Payment Inquiries: The Precursors to Invoice and Payment Fraud
Abnormal recently detected campaigns targeting our customers where malicious actors will impersonate major brands and reach out to accounting teams to ask if there are any outstanding invoices for the company they are impersonating.
Abnormal classifies these messages as “Payment Inquiries”, and while these messages may not seem like attacks, they are often the precursors to invoice and payment fraud. As a result, organizations should use extreme caution with these messages, and ideally, email security solutions should prevent these messages from reaching employee inboxes.
What is a Payment Inquiry Message?
Payment inquiry messages are a very common method in which attackers gain the information they need to initiate a successful invoice or payment fraud attack. The goal of these messages is to gain information about the payment status of outstanding invoices and subsequently redirect payment to be sent to a fraudulent bank account. These inquiries typically have the following characteristics:
- Impersonation of a Known Brand: Attackers initiate payment inquiries using one of two methods to impersonate a known brand: they will either spoof the email of a legitimate vendor or impersonate the domain by registering a lookalike domain. For example, they may use redbIrd.com in hopes that the recipient won't notice the discrepancy from the real domain at redbird.com.
- Innocuous Content: The content of these emails is seemingly innocuous. The attackers will often claim to be auditing outstanding invoices for the brand they’re impersonating and ask questions to gain information about when outstanding invoices may be due. Attackers may ask about the process to update bank details for upcoming transactions, claiming there have been bank changes.
- Change in Reply-to Address: If the email is spoofing a known brand, the attacker may alter the reply-to address to redirect the conversation thread back to themselves.
Here is an example of a Payment Inquiry message that Abnormal Security has detected for one of our customers, with anonymized names and email addresses:
Subject: [External] Invoices / Due Payments
Sender: Samsung (accountreceivables@samsung.com)
Reply-to: acountpayabledept@personalemail.com
Hi,
We want to update our record of accounting for the month ended April,2020 which is yet to be balanced and also audit our account's opening balance for the new month, Therefore we will like to know if there is/are any outstanding payments till date. If there is, then for the record let us know how much is due and when is the invoice due date?
Due to the pandemic crisis we urge you to review all outstanding invoices with you.
stay home and stay safe.
John Smith
Why Payment Inquiry Messages are Alarming
Before we dive into the implications of these payment inquiry messages, let’s first discuss invoice fraud attacks to better understand how these inquiries fit into attacker strategy.
Typically, invoice fraud attacks are hyper-targeted attacks. In these attacks, attackers hijack existing financial conversations to attempt to execute payment against fraudulent invoices or attempt to update a valid payment with fraudulent bank account details.
Invoice fraud attacks are high-cost, high-reward attacks:
- High Cost: These types of attacks require significant effort to initiate. In order to execute such attacks, attackers need to have executed successful credential theft attacks on vendors to be privy to their conversations and thus perfectly time their attacks.
- High Reward: Attackers are hijacking existing conversations, so they see higher engagement and higher success because their targets have already been engaged in a legitimate conversation. As a result, they are less likely to be suspicious of changes that the attackers will introduce, like requests to change banking details.
Invoice fraud attacks often require attackers to be engaged with their targets for long periods of time. For example, Abnormal Security observed an attack while our tools were operating in passive mode that was conducted over nine full weeks. Attackers will engage in these drawn-out attacks because the financial rewards can be significant—in the case of this nine-week attack, they would have stolen more than $700,000 from the target had Abnormal not stopped it.
That said, attackers are able to reduce the cost of conducting invoice fraud attacks by leveraging payment inquiries as a first step. Because these attacks impersonate or spoof addresses of known brands like Samsung and Unilever, they don’t require stolen credentials to hijack conversations. This allows malicious actors to create significantly more opportunities for invoice fraud attacks, with a much lower time and resource commitment.
Attackers do this by employing a “pray and spray” method, sending generic inquiry messages to multiple recipients, sometimes within the same organization. These inquiry messages are seemingly innocuous because they’re only requesting information, and attackers only need to get a single engagement from a target in order to initiate an attack with the information that has been provided to them.
