Microsoft Office 365 Security Alert Spoofed to Steal Credentials
Microsoft provides security alerts in the case of fraudulent logins on user accounts. Users are usually able to trust these emails due to the source being from a trusted brand. And because the email relates to account security, the recipient may unconsciously trust the email solely based on the subject matter.
In this attack, threat actors spoof an internal email from the recipient's company regarding a security alert in order to steal user account credentials.
Summary of Attack Target
- Platform: Office 365
- Email Security Bypassed: Proofpoint
- Payload: Malicious Link
- Technique: Spoofed Email
Overview of the Microsoft Alert Spoof
This email impersonates a security notification email for the recipient's Microsoft accounts, ostensibly from the company's email security team. The message claims that there was a suspicious sign-in attempt, and the user should review their account activity via the link provided.
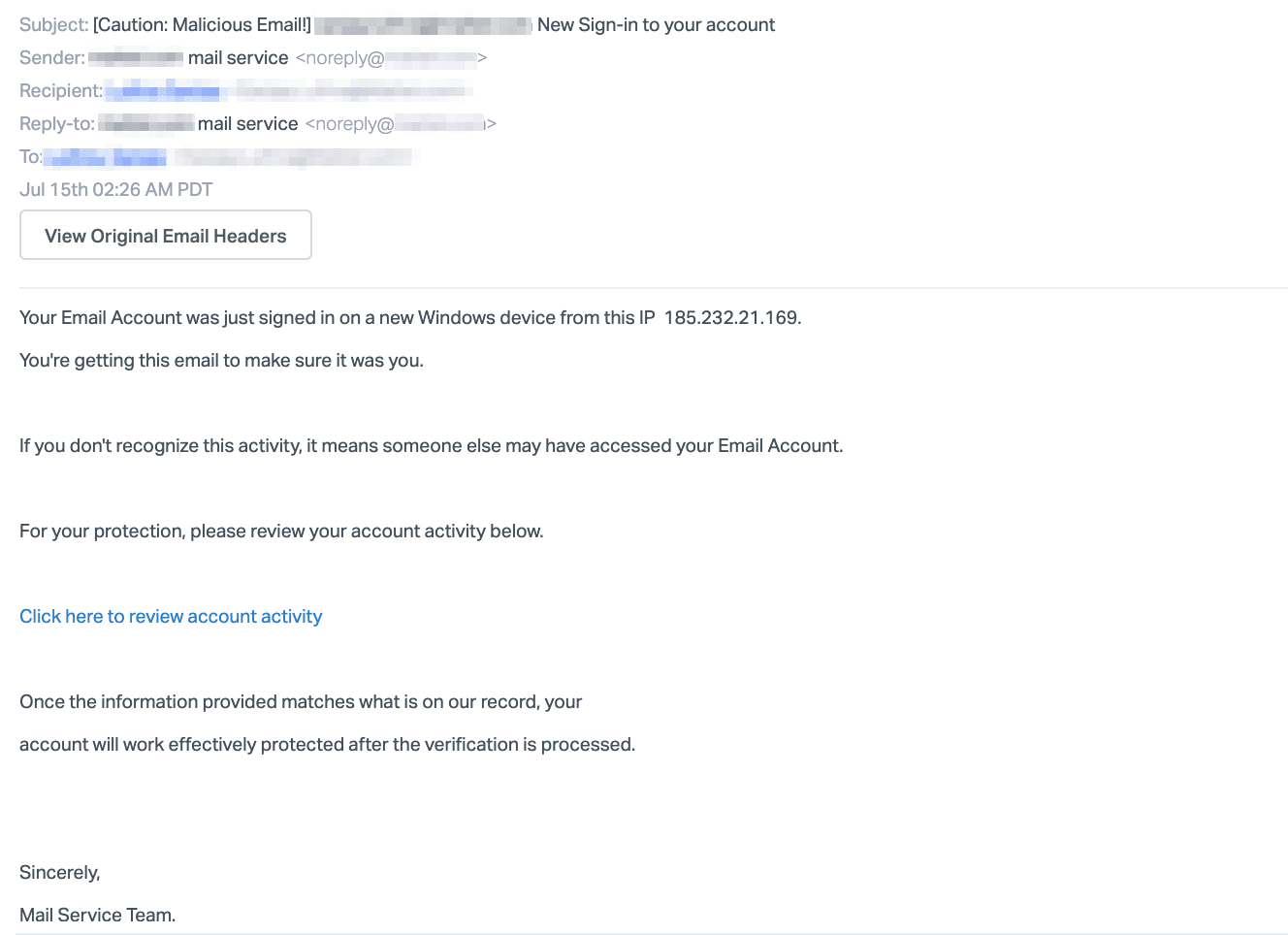
However, instead of directing the recipient to the sign-in activity page, the links sends the target to what appears to be a Microsoft login page hosted on a site likely controlled by the attackers. The recipient's professional email is already input, so all the recipient has to do is enter their password.

With fewer steps required to enter account credentials, it's more likely the recipient will fall for the attack. If they do so, the attacker can utilize this information to compromise the recipient's email account, as well as all other Microsoft applications associated with it including SharePoint, OneDrive, and Teams.
Why the Microsoft Alert Spoof is Effective
The email presents itself as a security notification, claiming there may be a suspicious login from the recipient's account. This type of notification is more likely to cause a recipient to act quickly and overlook any red flags. Thus, the recipient may not realize that both the message and the link are fraudulent.
In addition, the attacker has successfully spoofed the email domain of the recipient's company. This means that the recipient is less likely to realize that the message is malicious, as they will believe it has originated from a safe, internal source. The landing page for this attack also directly impersonates the official Microsoft login page and includes their email address—adding to the credibility of the page.

Abnormal stops this credential phishing attack due to the spoofed email address, the suspicious link, and the fact that the sender is attempting to impersonate an administrator within the company. Combined with the language that indicates personal information theft, we can determine that this email is malicious and block it before it reaches user inboxes.
To discover more about how Abnormal protect you from credential phishing attacks, request a demo today.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

