
Wells Fargo customers are being targeted by a phishing campaign impersonating the Wells Fargo Security Team and luring potential victims to phishing pages with the help of calendar invites.
Wells Fargo is a multinational financial services (banking, investment, and mortgage) provider with roughly 263,000 employees in 7,400 locations in 31 countries and territories. It serves one-third of all US households and it was ranked No. 30 on Fortune’s 2020 rankings of America’s largest corporations.
The phishing messages spotted by researchers at email security company Abnormal Security earlier this month have so far targeted over 15,000 Wells Fargo customers using .ics calendar file attachments containing events directing the recipients to phishing pages.
Calendar notifications used to boost the attacks' rate of success
The attackers' phishing emails claim that the targets have to update their security keys using instructions included within a .ics calendar file attachment to avoid having their accounts suspended.
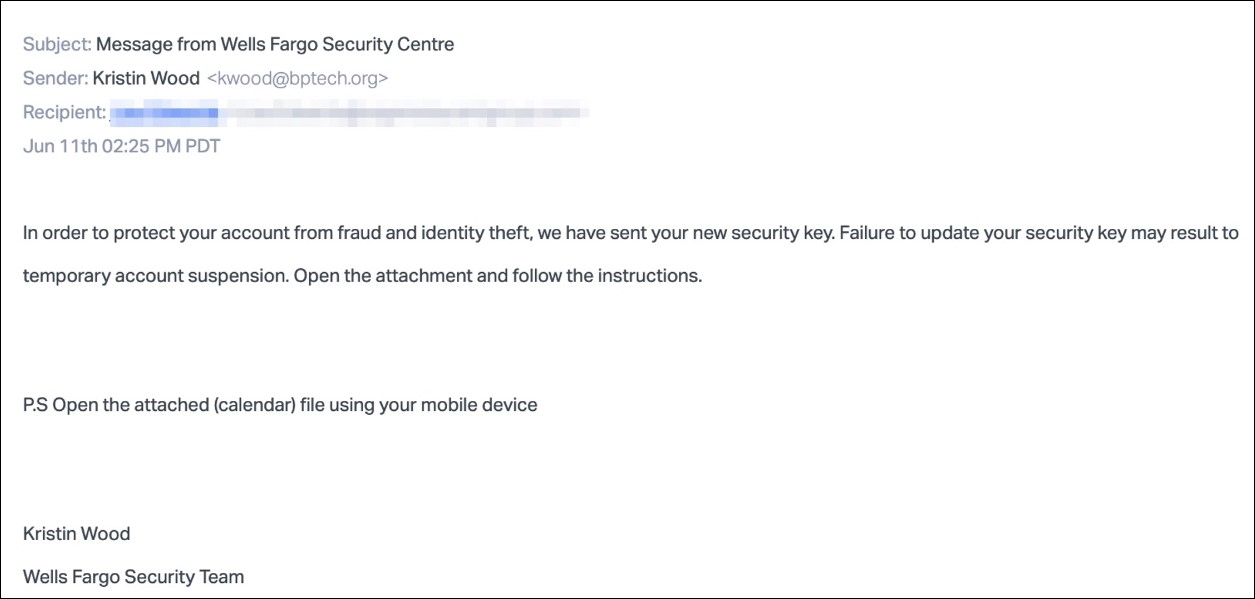
"Contained within the event description is a link to a Sharepoint page which directs the users to click on another link to secure their account," Abnormal Security found.
"This link leads to a fake phishing page for Wells Fargo, where users are prompted to enter sensitive information such as their username, password, PIN, and account numbers."
The scammers also instruct the targets to open the calendar file with their mobile devices to take advantage of the fact that the event included in the .ics file would be automatically added to the victims' calendar.
Subsequently, their calendar apps would deliver automatic notifications that the victims would likely click since they're delivered by a trusted app.
This translates into a higher rate of success, with the attackers being able to harvest sensitive information from a lot more Wells Fargo customers.
