Customer Communication Leads to Continuous Product Innovation
Here at Abnormal, our product management team continuously looks for ways on how they can make incremental improvements that compound over time and lead to even better customer experiences. Plus, our entire team is abnormally focused on our customers and takes their feedback seriously. As a result, we’ve implemented many refinements in our latest product update to address even the most nuanced improvements suggested by our customers.
Here are some of the latest customer-driven improvements.
Threat Log Exports Increased to 90 Days
We have increased our 30-day export to 90 days to more effectively support our customers with quarterly reporting requirements. Customers can now download a spreadsheet of threat log data matching any filtering criteria in a comma-separated values (CSV) file for offline analysis and archival purposes.
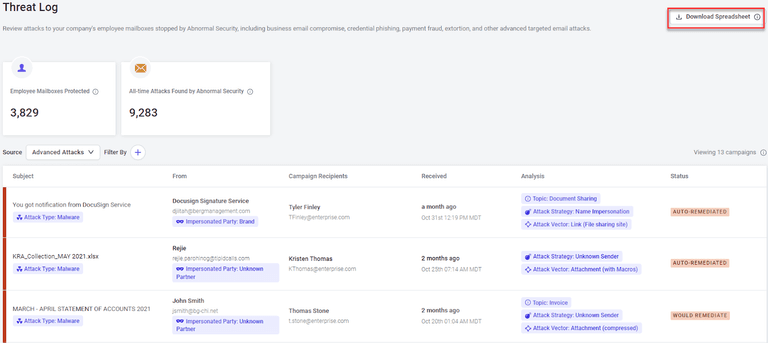
If continual data exports and offline analysis is your primary use case, we recommend integrating Abnormal into your existing SIEM infrastructure to automate the operation.
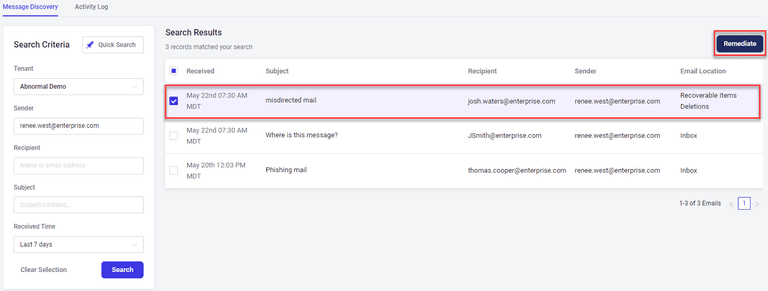
Streamlined Operations: Search and Respond Speed Improvement
Abnormal has decreased the response time by 60%, now providing instant results in mere seconds. The speed improvements help IT security and messaging teams locate messages and remediate them more quickly. Customers of Microsoft 365 and Google Workspace can use Search and Respond to find and delete messages with only a few clicks. Our Search and Respond functionality enhances Microsoft 365 with rapid results for the last 30 days of email messages in seconds.
This feature can be useful in security and compliance scenarios, including:
- When an employee unintentionally sends a critical internal communication.
- When an employee is unsure where a message is located.
- When harmful or undesirable mail gets past email security solutions in extremely rare circumstances.
Admins can search by fields like sender, recipient, and subject, and see a list of messages that were sent and the metadata contained in them, and view message bodies and headers. From there, admins can choose to remediate those messages.
Streamlined Operations: Threat Log Navigation Enhancement
Users can now navigate via convenient arrow keys to swipe through the threat log details page to rapidly locate the most recent or older email campaigns. Customers benefit from increased productivity and control as messaging admins or IT security analysts navigate between email campaigns to complete investigations and identify attacks requiring significantly less time and clicks.
Improving Customer Satisfaction, One Feature at a Time
We aim to have open and transparent communications with our customers and relentlessly work to continually improve and expand our product capabilities. Together, we can solve the problem that matters most, which is providing the highest level of protection for all email threats. If you’re a current customer who would like to request a new feature, please reach out to your Customer Success representative.
Not yet an Abnormal customer? Request a demo today to learn how Abnormal can enhance your email security capabilities and provide visibility into email threats that other solutions miss.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

