Bitcoin Requested in New Extortion Scam
Recently, there has been a rise in scam emails demanding recipients to pay a ransom with bitcoin, or else the personal information attackers have gathered about the recipient will be released to the public. The means by which attackers have obtained this information has evolved, as has the amount of BTC that is requested.
One thing that remains the same, however, is the goal of these scams: utilize high-pressure intimidation tactics to extort victims into paying attackers to remain silent about the information they do not have.
In this attack, attackers extort recipients for a bitcoin transfer in exchange for not revealing personal information that they claim to have stolen in a hack.
Summary of Attack Target
- Platform: Office 365
- Email Security Bypassed: Office 365
- Victims: Employees
- Payload: Text
- Technique: Extortion
Overview of the Bitcoin Extortion Attack
This attack features an email that seemingly originates from a brand that services electrical contracts, but is actually a spoofed domain. The attacker begins by claiming they are a private investigator, that they are a part of an agency that compromises accounts, and they have discovered a plot to blackmail the recipient. However, they are not specific on what this plot is.
The email continues, claiming that they have negotiated a price with the agency they are working with and decided to give the recipient a discount, to be paid in bitcoin, in exchange for deleting the evidence that could damage the recipient's reputation and career. If the recipient chooses to ignore the warning, the attackers threaten to release the information.
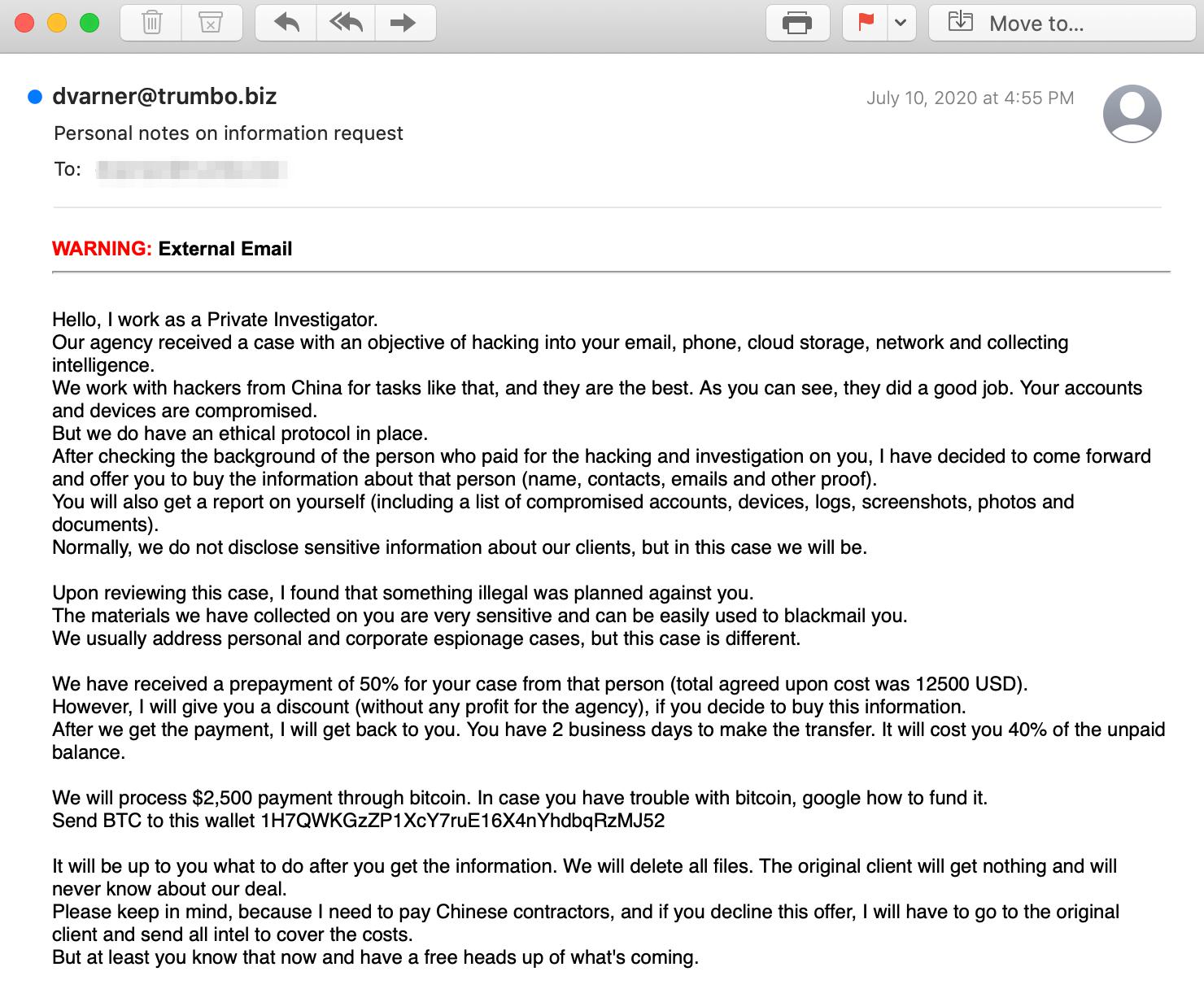
The payload of this attack is provided in the body of the email. The instructions are provided for the recipient to send BTC to a specific wallet address. In the event the recipients are unclear on how to send funds to the wallet, they are instructed to "google" how to do it. If the recipients should fall victim to this BTC scam, they are will incur a financial loss of $2,500.
