QuickBooks Impersonated in Invoice Fraud Scheme
Quickbooks is popular accounting software that also supports the management of essential business functions such as payroll, billing, and invoicing. Its widespread use, especially among small businesses, has made it a target for impersonation among attackers trying to steal valuable information from unsuspecting employees.
In this attack, scammers impersonate QuickBooks to steal valuable credential information from their target.
Summary of Attack Target
- Platform: Office 365
- Payload: Link
- Technique: Spoofing / Impersonation
Overview of the QuickBooks Impersonation Attack
In this email, the attacker impersonates Quickbooks and sends a fake invoice from a supposed vendor that the recipient is meant to pay. They use spoofing to bypass traditional mail filters and gain legitimacy in the eyes of the recipient.
Although the email appears to originate from “quickbooks@notification.intuit.com”, the headers reveal that the true sender domain is “airtelbroadband.in”, which fails DMARC authentication. The email prompts the recipient to “Review and Pay” by clicking on the indicated button, leading them into the attacker’s phishing trap.
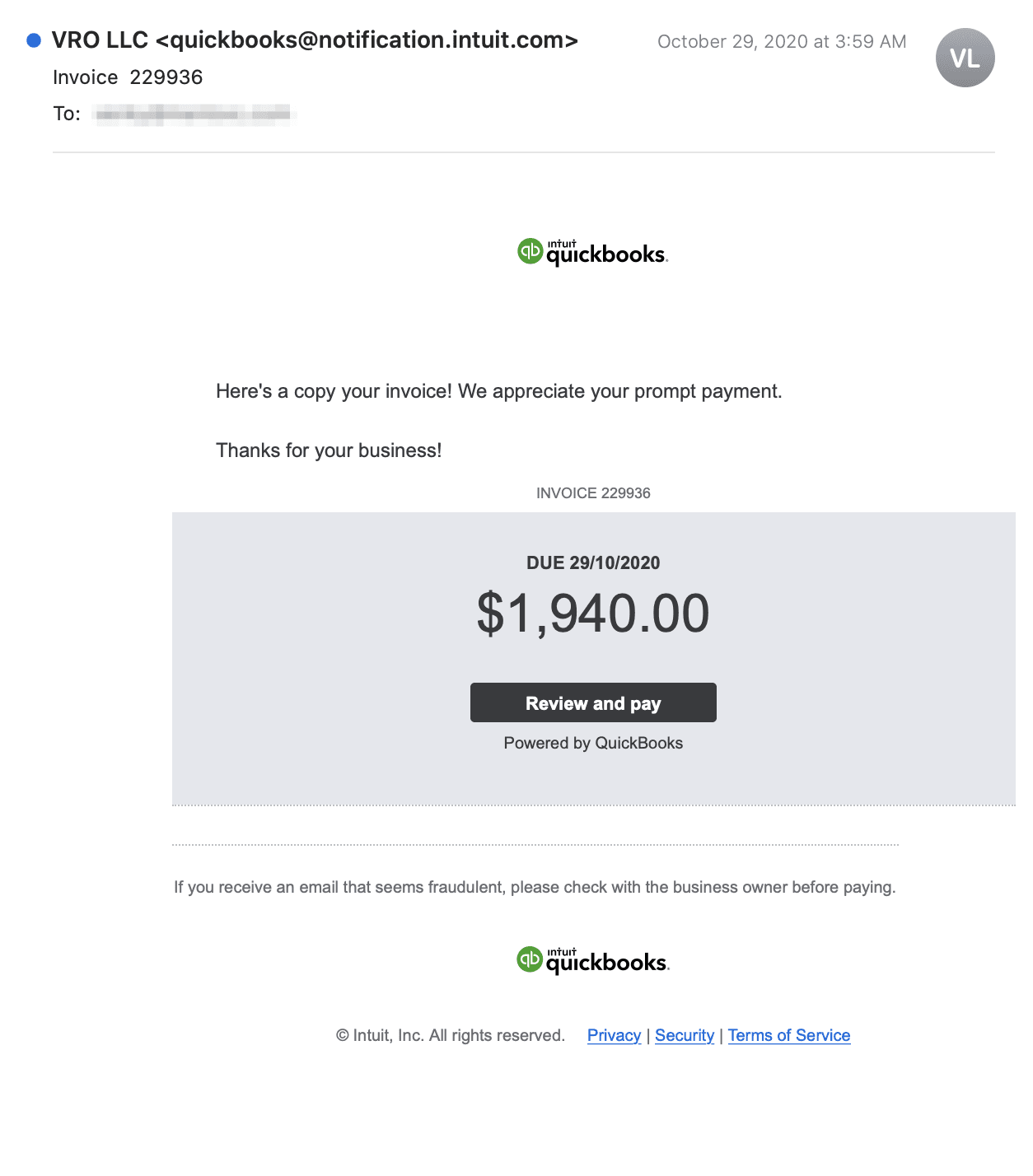
The “Review and Pay” button provided by the attacker disguises a malicious link, redirecting the recipient to “http://parkburgerkuwait.com/lo...”. While the landing page for this particular link has been removed, in the past we have seen similar attacks that lead to realistic sign-in pages asking for the user’s credentials to access the invoice.
