Ledger Impersonated in Cryptocurrency Scam
Cybercriminals are desperate to obtain recovery phrases of cryptocurrency wallet users, as those phrases allow them to gain access to peoples' sensitive information and crypto assets. In this attack, malicious actors impersonate Ledger—a hardware wallet that stores users' private keys to cryptocurrency—to steal the security phrases needed to access the virtual currency.
Summary of Attack Target
- Platform: Office 355
- Email Security Bypassed: Proofpoint
- Payload: Malicious Link
- Technique: Brand Impersonation
Overview of the Cryptocurrency Attack
This attacker impersonates Ledger, a company that develops security and infrastructure solutions for cryptocurrencies and blockchain applications, by sending a convincing email that mimics Ledger’s security notification email. The email masquerades as a new device sign-in alert, states that a new sign-in has occurred from Ukraine, and contains a list of details, including an address, user agent details, and browser. The email then urges the recipient to visit the link to cancel the device authorization.
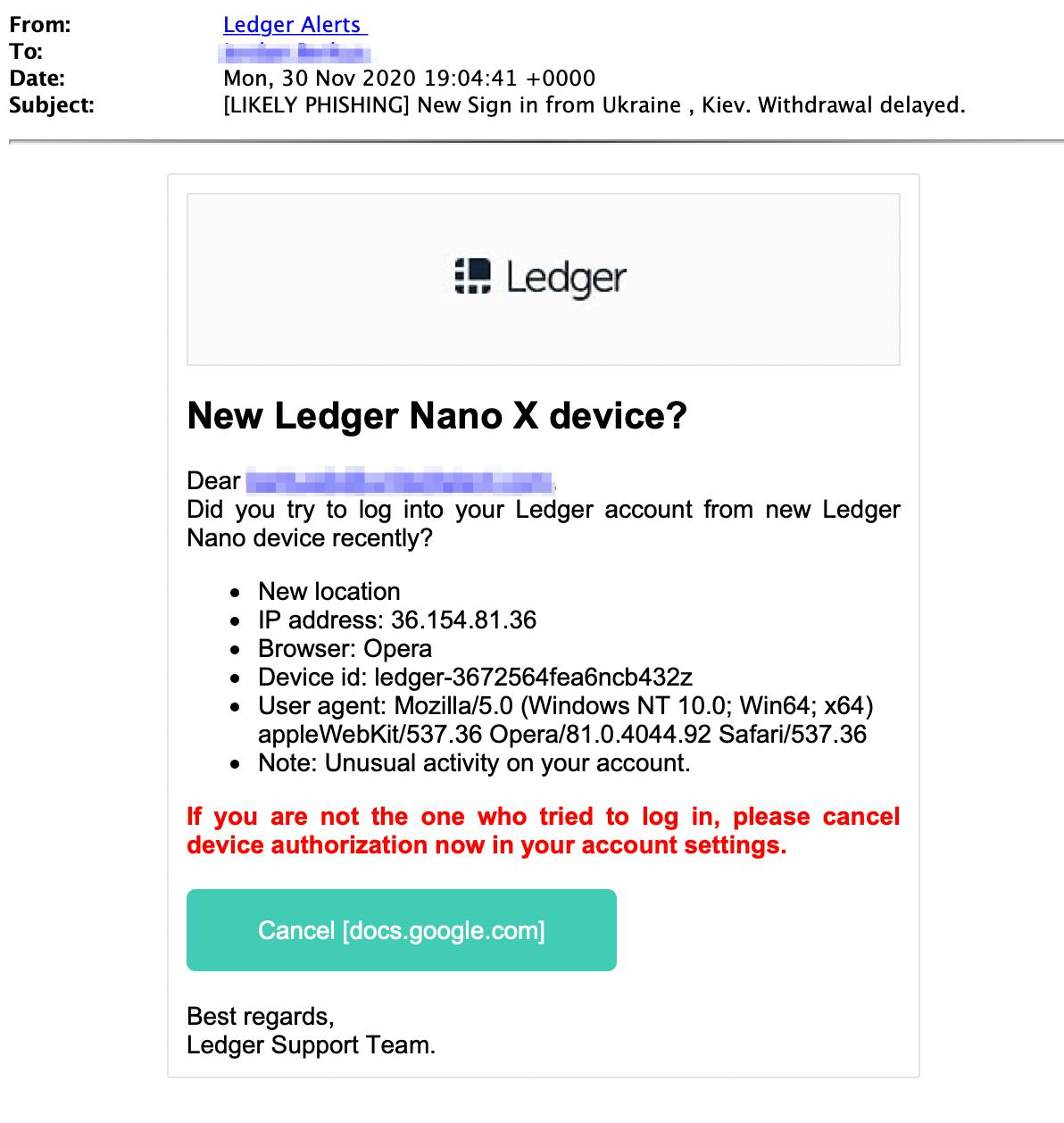
The email contains a link that takes the recipient to a Google Doc, which says that they are being sent to www.ledger.com. When the recipient clicks on the link, they get redirected to a fake phishing page that looks like the legitimate Ledger website.
