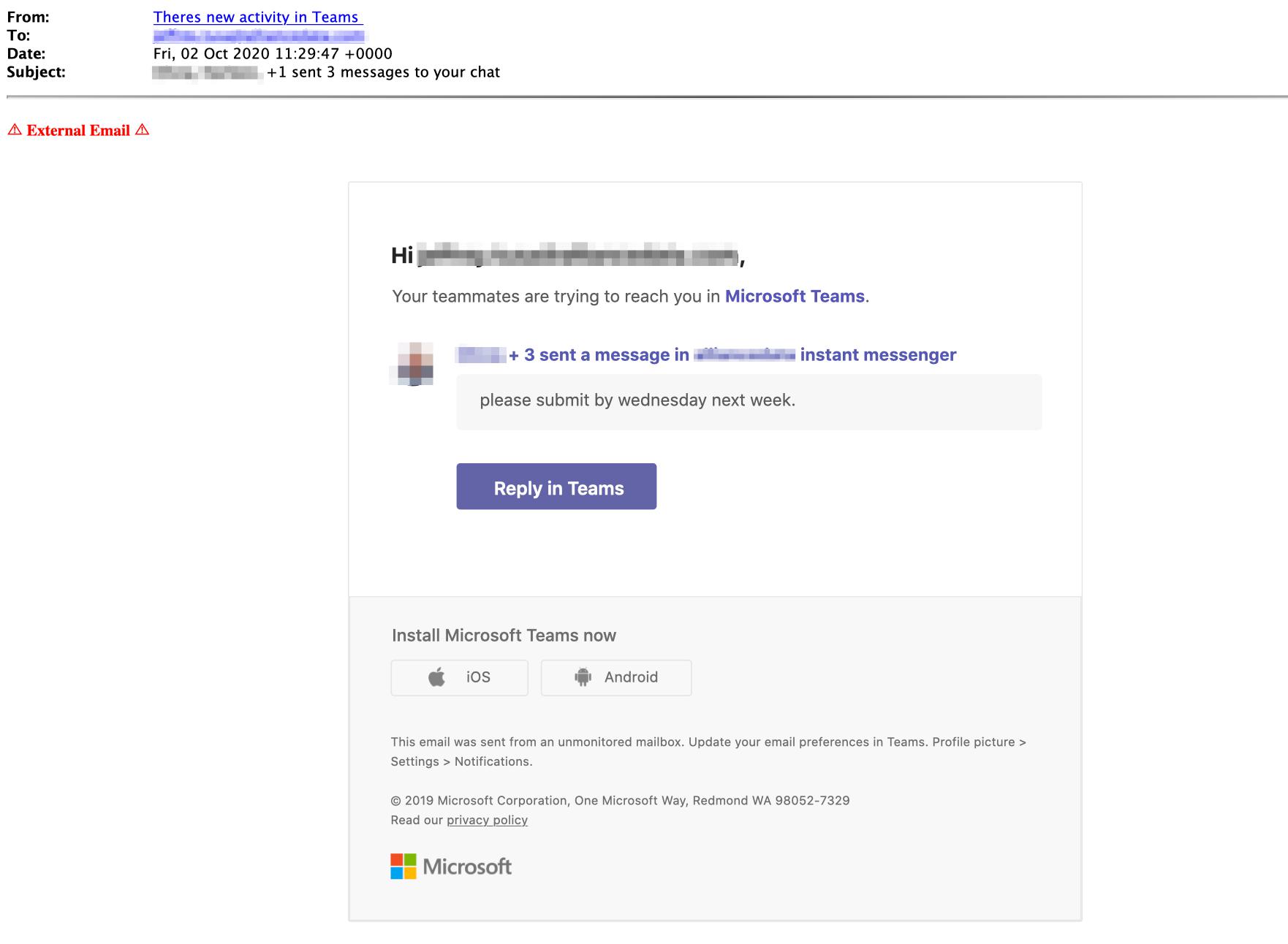
Within the email, attackers utilize numerous URL redirects in order to conceal the real URL that hosts the attack. This tactic is employed in an attempt to bypass malicious link detection used by legacy email protection services. After clicking on a link, there is an image urging the recipient to log in to Microsoft Teams. Once the user clicks this image, the URL takes the recipient to a compromised page which impersonates the Microsoft Office login page.
