
Zoom users are targeted by a new phishing campaign that uses fake Zoom meeting notifications to threaten those who work in corporate environments that their contracts will either be suspended or terminated.
So far this series of phishing attacks that spoof automated Zoom meeting alerts has landed in the mailboxes of over 50,000 targets according to researchers as email security company Abnormal Security.
Potential victims are more willing to trust such emails during this time given that a lot of employees are now working from home and take part in daily online meetings through video conferencing platforms like Zoom because of stay-at-home orders and lockdowns caused by the COVID-19 pandemic.
Cloned Zoom login page used for phishing credentials
The phishing emails mimic legitimate Zoom meeting reminders hinting at the target's layoff in a meeting with their company's Human Resources and Payroll Administrative Head that is scheduled to start within minutes.
"When the victim reads the email they will panic, click on the phishing link, and hurriedly attempt to log into this fake meeting," the researchers said. "Instead, their credentials will be stolen by the attacker," .
The victims are also told that their presence is required as part of the "Q1 performance review meeting."
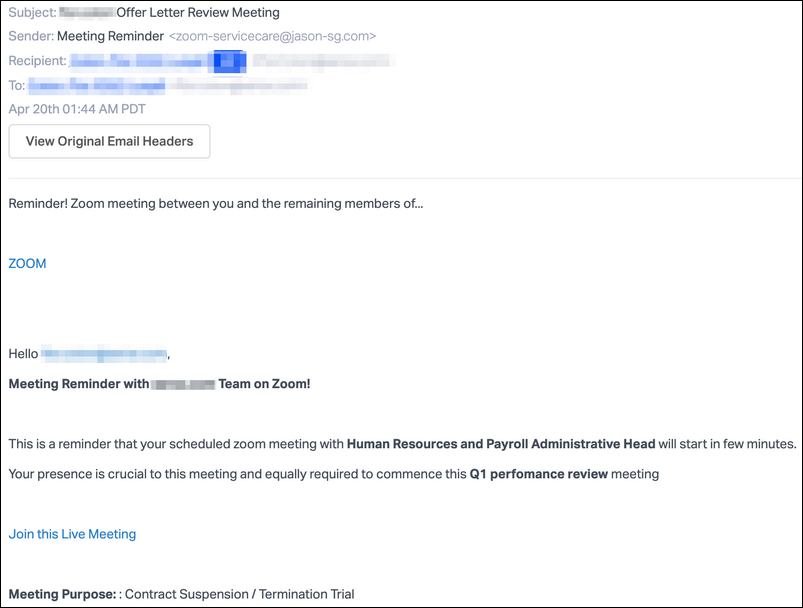
The attackers are using embedded links within the email to redirect the recipients to the landing page hosted at zoom-emergency.[]myftp.org hidden under a link with the asking them to "Join this Live Meeting."
Once they reach the phishing landing page, the victims see a cloned Zoom sign-in page, the only difference from the original being a request to use their enterprise email accounts to log in and that the sign-in form is being used by the scammers to steal the victims' credentials instead of logging them in.
They are pushed by the crooks to enter their enterprise email account credentials with the following phrase: "Zoom now allows you to join and host meetings without signinup. Simply continue with your organization email login to proceed."
Because this landing page is designed and looks identical to the real thing, the targets might have a hard time realizing that they have reached a page that will harvest their credentials instead of Zoom's official site.
