Navy Federal Credit Union Members Targeted in Phishing Attack
As individuals worldwide struggle with the financial burdens caused by the COVID-19 pandemic, cybercriminals are taking advantage. In a recent attack uncovered by Abnormal, attackers impersonate the US Navy Federal Credit Union in order to steal victims' banking credentials. Once the credentials are placed into the the phishing site, criminals could use them to access the account and transfer money.
Summary of Attack
Platform: Office 365
Victims: Employees
Payload: Malicious Link
Technique: Impersonation
What was the Attack?
As individuals are struggling to balance bills, live on reduced revenue or income, and manage unexpected costs during the pandemic, financial stimuli such as the stimulus check and the Payment Protection Program are helping people and businesses alleviate some of their financial burdens. This email sent by attackers claims to come from the US Navy Federal Credit Union and states that the user has received $1,100 dollars due to the COVID-19 pandemic.
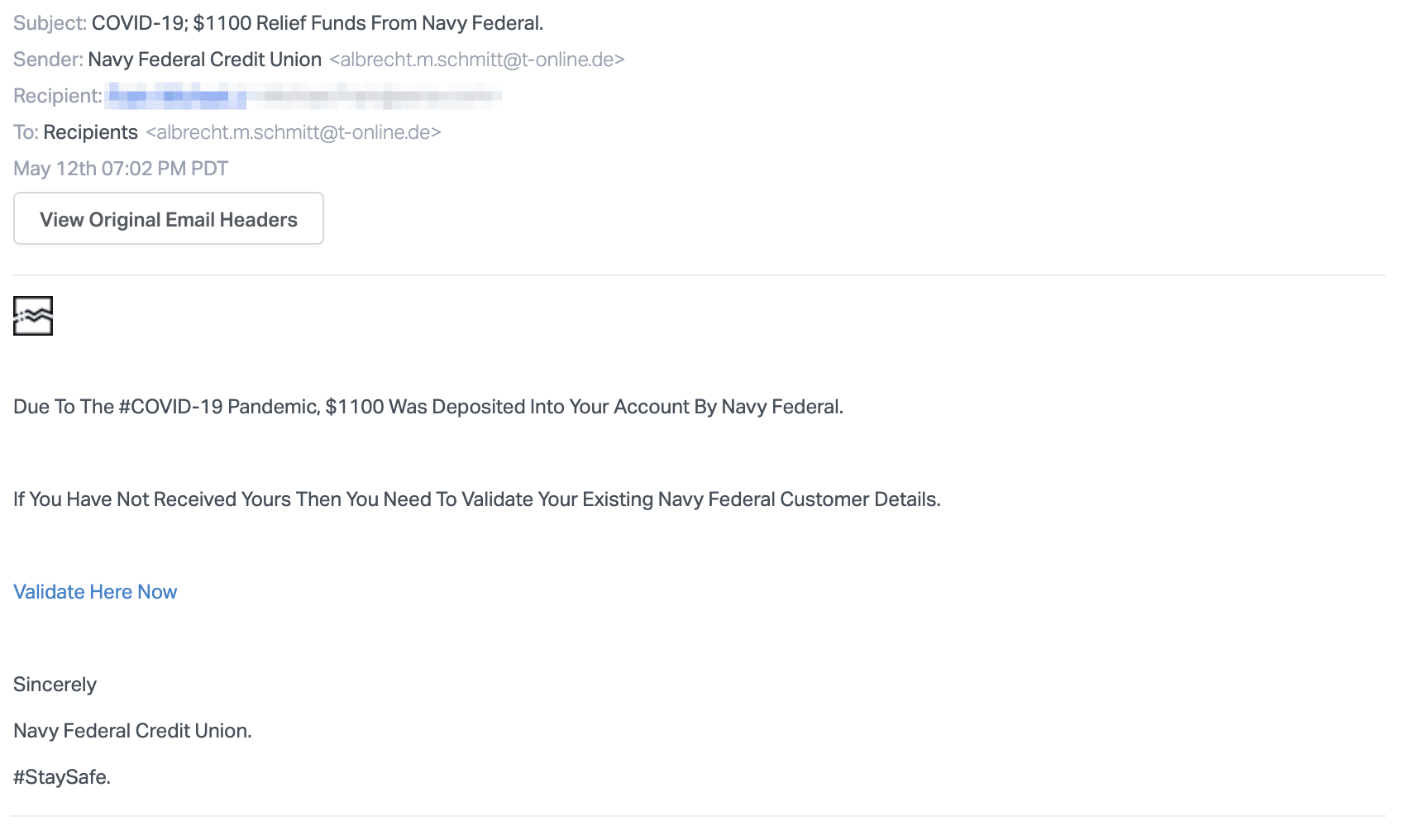
The message claims that if the user has not received funds, they must validate their account with the link provided, which directs them to a phishing credentials webpage.