Why the Bitcoin Extortion Scam is Successful
The letter uses extortive tactics to demand action from the recipient, who is coerced into paying $2,500 to the attacker through a bitcoin wallet within two days. By ensuring that any and all information the attackers have obtained will be deleted, it provides a strong incentive for victims to pay attackers the ransom.
In addition, the sender is impersonating a brand ’trumbo.biz’, however, the email authentication fails, indicating the sender is spoofing the domain. By appearing to originate from a company domain, the recipient is given the impression the domain has been “hacked” so that when victims receive the attackers' message, they are more likely to believe the attackers' claims.
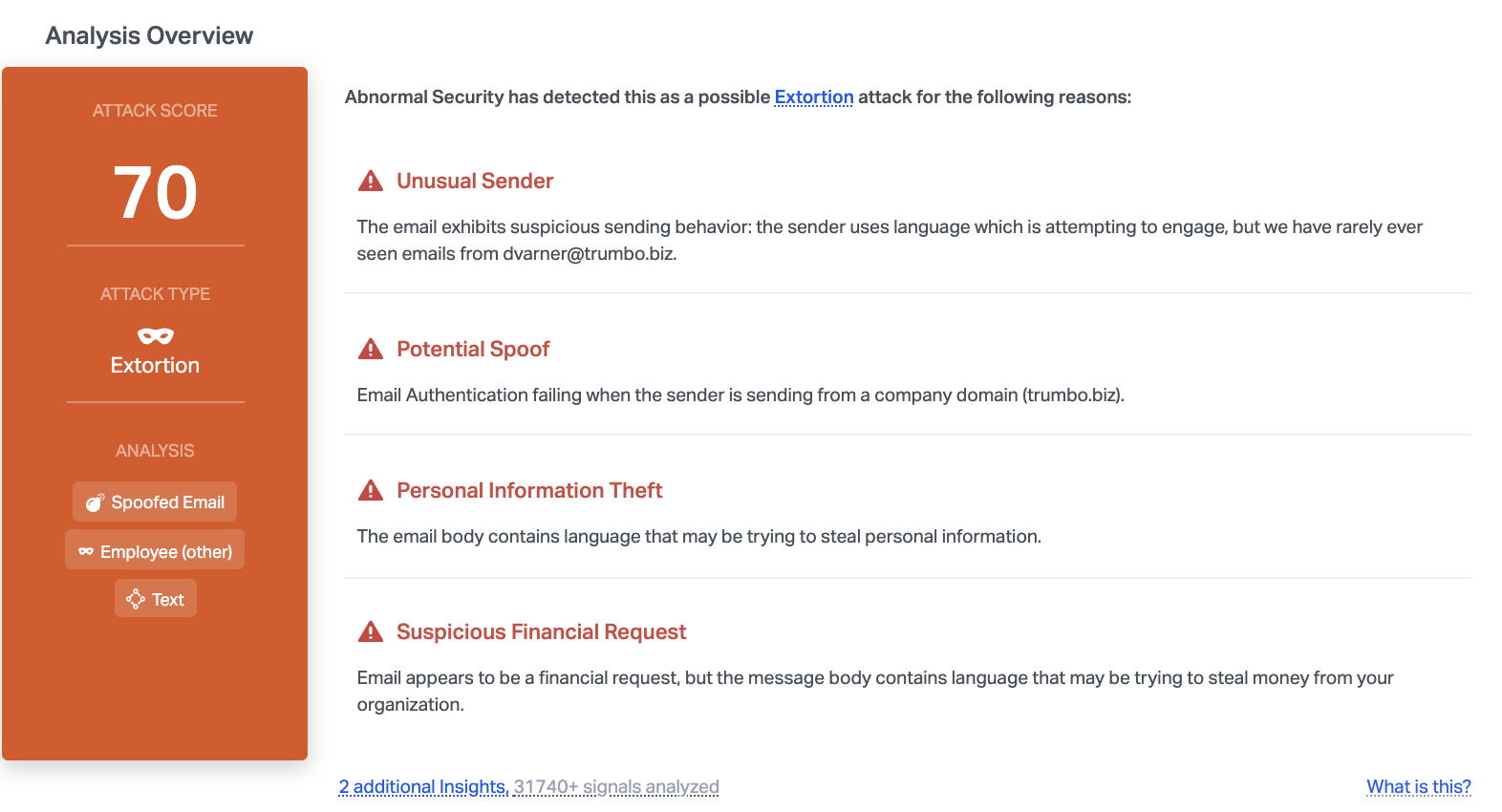
Abnormal stopped this email due to the unusual sender, spoofed email address, and the financial request. By understanding the intent of this email, we can understand that this is an extortion scheme that may be trying to steal information or money.
To learn more about how to protect your employees from extortion, see a demo of the Abnormal platform today.






