Attackers Compromise Office 365 Accounts without Stealing Credentials
Credential phishing attacks are not new, and impersonating Microsoft is well-known at this point. However, this attack is unique because the attacker was not simply asking for email credentials. Instead, the attack uses an app integration to gain full access to a Microsoft account, including email conversations, OneDrive files, and more.
Summary of Attack
- Platform: Office 365
- Email Security Bypassed: Office 365
- Victims: Internal Employees
- Payload: Office 365 App
- Technique: Brand Impersonation
Overview of the Phishing Attack
In this attack, the attacker leveraged an Office 365 app which, according to PhishLabs, was created using information stolen from a legitimate organization. This app requests access to nearly everything in the victim's O365 account—email, OneDrive, contacts, and more.
The email itself purports to come from Microsoft, asking users to log in to enable additional anti-virus protection on their account. The email looked like a legitimate email from Microsoft and links directly to legitimate Microsoft pages, including a real Microsoft login page.
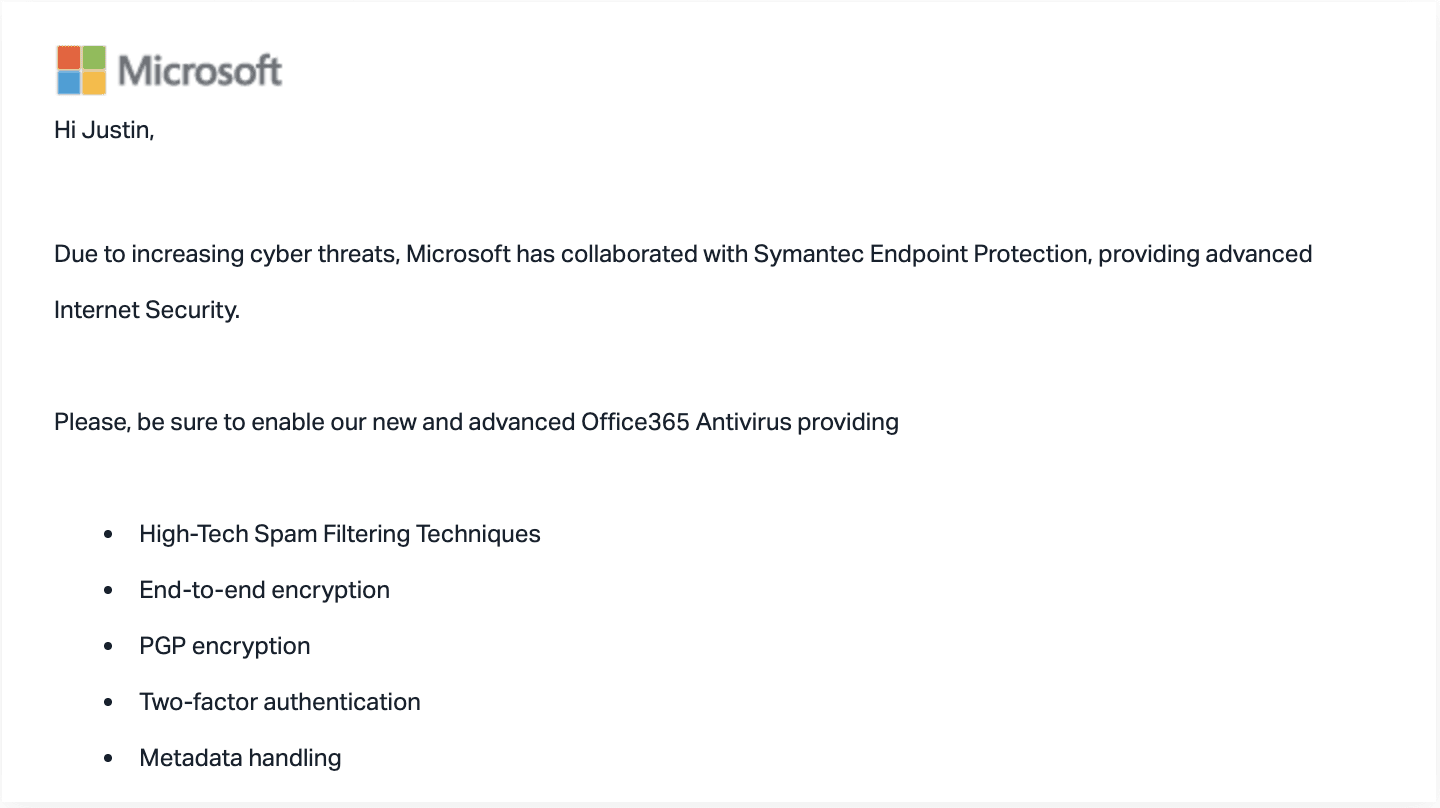
Although the login page the email linked to was a legitimate Microsoft login page, the URL also instructed Microsoft to forward the authorization token to another domain. After the user logged in, this forwarded token would trigger an app to request full access to the victim's Office 365 account. This portion of the URL would not have been easily visible in the browser's address bar.