If the victim does not pay close attention to the URL of the “sign-in page", they could easily fall into this trap and release their credentials to the attacker. The email looks legitimate, with sophisticated formatting and links at the bottom that lead to legitimate Quickbooks resources. The only way the recipient could catch the attack is by looking closely at the landing page link, and because businesses receive a high volume of Quickbooks emails, it is possible or even likely that they would quickly skim over the details and miss this crucial piece of information.
If the recipient falls victim to this phishing attempt, they will compromise their QuickBooks credentials and open up their company to a possible breach. Additionally, if the recipient does not realize their mistake, they may become a target of more of these fraudulent attacks in the future.
Why the QuickBooks Impersonation Attack is Effective
This email was received on the same day that the invoice is supposedly due, motivating the recipient to act quickly in paying off this debt. The attacker specifically asks the recipient for a “prompt payment” to increase this sense of urgency, hoping that, in their haste, the victim will overlook the suspicious landing page link.
It is also expertly framed, with Inuit Quickbooks logos and links meant to distract from the malicious link vector. Additionally, the email states at the bottom to check with the business owner before paying to avoid fraud, giving the recipient a false sense of security as it seems counterintuitive for an attacker to warn their target about their potentially malicious email.
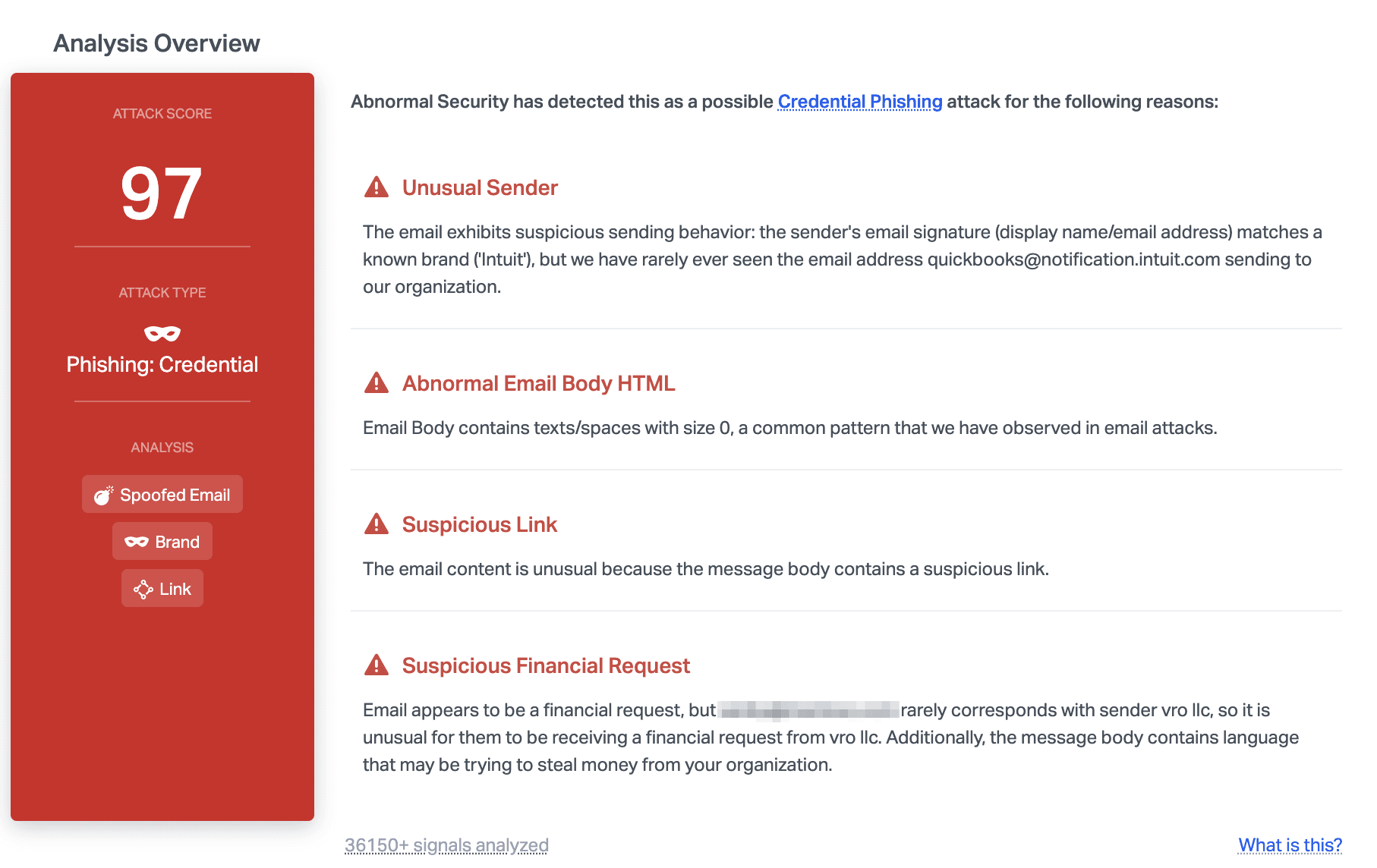
Abnormal determined that this email was malicious due to the unusual sender, suspicious link, and the unusual financial request, understood in the body of the email. Additionally, Abnormal knows that QuickBooks impersonations are widespread across all industries. We have seen nearly 900 of these particular attacks in the mailboxes of over 20 different customers and we expect the rate of these attacks to rise with the continued growth in usage of QuickBooks’ online services.
To learn how to protect your organization from QuickBooks and other impersonations, see a demo today.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