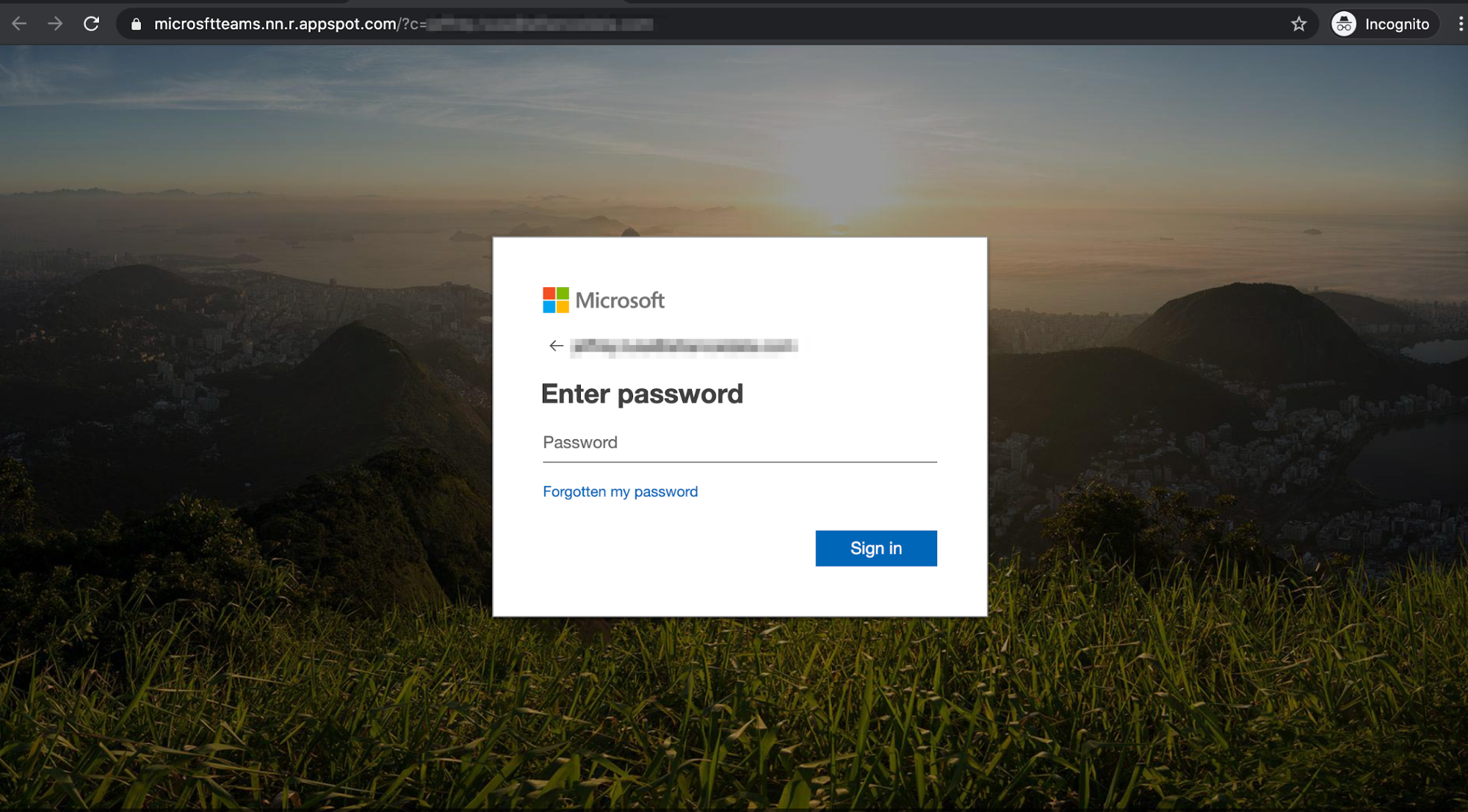
In a separate attack impersonating Microsoft Teams, the sender email originates from a recently registered domain, “sharepointonline-irs.com”, which is not associated with either Microsoft or the IRS. The URL redirect is hosted on YouTube, then redirected twice to the final webpage, which hosts another phishing credentials site mimicking the Microsoft login page.

Should the recipient fall victim to either of these attacks, their Microsoft credentials would be compromised. Since Microsoft Teams is linked to Microsoft Office 365, the attacker may have access to other information available with the user’s Microsoft credentials via single-sign-on.
Why the Microsoft Teams Attack is Effective
The emails impersonating Microsoft Teams and the landing pages the attackers created were all extremely convincing. The webpages and the links within the email are visually identical to legitimate Microsoft Teams and Microsoft login pages, so recipients would be hard-pressed to understand that these sites were set up to misdirect and deceive them to steal their credentials
Furthermore, given the current situation, people have become accustomed to notifications and invitations from collaboration software providers. Because of this, recipients might not look further to investigate the message.
Curious how Abnormal Security stops these and other brand impersonation attacks? Request a demo to learn more.






