IRS Impersonated in Identity Theft Scheme
IRS email impersonations are widespread across all industries. These attacks vary in scale and victim, targeting both individuals and companies as a whole. This particular attack follows the growing trend of utilizing social engineering strategies for malicious engagement, allowing attackers to easily bypass email security solutions that focus on link or attachment-based threat vectors.
Summary of Attack Target
- Platform: Office 365
- Victims: Employees
- Payload: Link
- Technique: Impersonation
Overview of the IRS Impersonation Attack
The attacker impersonates the IRS by crafting an automated email informing the applicant that they have been approved for the $1,400 stimulus payment. The email contains a link hidden embedded within the text that reads “Claim your refund now”.
By clicking on the link, the recipient is led to the attacker’s carefully crafted landing page. Here the recipient is prompted to fill out the form, which includes personal information like social security number, date of birth, gross annual income, driver's license number, and electronic filing PIN. With all this information, attackers have everything they need to commit identity fraud. And with an added field of gross annual income, they know which victims likely have the most money to steal.
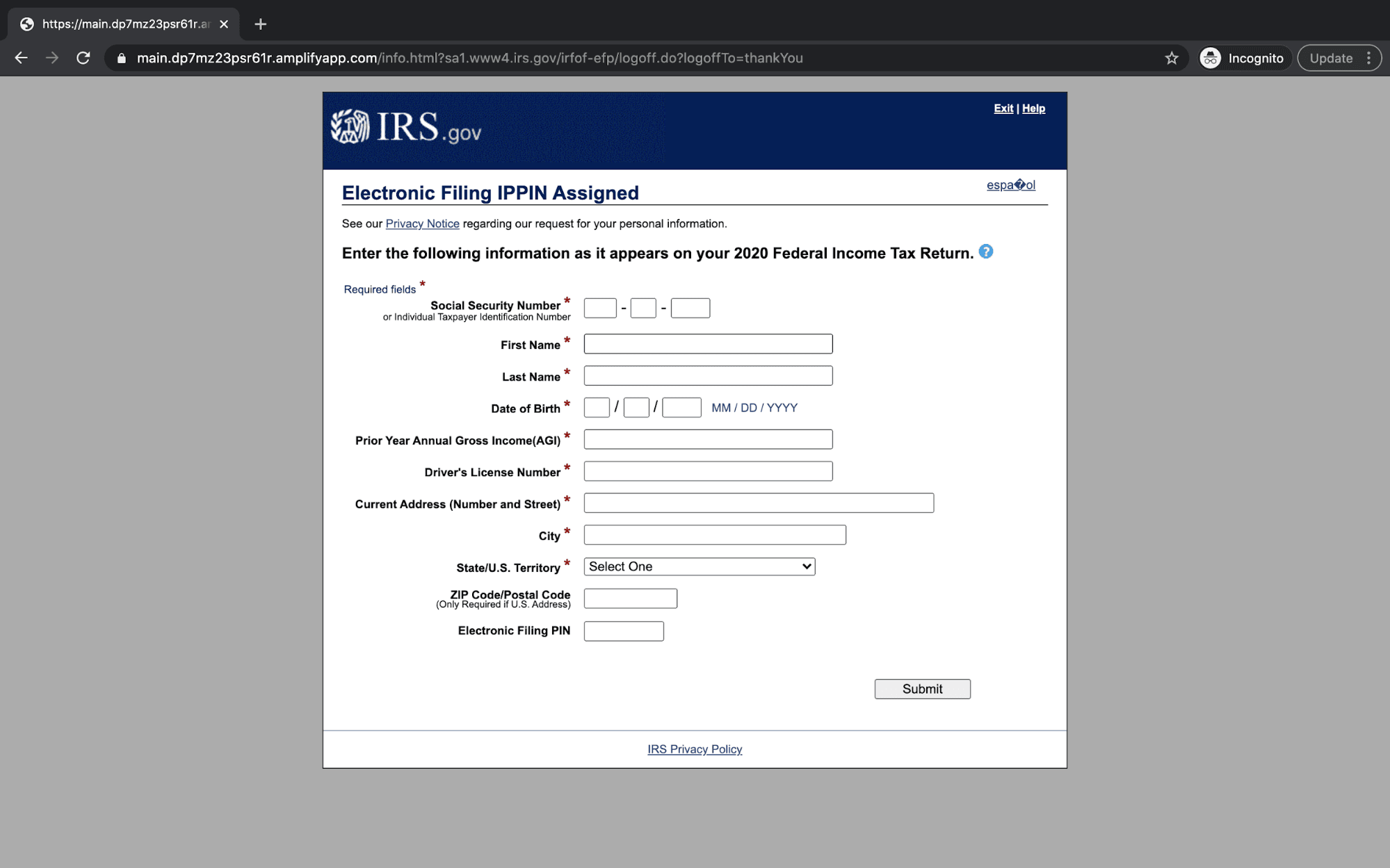
This impersonation is especially convincing as the attacker’s landing page is identical to the IRS website, including the popup alert that states “THIS U.S. GOVERNMENT SYSTEM IS FOR AUTHORIZED USE ONLY,” a statement that also appears on the legitimate IRS website.

