Spoofed Healthcare Email Used for Identity Theft
Healthcare continues to be a preferred method for cyber attacks, and this attack features an impersonation of UnitedHealthcare in the form of a request for a claim.
Summary of Attack Target
- Platform: Office 365
- Payload: Malicious Link
- Technique: Spoofing / Phishing
Overview of United Healthcare Phishing Scam
The email appears to originate from notifications@e-notifications.myuhc.com, which is an authorized UnitedHealthGroup Incorporated domain. However, this email is actually spoofed—authentication fails for this message and it is revealed the sending domain is actually ncswi.com. This domain is registered through a common hosting service and is not a CSC Corporate domain that the United Health Group belongs to.
The email states that the recipient is eligible for a health card overpayment refund and displays a "See My Claims" button in order to view the money the recipient could receive.
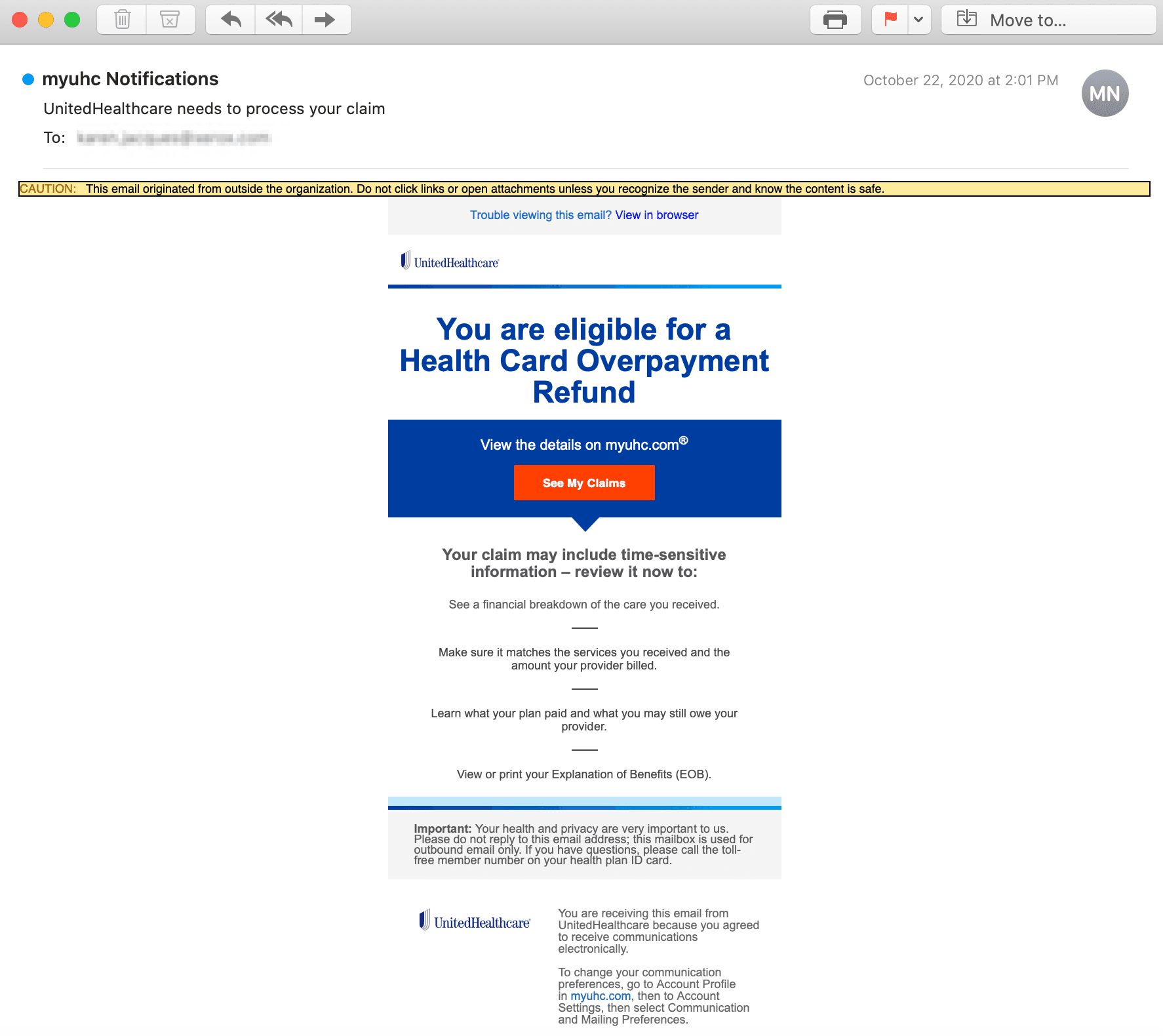
The button contains a concealed link that redirects the recipient to "http://azovmashprom.com.ua/sit...". The landing page mimics the official United Healthcare website, and is a form that requests the recipient to input their Full Name, and Date of Birth.