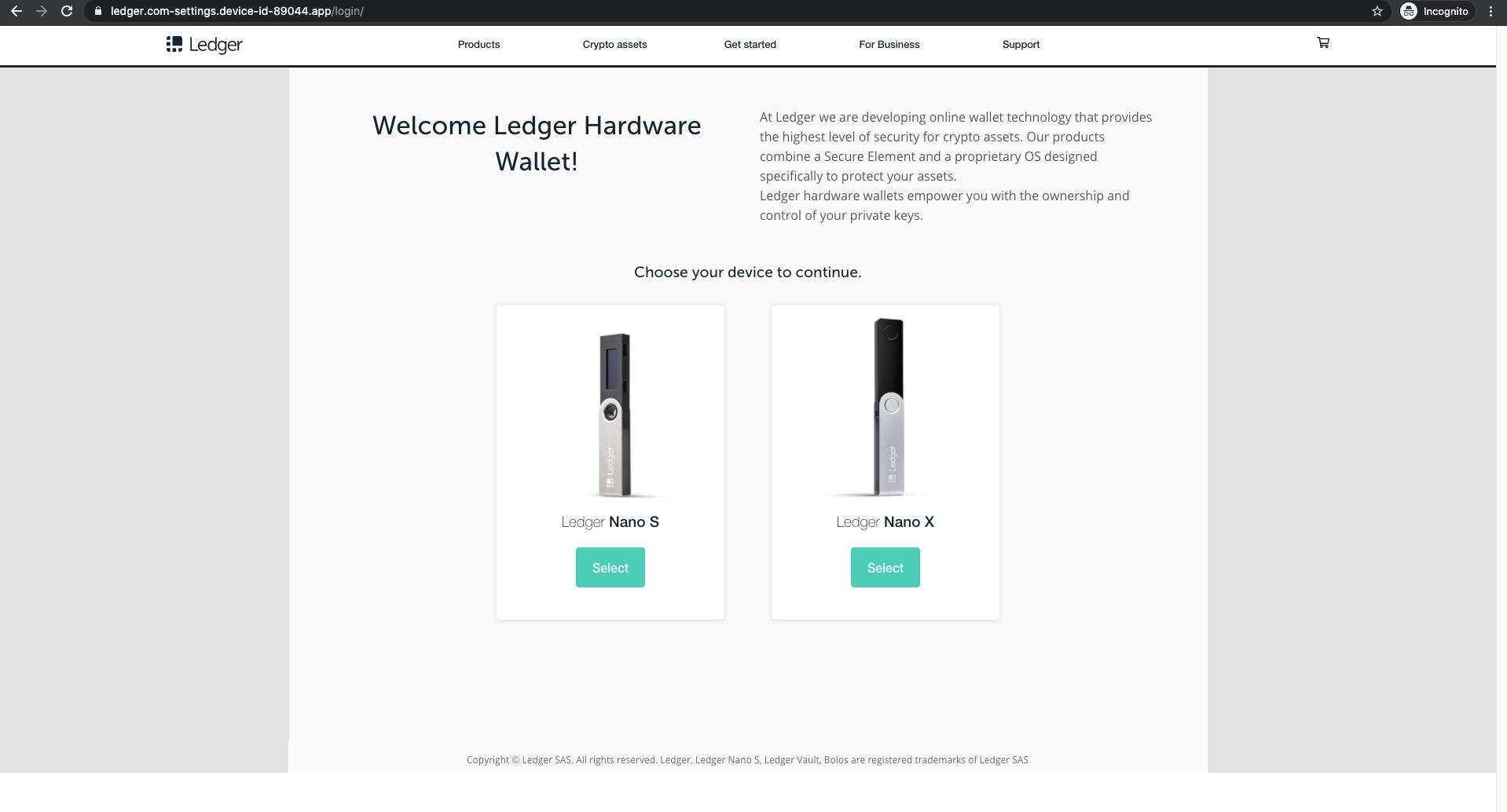
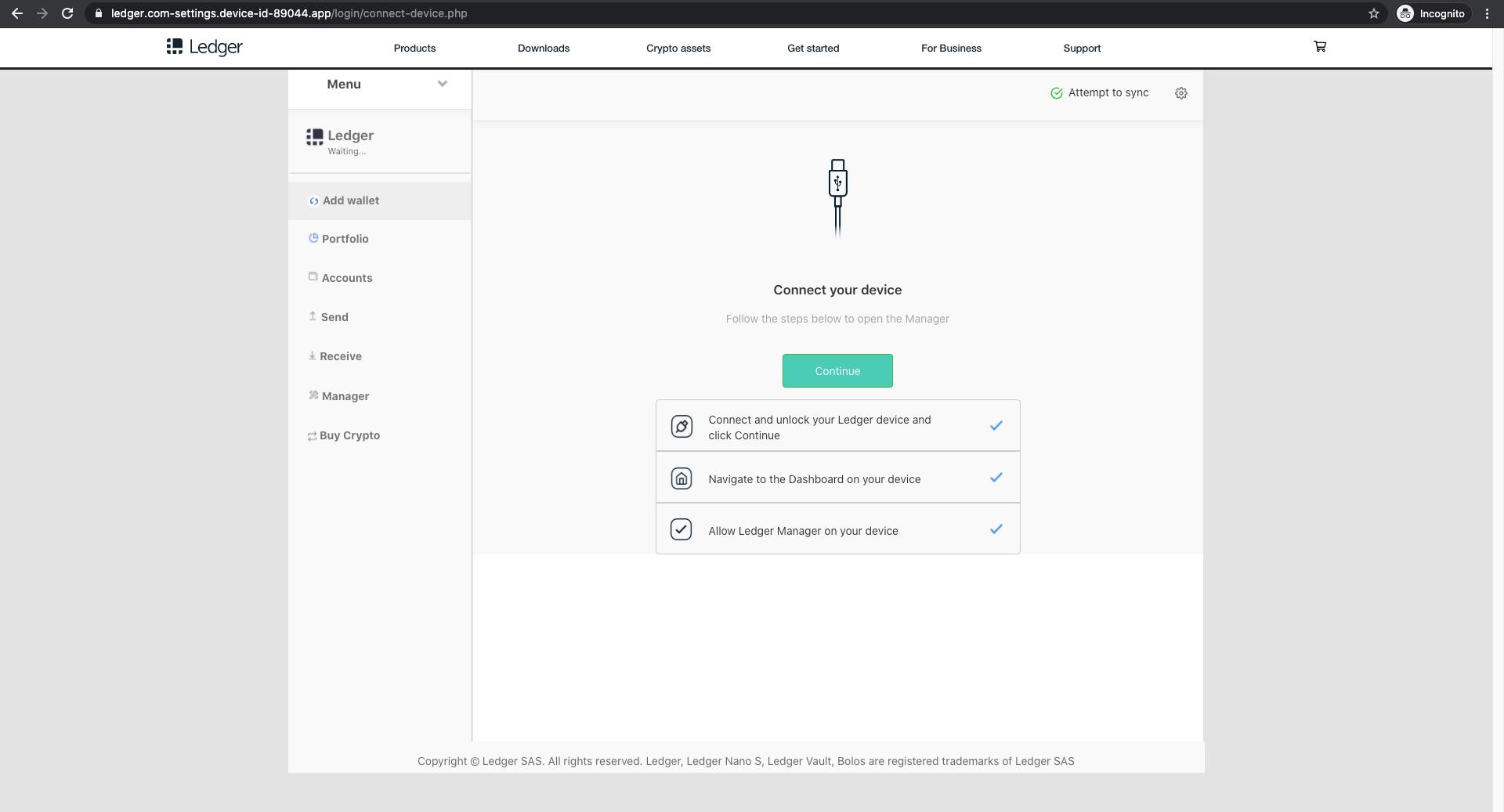
The attacker attempts to fool the recipient by putting “ledger.com” in the URL, but the domain of this fake site, “device-id-89044.app”, has no relation to Ledger. The site then asks the recipient to choose their device to continue. Once the device is selected, it shows a secure connection loading page, then instructs the user to connect their device and click continue.
