As Abnormal continues to fortify cloud identity protections, the next step is enhancing threat hunting workflows and ongoing investigations.
While Abnormal can automate the hunt for compromised users with Account Takeover Protection, there are many reasons why a Microsoft 365 account should be disabled or user access revoked that do not fall into the realm of identity takeover by an external attacker (a known malicious insider or user who had left the organization but somehow maintained access, for instance).
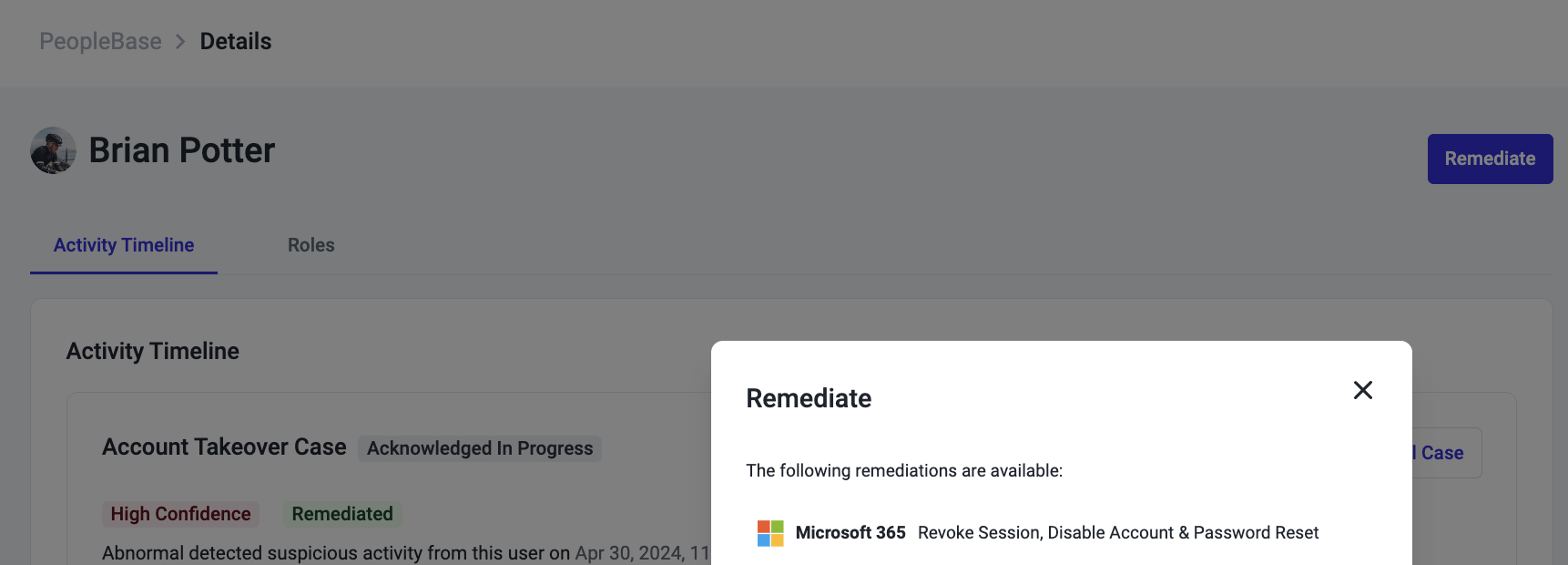
Now, directly through a user’s PeopleBase entry, all customers have the ability to manually suspend Microsoft 365 access:
Revoking active sessions
Disabling user accounts
Forcing password resets