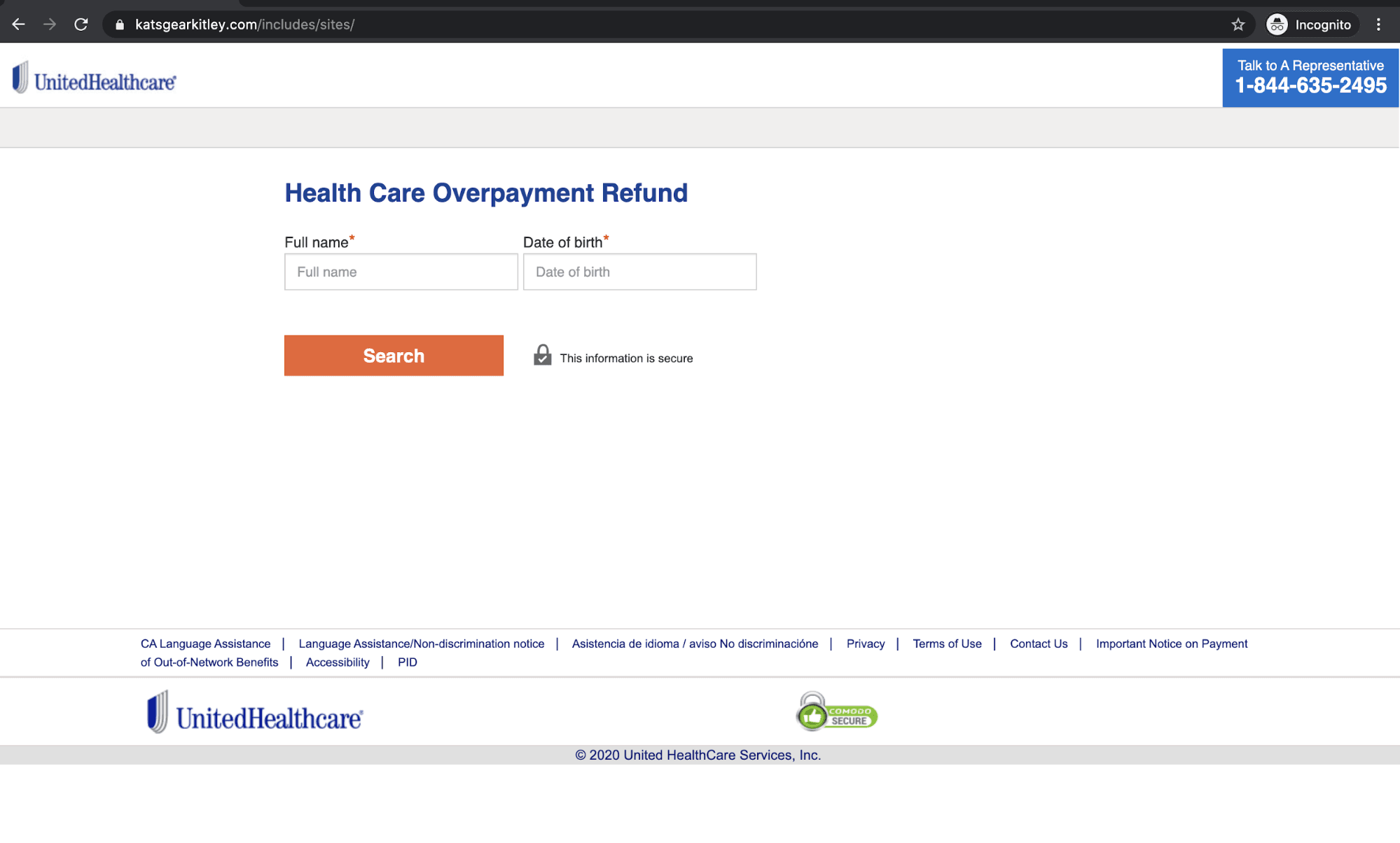
There is a search button provided for the recipient to click on, where they are notified of a refund entitlement in the amount of $683.34.
