Compromised Account Used to Launch Internal Phishing Attack
Compromised accounts are commonly used by cybercriminals to send additional attacks because they appear to originate from a trustworthy source—typically a known partner or customer, or a known coworker within the organization. In this attack, the account was first compromised, and then attackers used it to launch internal phishing attacks to gain access to additional accounts.
Summary of Attack Target
- Platform: Office 365
- Email Security: Proofpoint
- Victims: Internal Employees
- Payload: Malicious Link
- Technique: Compromised Internal Account
Overview of the Internal Phishing Atack
In this attack, the email itself is simple and masquerades as an encrypted message notification related to a OneDrive for Business file. It appears to come from an internal account and is sent to a known coworker, asking them to open the message.
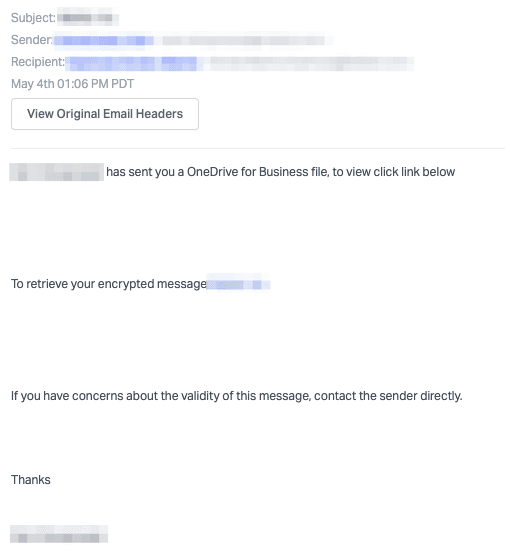
If the recipient clicks on the link, it takes them to a PDF hosted on a Russian domain, which guides victims to click on another link to view and download the supposed file. After clicking the second link, the victims are taken to a phishing page.
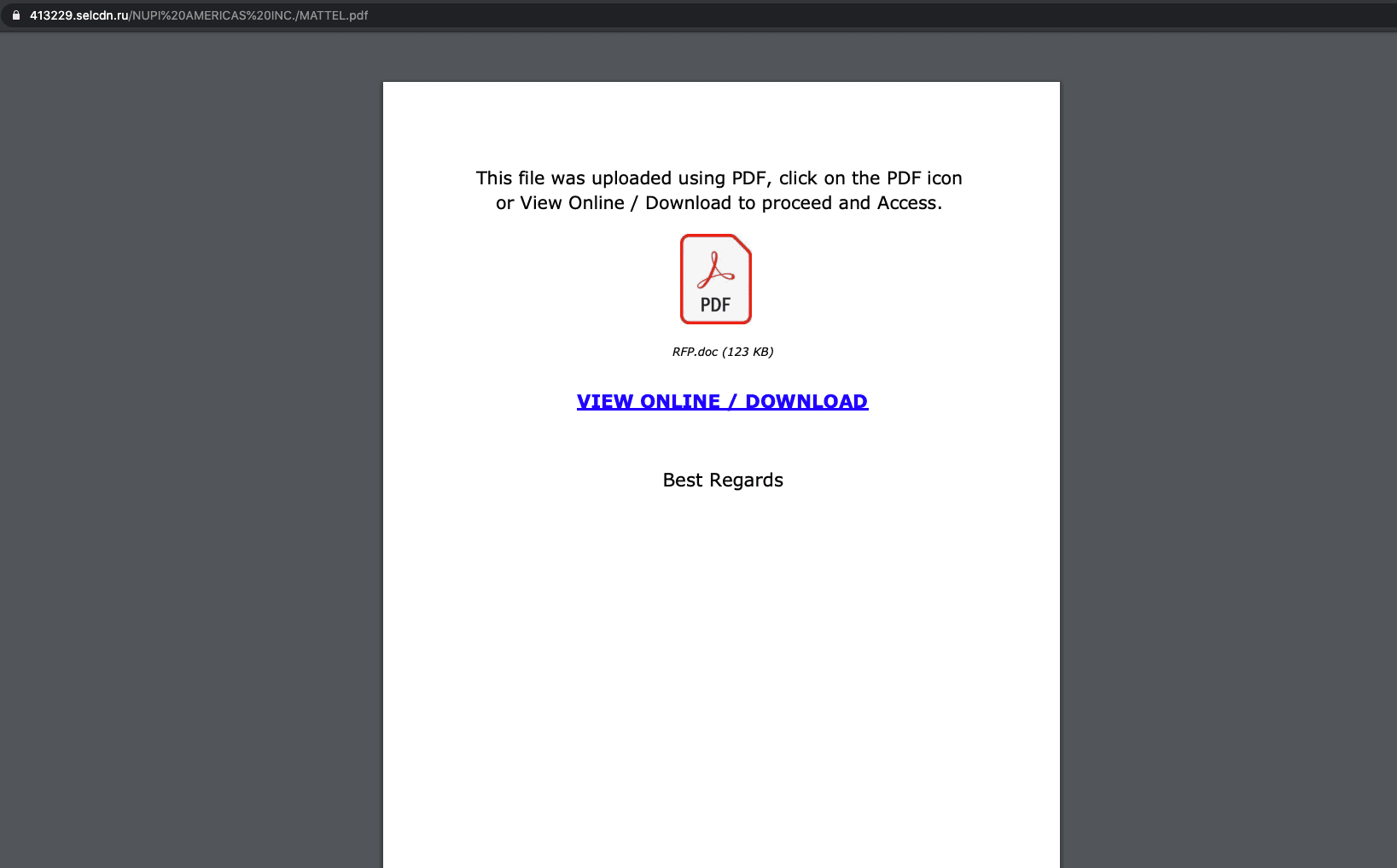
The phishing page asks the victim to enter their Microsoft credentials in order to access the document. Should victims fall for this attack, they risk further compromise within their company as the attacker gains access to more OneDrive and Microsoft Office accounts, from which they can steal valuable and sensitive information, hijack existing conversations, or create new attacks on other employees.