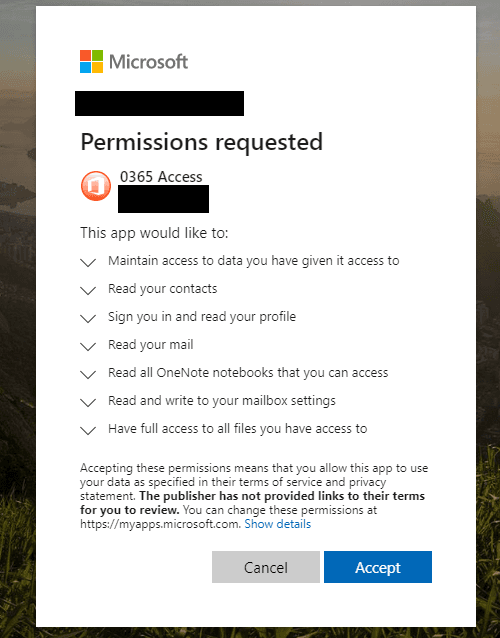
If the user granted the app the access it requested, attackers would take full control of the victim's account. Because access is granted through the malicious app, a password reset would be ineffective—the only way to deny the attacker access to the account would be to delete the app.
Why the Attack Bypassed Existing Security
In this case, the email sent from the attacker looked like a real email from Microsoft and the display name itself said as much. In a unique twist, it offered greater protection for the user's Office 365 account. Nothing about the email, including URLs, looked amiss or illegitimate. Making it even more complicated, the attacker directed the victim to a real Microsoft login page because the point of the attack was not to steal credentials.
The email even said that users would be getting new security capabilities, so they might have even expected the app prompt a full access request to their account. This attack was sophisticated: there was no credential theft since the login page was real, and even if the user realized that this was an attack, changing their password would not block the attacker's access to their account.
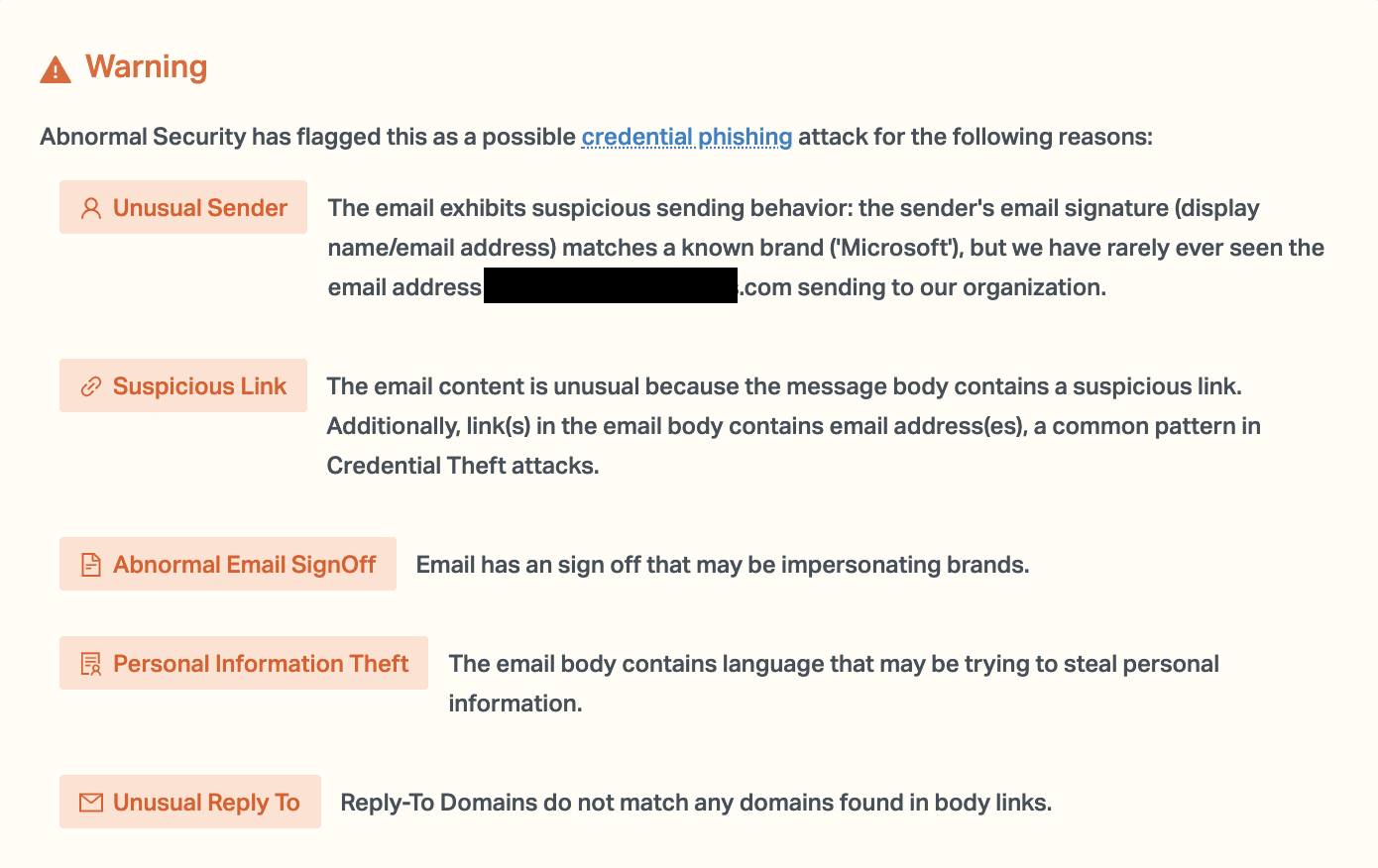
Abnormal stopped this attack because of the unusual sender address, the unusual reply-to domain, and the urgent language present within the email itself. In an attack that is extremely difficult to stop, and where remediation is much harder than simply changing the password, increased security is vital to prevent compromise.
See how Abnormal can prevent these attacks for your organization by requesting a demo today.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