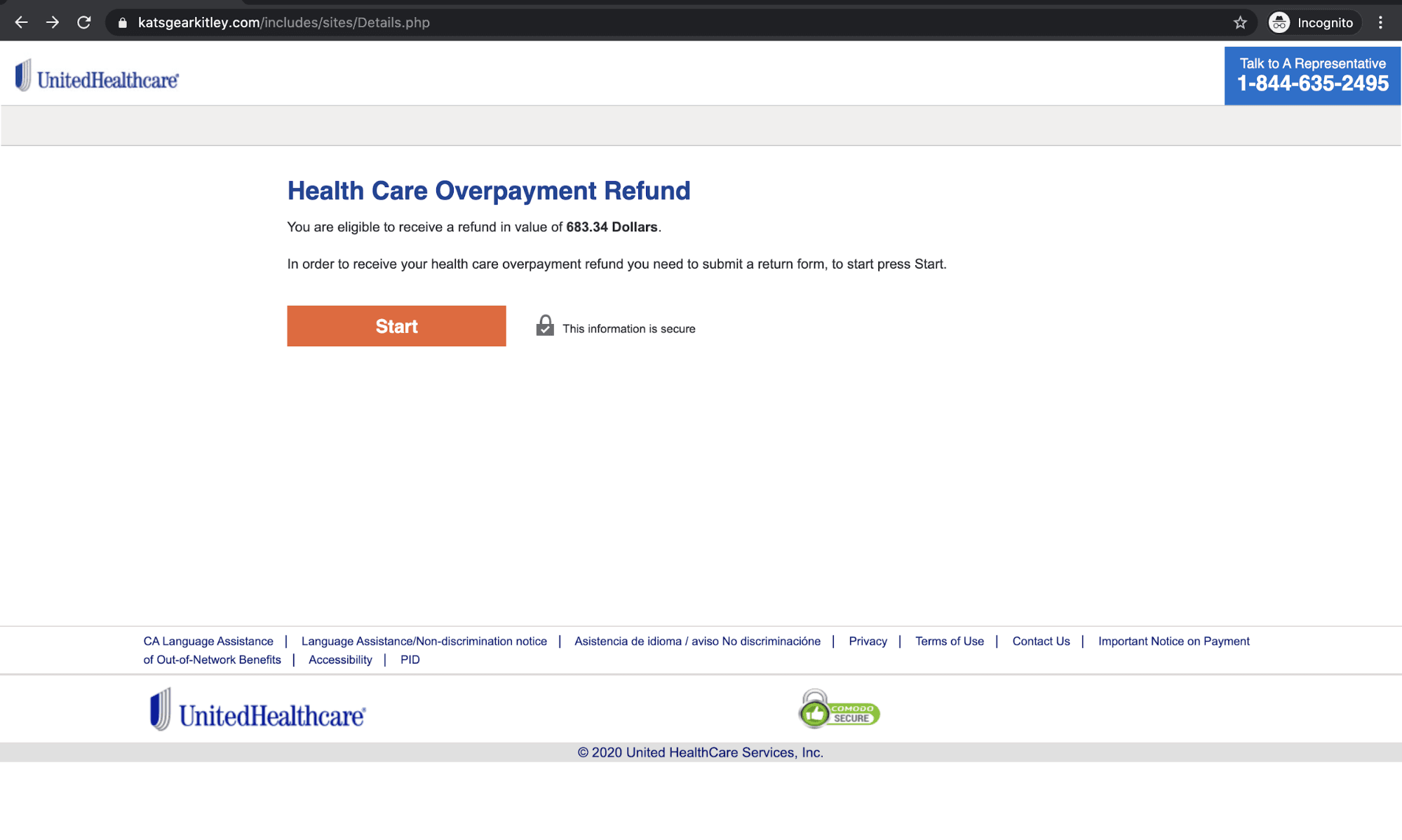
The recipient is then prompted to press start and is led to the final phase of the attack where they can enter all of their personal information including their Name, Social Security Number, and Driver's License Number.
