Microsoft Impersonated to Deliver COVID-19 Phishing Attack
In this attack, attackers impersonate a company's Human Resources department and send a COVID-19 scan via a lookalike Microsoft Office 365 email.
Summary of Attack Target
- Platform: Office 365
- Victims: Employees
- Payload: Malicious Link
- Technique: Impersonation
Microsoft Impersonated in Phishing Attack
The original message to the recipient appears to originate from the company’s internal human resources email address. The email looks to be a regular Microsoft O365 notification, notifying the recipient that a document has been shared with them, but the link embedded in the message leads to a phishing site.

The impersonated O365 email contains a document that poses as a PDF regarding a "Covid-19 Report". The email itself includes the Microsoft logo in the footer, increasing the visual legitimacy of this message. The email also states that the file is secure and has been scanned for viruses, which may dupe the recipient into following the link.
When clicking the link in the email, the recipient is presented with a page that appears nearly identical to that of the Microsoft login page and prompted to input their credentials.
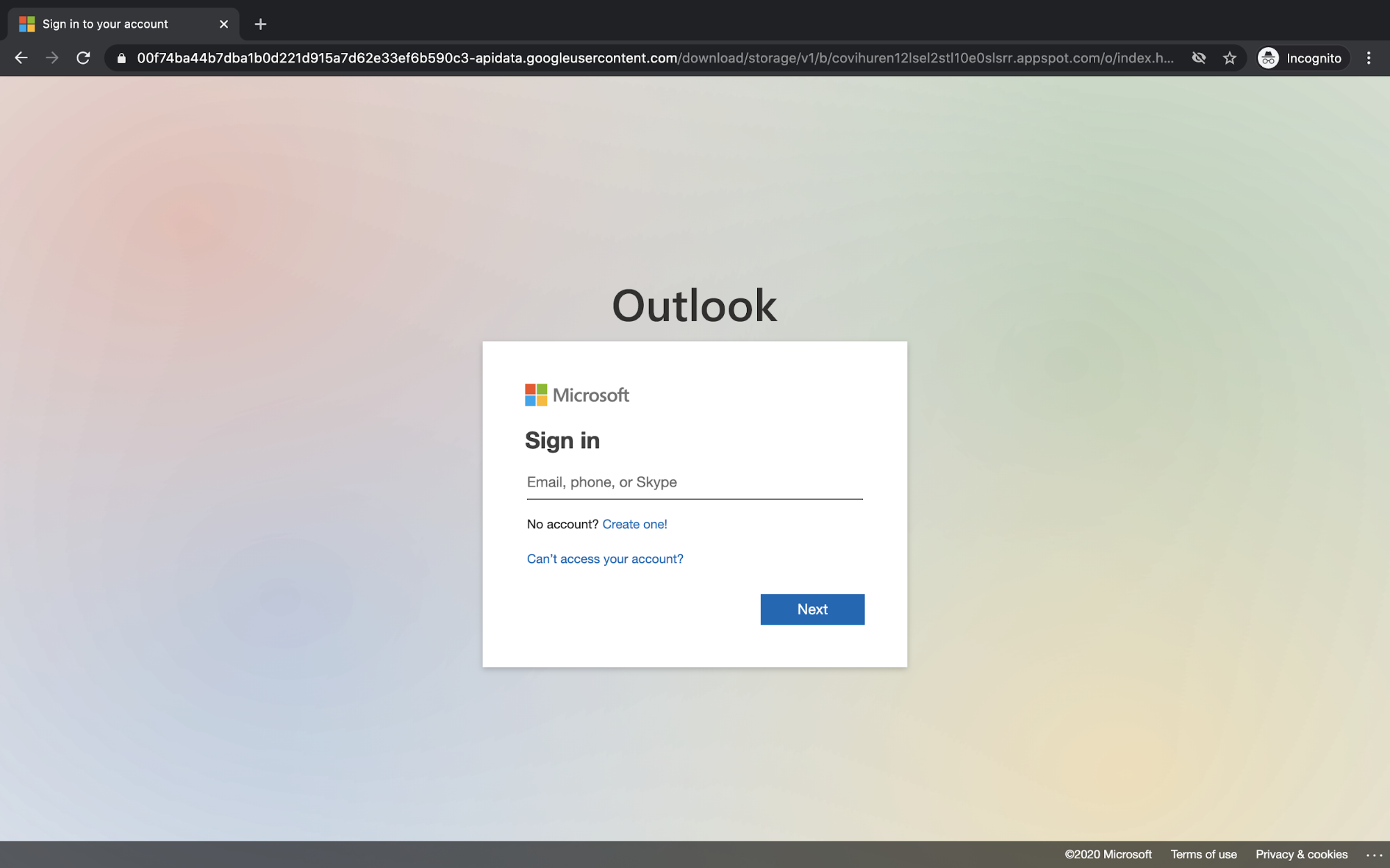
Although this appears to be the legitimate Microsoft login page, the URL 'googleusercontent.com' clearly has no relation to Microsoft. If the recipient were to input their login information to "view the document" that they just received, their credentials would be compromised by the attacker.