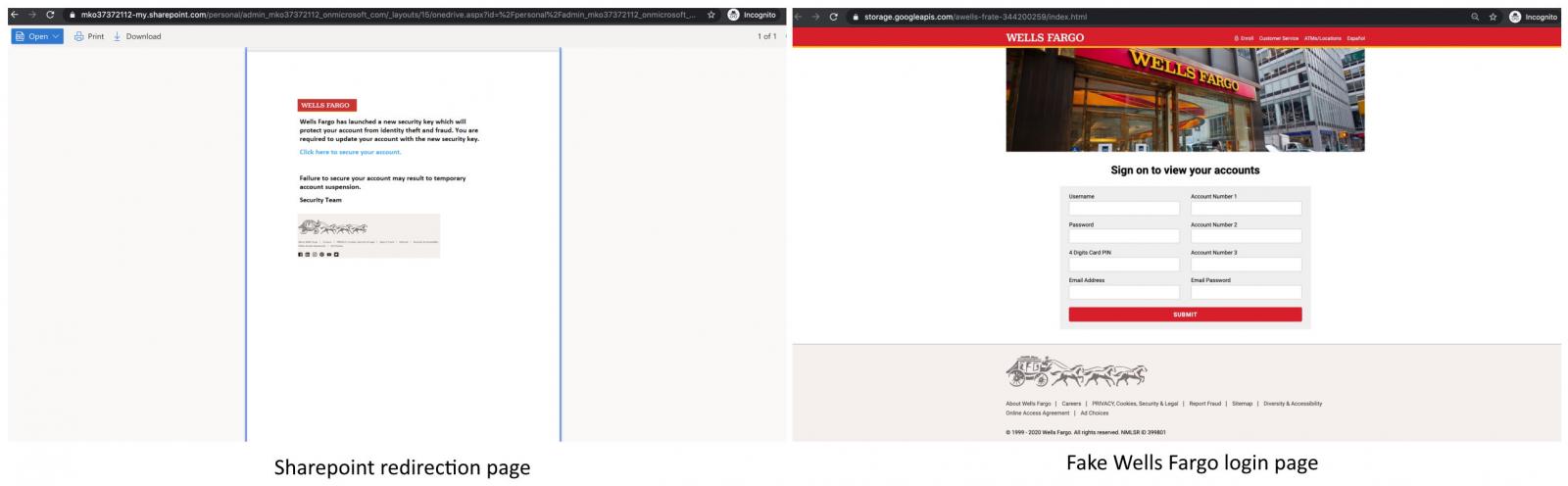
The final phishing landing page where the victims are sent from the Sharepoint redirection page is a fake Wells Fargo login that asks the users to input their credentials, account numbers, email addresses and password, as well as their cards' 4 digits PIN.
If the victims fall for the trick, enter their information, and hit the SUBMIT at the bottom of the phishing page, the attackers would get their hands on all the info they need to compromise and take control of their accounts, stealing their identity and money in the process.
Bank customers are always an attractive target
"Financial institutions are always common targets for attackers," Abnormal Security concluded. "Access to a user’s sensitive information would allow an attacker to commit identity theft as well as steal any money associated with the account."
"Many of these companies have stringent regulations and security in order to protect users and their financial holdings. However, attackers are continually finding ways to compromise users’ accounts."
Earlier this week, F5 Labs' security researchers spotted ongoing attacks trying to steal credentials from customers of dozens of US financial institutions by infecting them with Qbot banking trojan payloads.
Among the list of banks whose customers were targeted by the Qbot campaign, the researchers found Bank of America, Wells Fargo, JP Morgan, Citibank, Citizens, Capital One, and FirstMerit Bank, with 36 different US financial institution and two banks in Canada and the Netherlands being under attack in total.
In April, scammers were also sending out emails impersonating the U.S. Federal Reserve and baiting recipients with financial relief options through the Payment Protection Program.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now