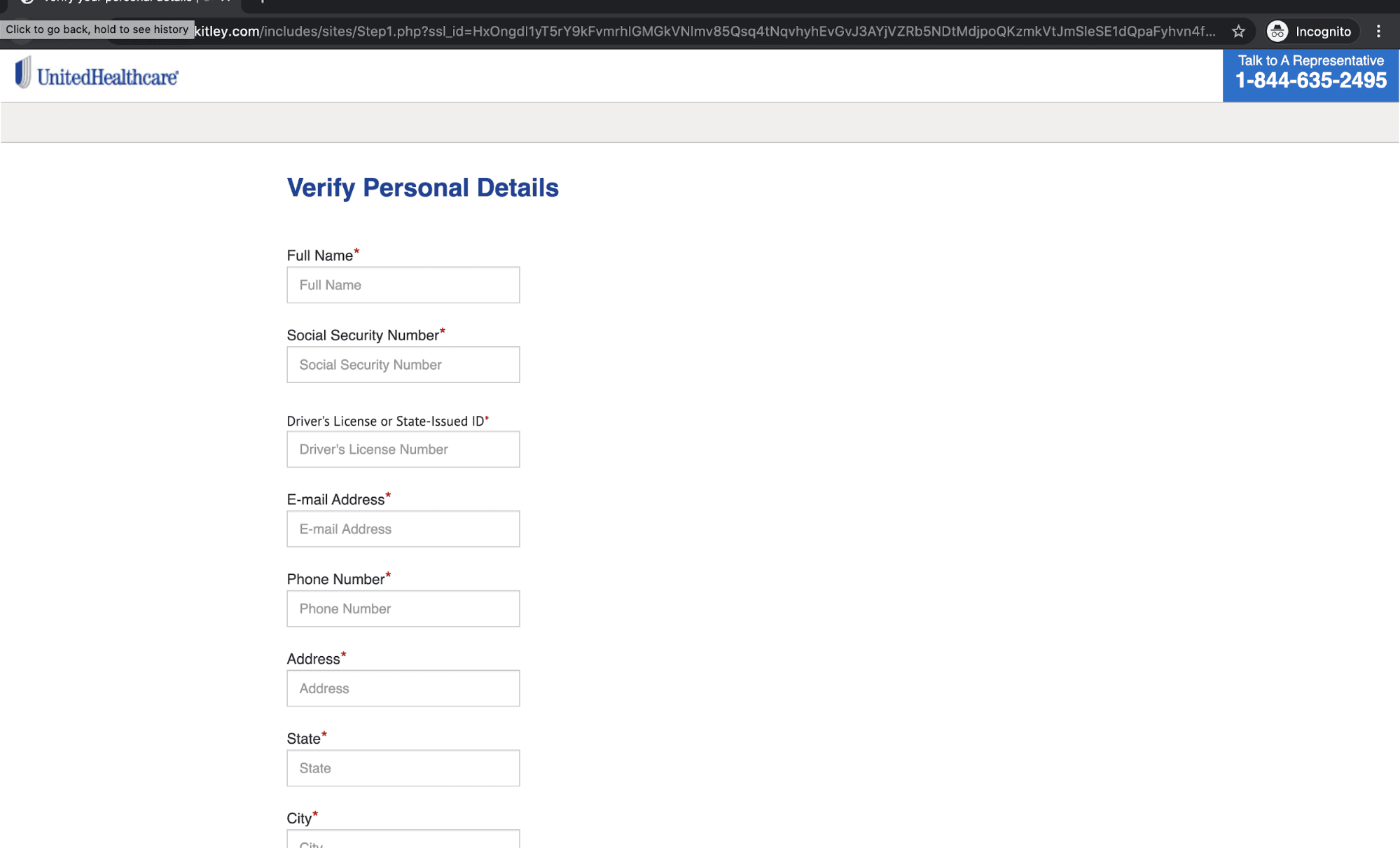
If the recipient falls victim to this attack, their extremely sensitive and personally identifiable information is compromised. Attackers can use this information to commit multiple forms of fraud, including identity theft.
Why the UnitedHealthGroup Scam is Effective
The attacker uses a sense of urgency to encourage the recipient to check their status by stating that their claim may include time-sensitive information. They take this a step further by having multiple landing pages and promising a return of $683.34 if they submit their information.
To the recipient, this email appears to come directly from UnitedHealthcare. The attacker utilizes not only spoofing to deceive the recipient, but also incorporates the UnitedHealthcare logo and address into the email, increasing the appearance of legitimacy.