Upon hitting the continue button, the phishing site asks for the user's recovery phrase as the result of a fake error.
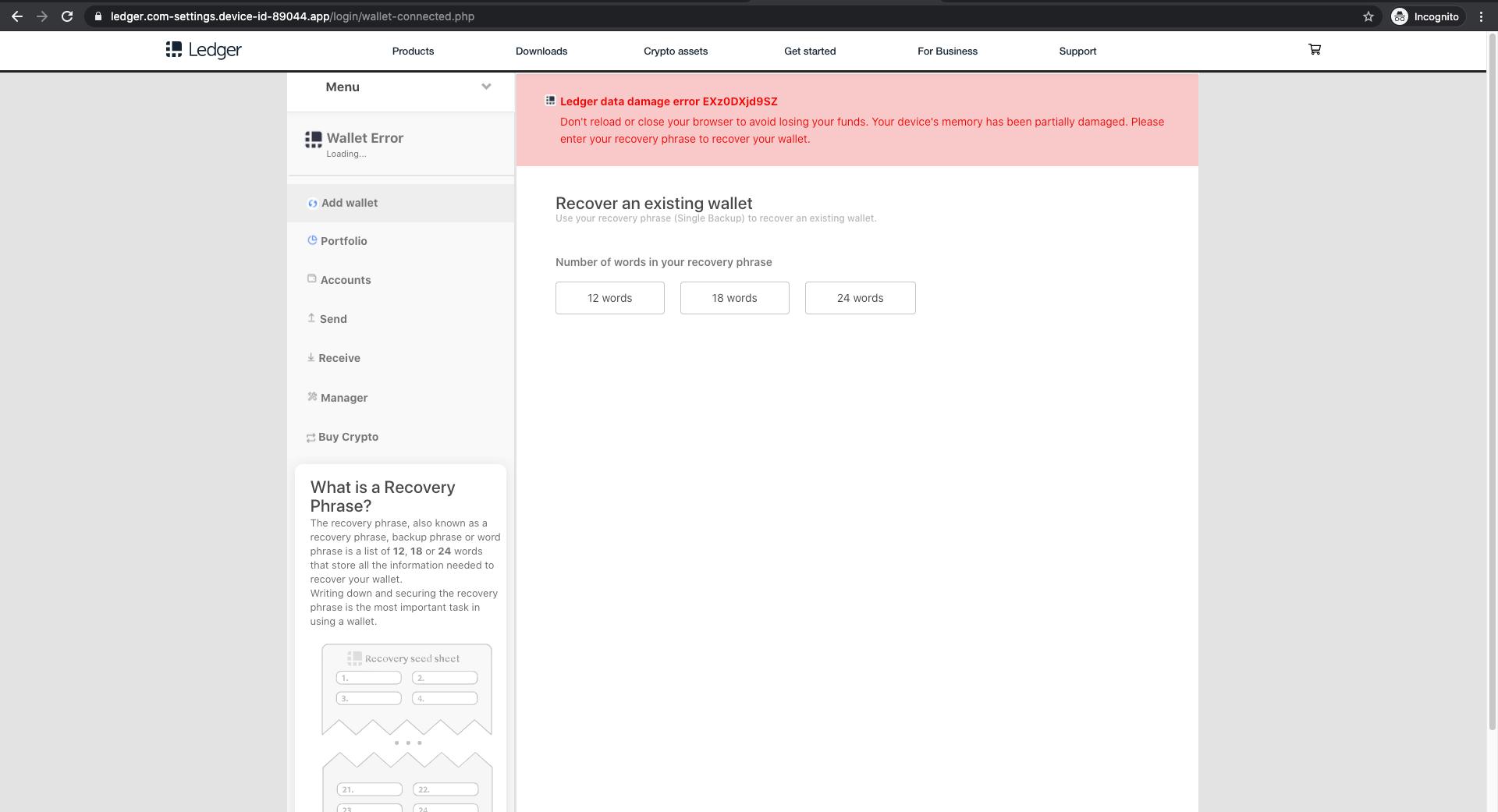
If the recipient does fall subject to this attack and inputs their recovery phrase, which is a vital piece of information to any hardware wallet user, the attacker will have access to all the information on the victim’s Ledger hardware wallet and access to all of their crypto assets. From there, the attacker can spend or transfer them immediately.