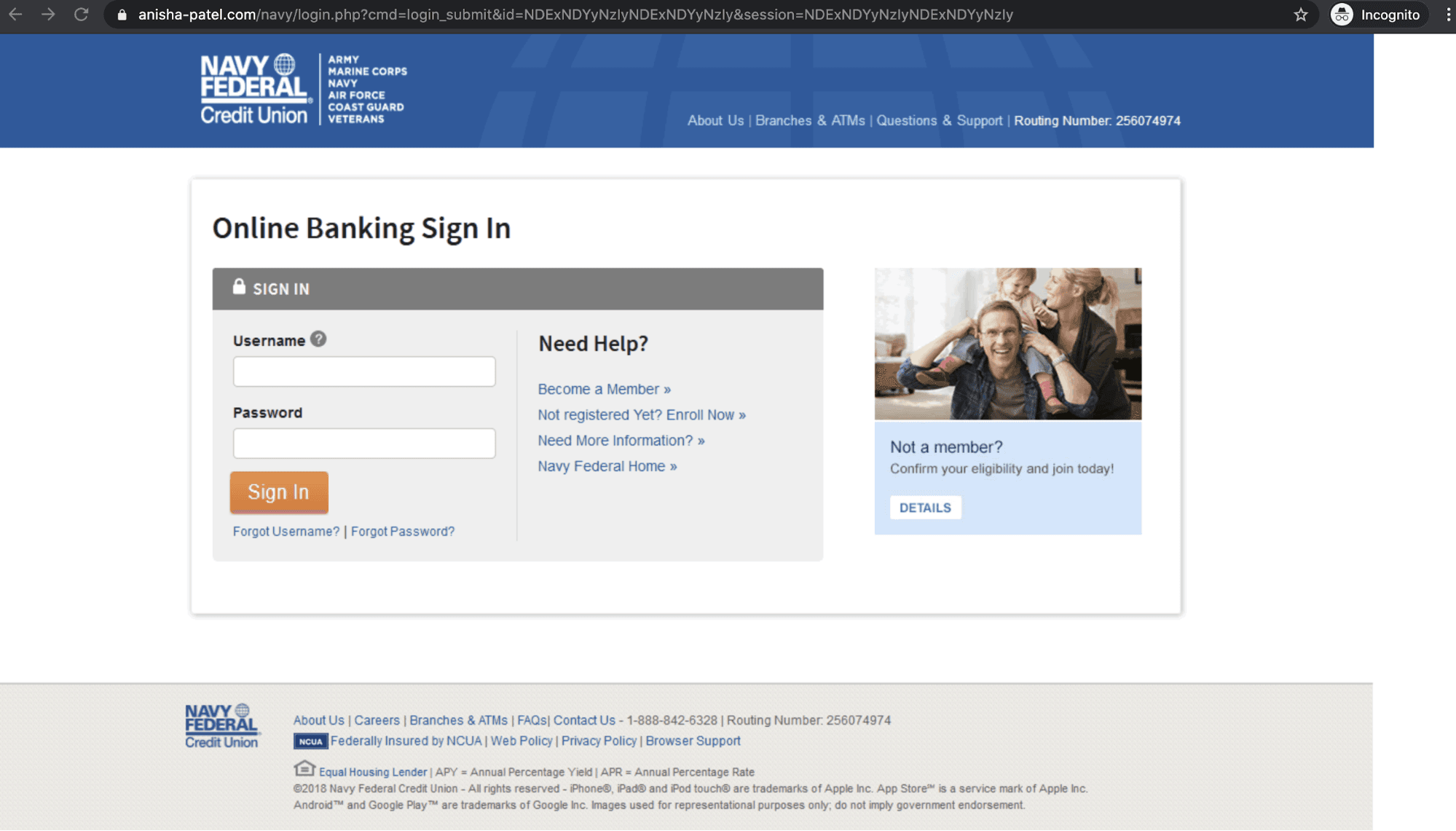
The link in the email takes the victim to a URL that's clearly not associated with the Navy Federal Credit Union. However, the landing page appears very similar to the legitimate Navy Federal Credit Union login page, and a victim searching for their $1,100 may not think to look at the URL before entering their banking credentials. Once entered, the attackers would have full access to the banking account and could then use it to buy items, transfer it into their own accounts, or invoke a variety of other financial crimes.
Why This Attack Bypassed Existing Security Infrastructure
Most traditional email security systems should recognize this email as a credential phishing attempt, due to the mismatch between the display name and the sender domain, as well as the inclusion of a malicious link. In addition to these traditional indicators of compromise, Abnormal also noticed that the message was related to COVID-19, which is currently being exploited by actors, and that the language included a suspicious financial request.