Why Compromised Accounts are Effective for Phishing
By utilizing a compromised internal account, the attacker is able to bypass any external email filtering set in place by the company, as most traditional infrastructure does not view internal-to-internal, or east-west traffic. In addition, it is easier to deceive recipients of this email, as the email appears to be coming from a coworker.
In addition, the link in the email is hidden in the text of the company’s name, and the link hosted on the Russian domain is concealed in the text that says “VIEW ONLINE / DOWNLOAD”. After clicking the links, victims are taken to a phishing page tailored specifically to their company.
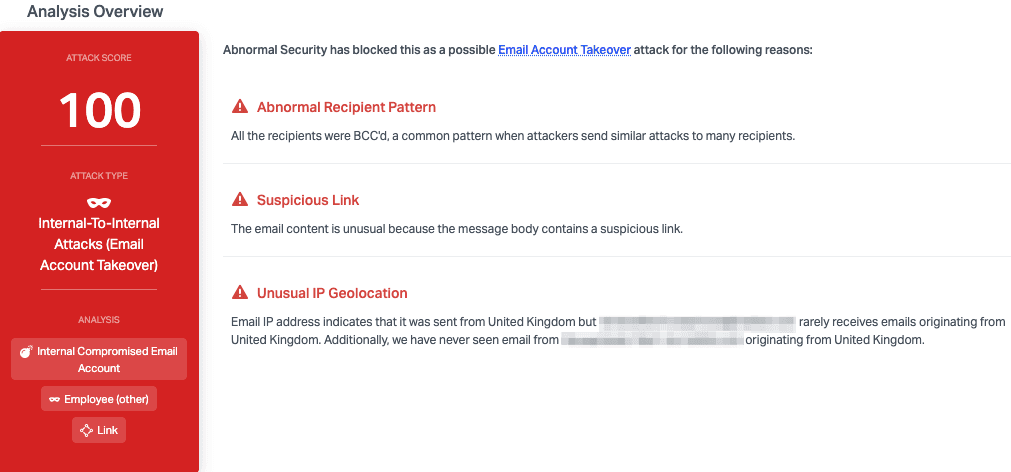
Abnormal stopped this attack due to a variety of malicious signals. Most notably, the attacker sent the original email from an IP located in the United Kingdom, which is suspicious because this sender never sends from the UK, and the recipient rarely receives emails from there either. Combined with the BCC recipient pattern and the suspicious link, it's clear that this account has been compromised and is now being used to attack the organization.
To learn how Abnormal can detect account takeovers within your organization, request a demo today.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