Because of its low cost, attackers are able to execute exponentially more payment inquiry attacks than targeted invoice fraud attacks.
How Payment Inquiries Lead to Payment Fraud Attacks
Let’s take a look at real-life examples of payment inquiries that Abnormal has detected and stopped in order to understand how these messages lead to attacks.
Recently, we observed a coordinated payment inquiry message sent to various Accounts Payable team members within a single customer over the span of a few days. These messages spoofed various known brands (Samsung, Halo Electronics etc.) with the same generic request to gain information about overdue payments. Messages were identical with suspicious reply-to addresses, indicating a strategy of diverting the conversation away from the spoofed inbox, and a hope that employees would provide them with information about outstanding payments.
We have also been observing identical payment inquiry messages sent to multiple customers for each brand that is impersonated, indicating that the hypothesis of the spray and pray technique is true.
Here’s the example of the email again:
Hi,
We want to update our record of accounting for the month ended April,2020 which is yet to be balanced and also audit our account's opening balance for the new month, Therefore we will like to know if there is/are any outstanding payments till date. If there is, then for the record let us know how much is due and when is the invoice due date?
Due to the pandemic crisis we urge you to review all outstanding invoices with you.
stay home and stay safe.
John Smith
Note that this email doesn’t (yet) request anything that seems like an attack and does not contain links or attachments that may cause secure email gateways to block it. However, this is still a dangerous message for employees to engage with, because it can lead to an attack. Here’s how the attack could play out:
- Many employees in the Accounts Payable team receive these emails, but don't realize it.
- One unsuspecting team member replies with the list of unpaid invoices.
- The attacker claims that their banking details have changed and requests that the unpaid invoices be sent to the new bank account.
- The employee complies with that request and updates bank account details so the payment is sent to the attacker.
As a result, these seemingly innocuous messages have the potential to lead to large financial losses.
How Abnormal Security Protects Against Payment Inquiries
Abnormal Security doesn’t only protect our customers from invoice fraud and billing account update attacks. We also protect our customers from the payment inquiry messages that lead to those attacks.
Our ABX technology uses impersonation signals and content signals to identify and remediate payment inquiry messages from your environment. These can be observed in VendorBase—our global, federated database on vendor and customer behaviors.
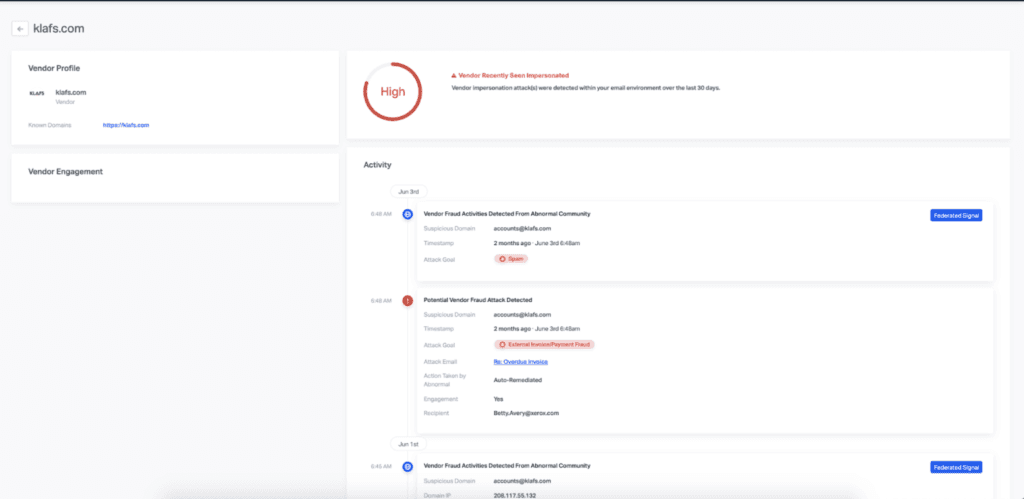
To learn more about how Abnormal protects organizations from payment inquiry attacks, schedule time with an Email Security Specialist for a one-on-one product demo.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