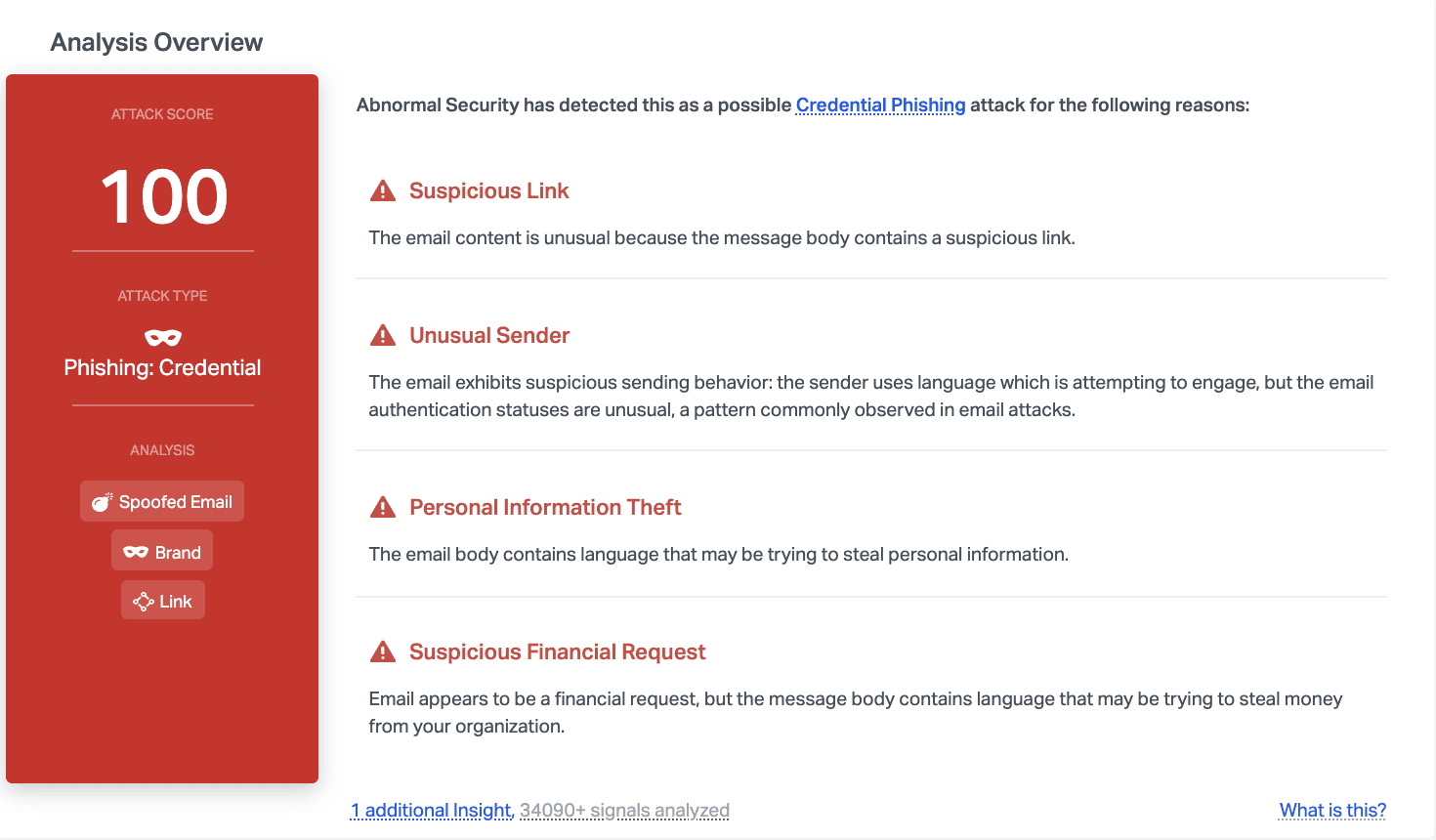
Abnormal is able to catch this attack due to the suspicious link, the unusual sender, and the fact that the email includes language that indicates that it may be attempting to steal financial information. In addition, this is an attack that we have seen in the past. Although it hasn't been active recently, the attack has now begun to resurface with little change.
To see how the Abnormal platform can protect you from spoofed emails, request a demo today.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

