
Scammers have tried to rip off computer equipment suppliers with a targeted email that impersonated the Commissioner of the Texas Department of State Health Services (DSHS).
They did their homework and crafted a credible message with details that would check out at a cursory search.
Diligent attacker
In a short email sent to a company’s sales department, the fraudsters requested a price quote for 20 touchscreen laptops and 200 portable hard drives.
The sender’s email impersonated John William Hellerstedt, the acting Commissioner of Texas DSHS since January 2016, and appears to come from the legitimate domain of the agency, according to Abnormal Security, a company providing email protection.
However, they listed a different email address in the ‘reply-to’ field, from a domain pretending to belong to the City of New York and registered two months ago.
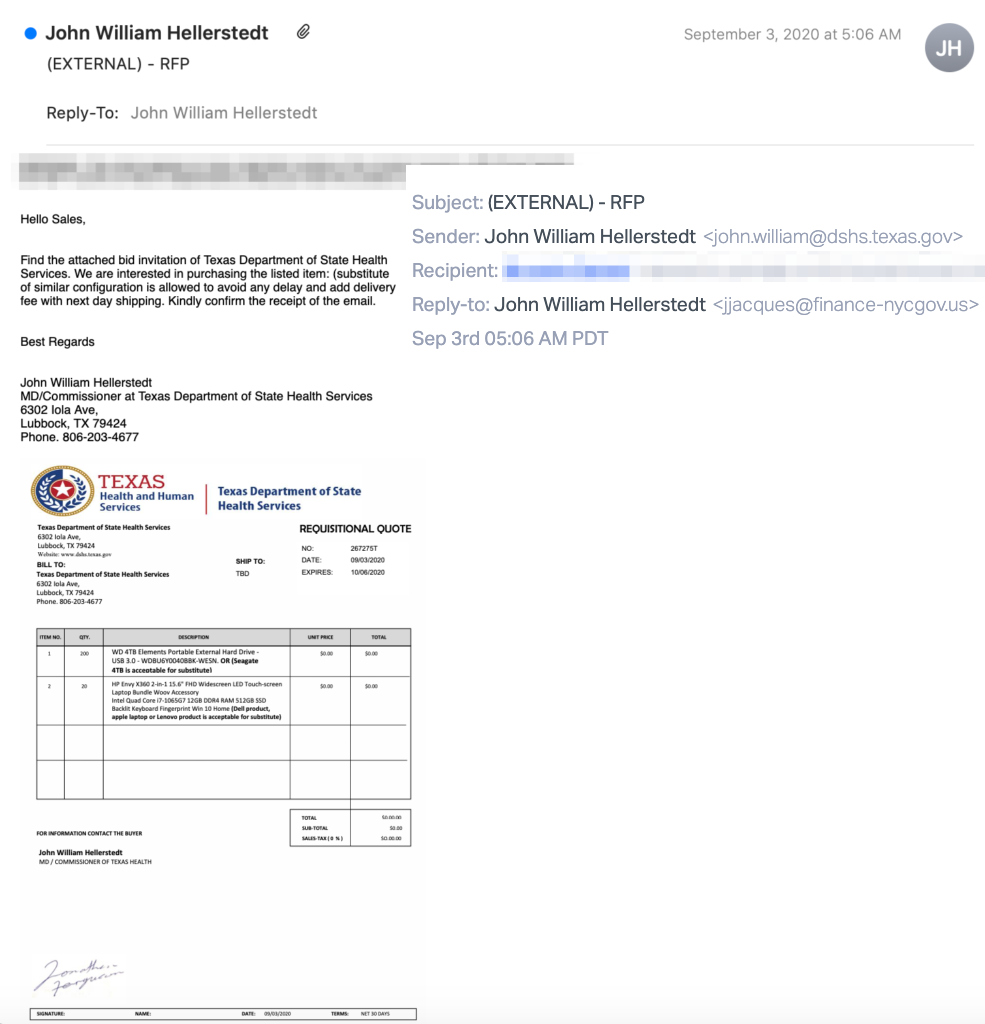
In the fake document above, the scammers do not disclose a shipment address and give the recipient a 30-day deadline to respond to the bid invitation. This is likely to solicit a reply from the target company that would allow them to earn more trust.
Apart from the legitimate-looking sender email address, the phrasing of the message, and the request for quotation document, the fraudsters also dropped a phone number that shows the Texas DSHS as the first result on Google.
Abnormal Security says in a report today that the purpose of the email was to trick the supplier into delivering the products to an address selected by the scammers.
“The attackers' goal is to retrieve merchandise, and later profit from the resale of the stolen goods” - Abnormal Security
The researchers say that the attackers were careful to cover their tracks and used a VPN service to hide their location and true IP address when sending the spoofed email.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now