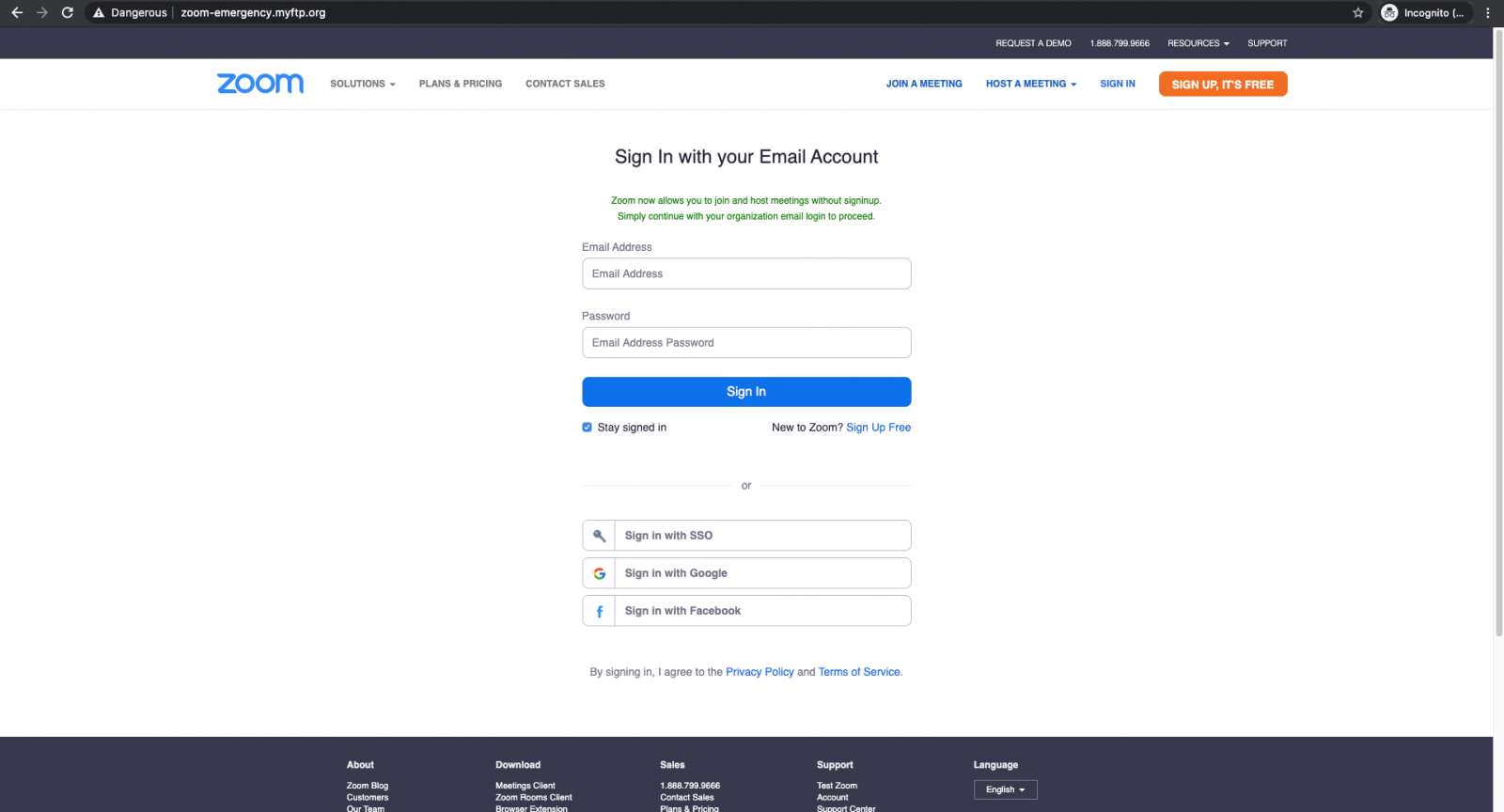
"Frequent Zoom users would look at the login page, think their session has expired, and attempt to sign in again," Abnormal Security explains.
"They would be more likely to input their login credentials without checking the abnormalities in the phishing page such as the URL or non-functioning links."
Cyber-criminals are also stealing Zoom credentials as we reported earlier this month when over 500,000 Zoom accounts were found up for sale on hacker forums and the dark web for less than a penny each, and even given away for free in some cases to be used in zoom-bombing pranks and other malicious activities.
In a statement to BleepingComputer, Zoom said at the time that they are helped by hired intelligence firms to find these password dumps to reset the impacted users' passwords.
Earlier this week, Zoom founder and CEO Eric S. Yuan said that the video conferencing platform surpassed 300 million daily Zoom meeting participants, many of them from enterprise environments.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now