The attacker also attempts to conceal the URL in an effort not to alert the recipient that the link leads to a form hosted on an Amazon domain. If the information is added to the form, the attacker can commit identity theft, among other nefarious acts.
Why the IRS Impersonation Attack is Effective
It is likely that this attack bypassed email gateways because the existing gateways only take threat examples from ongoing and current attacks that are in high volume. Phishing attempts that utilize social engineering are much lower in volume, target specific persons, and are able to be hosted on domains that can be quickly taken down.
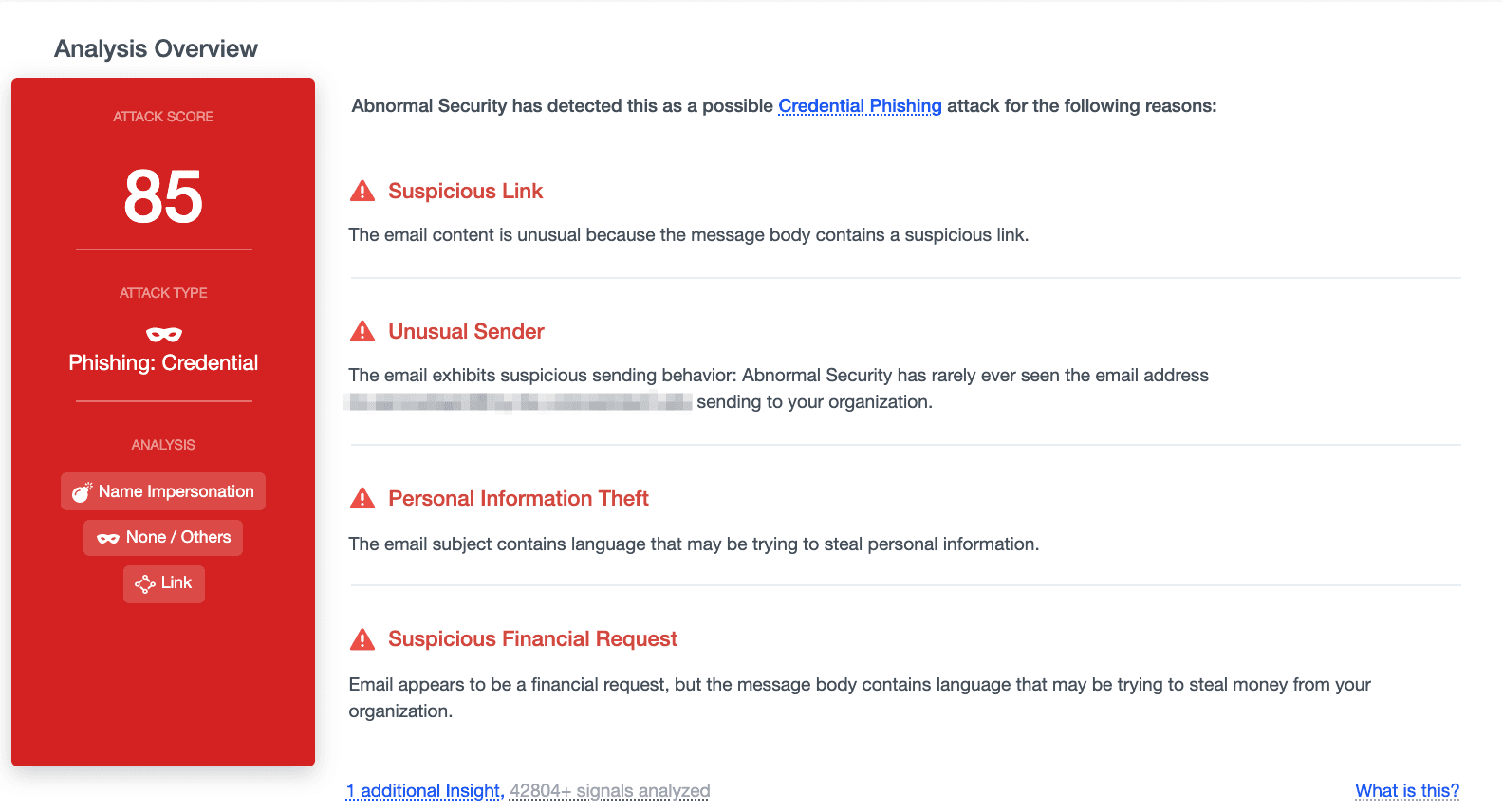
Abnormal was able to detect this attack by analyzing 42,804+ signals and this message received an attack score of 85 for a number of reasons. The first was the suspicious link embedded within the text of the email that led to the phishing page. Another signal was the unusual sender, as this email has never been seen sending to this particular organization. In addition to this, the language of the email was analyzed, and the Abnormal platform found suspicious financial vocabulary indicating a possible attempt to steal money from the recipient. As a result, this message is blocked before reaching end users.
To see how Abnormal can protect your employees from identity theft and other fraud, request a demo today.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