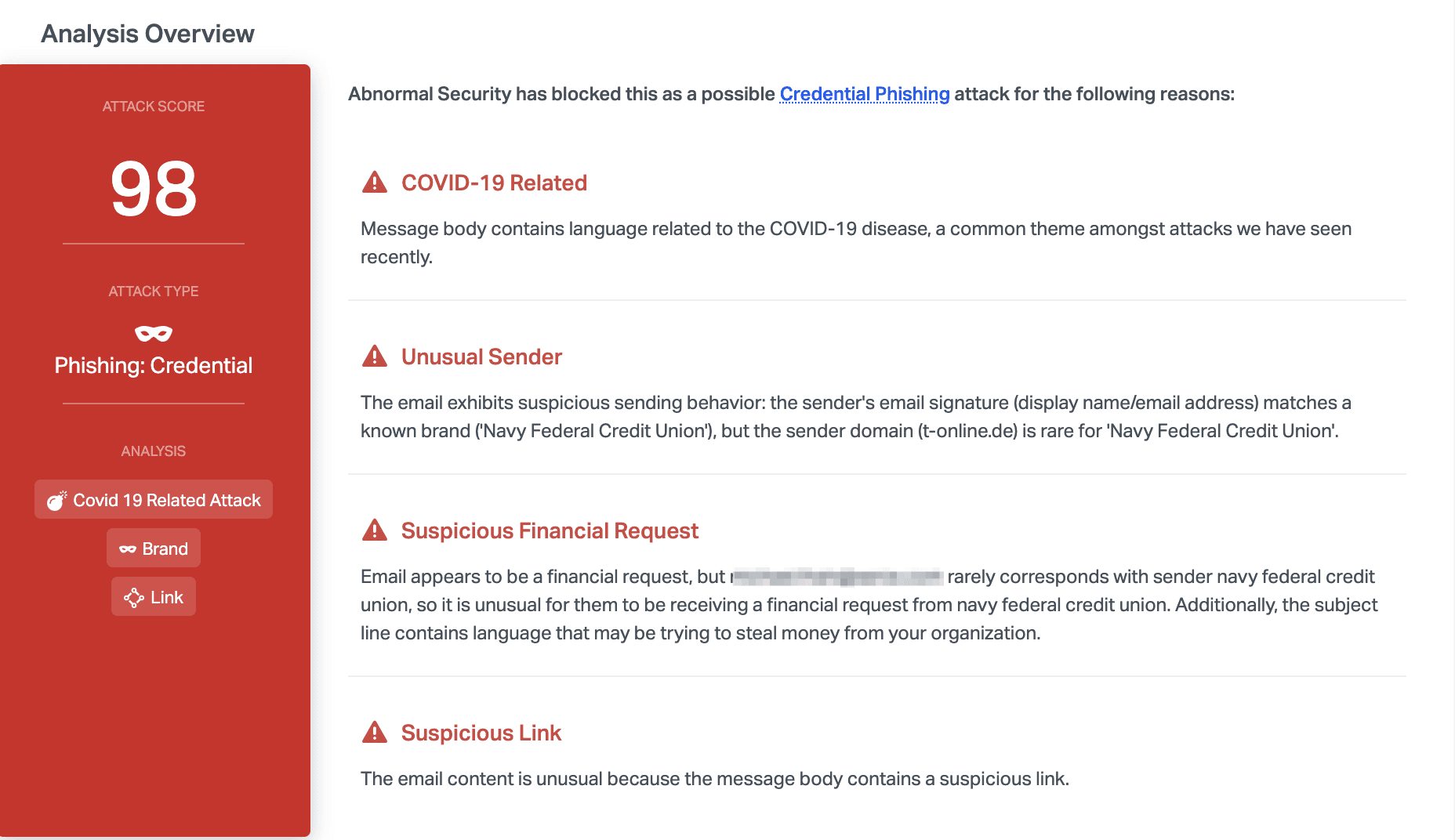
By taking a closer look at the original email, we can see that the attacker purposely masks the link with text, and hopes that the appearance of the landing page will convince the victim of its validity. We also notice that the language is invoking a sense of urgency and in a case where the email recipient has not yet received their relief funds, they may be more inclined to believe this email.
Furthermore, the attacker sent themselves the email (as seen in the to-field of the email attack), while the victim’s email address was placed in the BCC field. The email body itself is vague and contains no personalization, which is a common tactic used by attackers to mass send this campaign. By doing so, they can hide the number of victims from one another, as well as expand their net of targets, without needing to send individual emails to each person.
Curious how Abnormal can stop these attacks from reaching your end users? Request a short demo to see how Abnormal can work in your environment.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