Why the Cryptocurrency Attack is Effective
An unauthorized sign-in notification is often disconcerting and people are quick to jump on it, especially if the account is associated with their assets. This email attack utilizes this notification method and motivates the recipient to stop the authorized sign-in by clicking on a malicious link as quickly as possible.
In addition, the attacker portrays a sophisticated phishing site that can easily give a false sense of legitimacy to the recipient. The landing page looks exactly the same as the official page of Ledger. The way that the site shows a secure connection loading page, error message, and asks the user to enter their recovery phrase, all look convincing and legitimate.
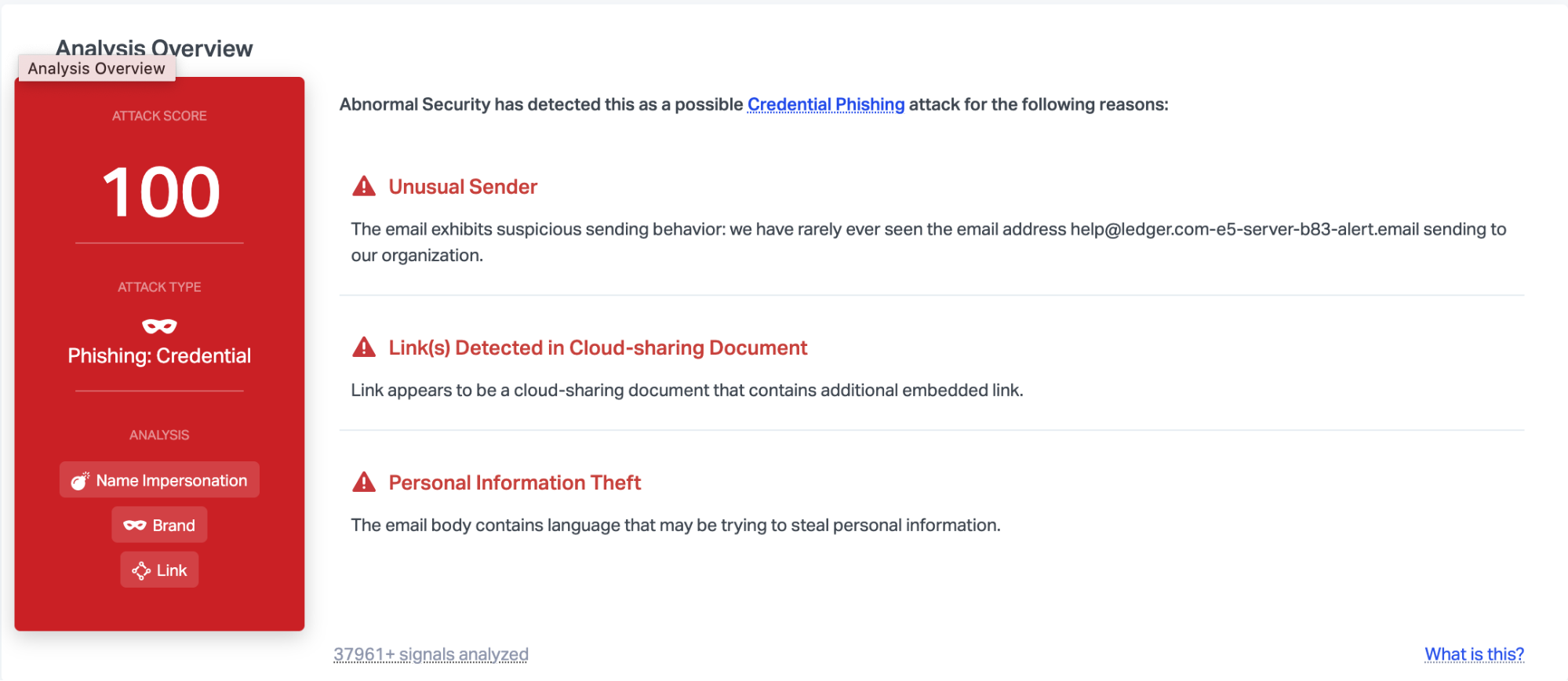
Abnormal is able to detect this attack due to the unusual sender, the links detected in the cloud-sharing document, and the language that indicates that the email may be trying to steal personal information. Combined, these indicators provide enough information to indicate that this email is malicious and as a result, Abnormal stops it immediately.
To learn more about how to protect your email from brand impersonation scams, request a demo of the Abnormal platform today.