Why It Bypassed Existing Security Infrastructure
In this attack, the attackers spoof an internal email domain, which can be challenging to catch, especially if expertly done. The attackers also utilized a trusted brand—Microsoft—to deliver their phishing link, utilizing a very convincing email template and login screen. And because the Microsoft email leads to a Microsoft site, the attack relies on users simply inputting their password in order to see the COVID-19 report.
Abnormal Security prevented this attack by analyzing various attack signals that flagged this email as malicious. Key indicators were the impersonation of a known brand, the presence of a suspicious link, and a mismatch between the sender domain and the display name.
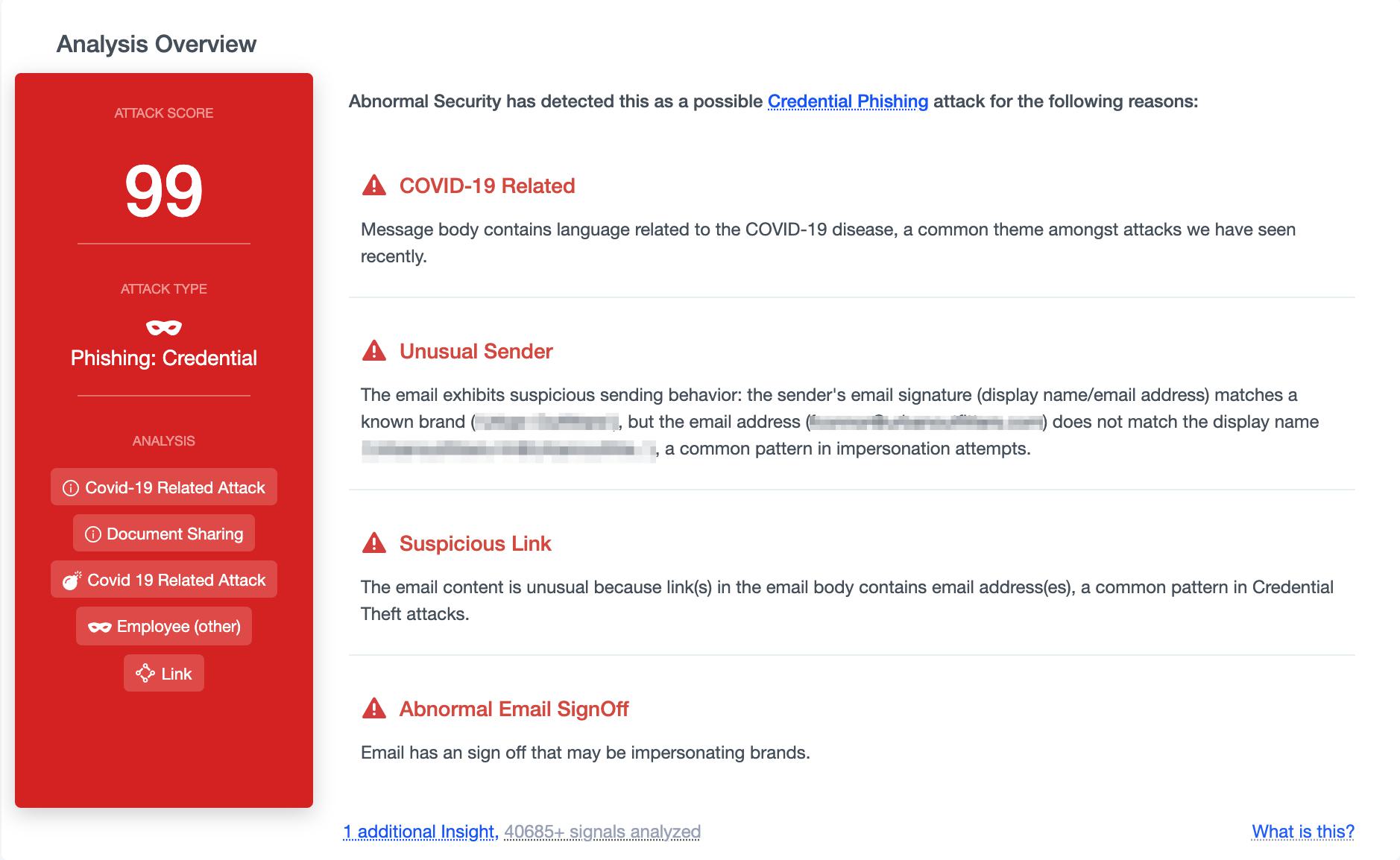
These signals, combined with a dramatic increase in COVID-19 phishing attacks, work together to inform us that this message is malicious. As a result, this message is blocked from inboxes before it can lead to compromised employee accounts.
Discover how Abnormal Security can stop brand impersonations and credential phishing emails for your organizations. Get started by requesting a short demo.






