Microsoft Office 365 customers are targeted by a phishing campaign using bait messages camouflaged as notifications sent by their organization to update the VPN configuration they use to access company assets while working from home.
The phishing emails impersonating VPN configuration update requests sent by their company's IT support department have so far landed in the inboxes of up to 15,000 targets according to stats from researchers at email security company Abnormal Security.
These phishing messages are a lot more dangerous because of the huge influx of employees working remotely and using VPNs to connect to company resources from home for sharing documents with their colleagues and accessing their orgs' servers.
Cloned login pages to steal Office 365 credentials
The attackers are spoofing the sender email address in the phishing emails to match the domains of their targets' organizations and embed hyperlinks that instead of directing the recipients to new VPN configs send them to phishing landing sites designed to steal their Office 365 credentials.
"Numerous versions of this attack have been seen across different clients, from different sender emails and originating from different IP addresses," Abnormal Security explains.
"However, the same payload link was employed by all of these attacks, implying that these were sent by a single attacker that controls the phishing website."
.png)
These attacks could have a high rate of success in tricking potential victims since many recipients might click through and log into their Office 365 accounts to avoid losing remote access to company servers and resources.
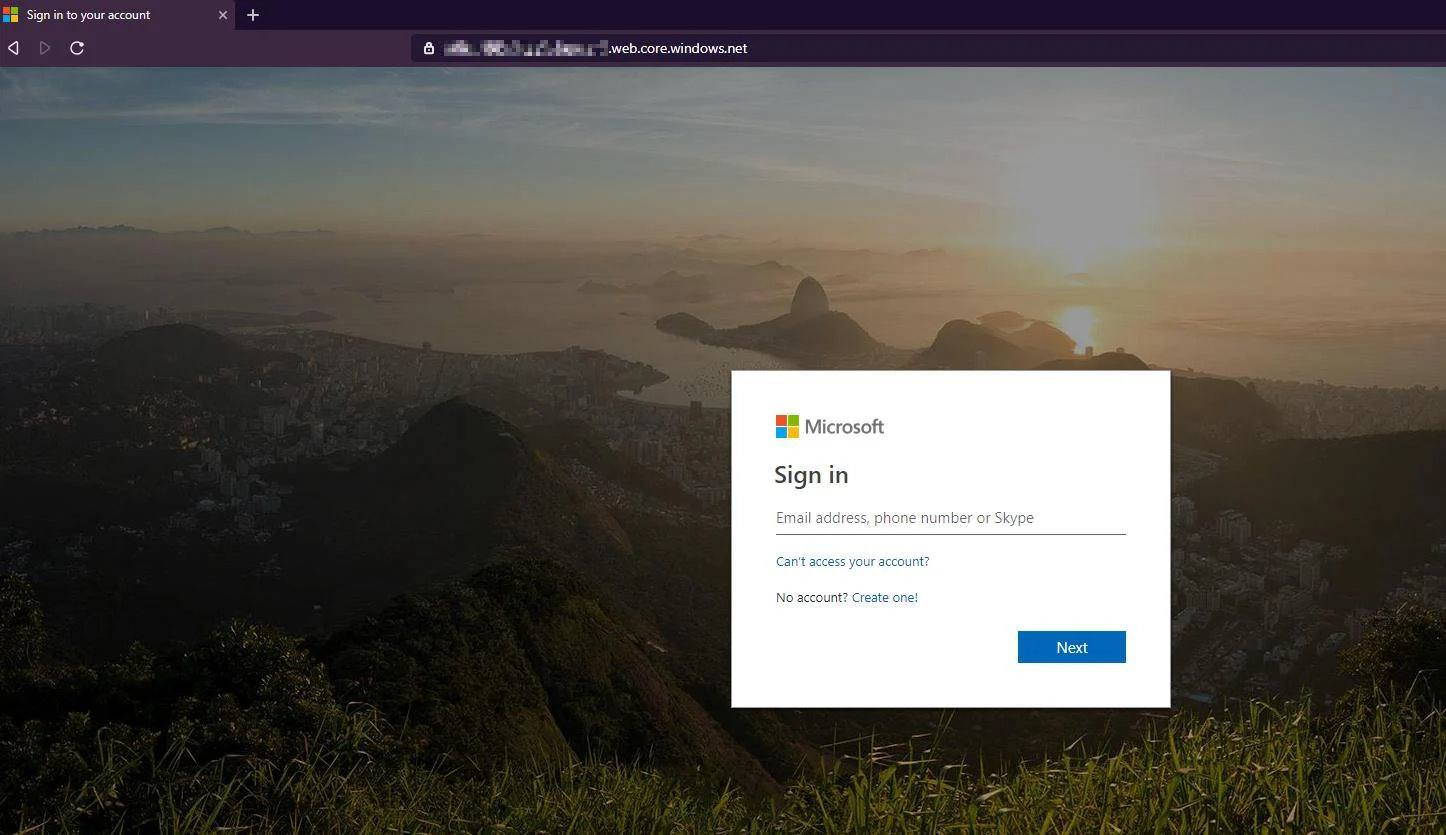
The landing page is a cloned Office 365 login page hosted on the Microsoft-owned web.core.windows.net domain by abusing the Azure Blob Storage and it comes with a valid Microsoft certificate, making it a lot harder to detect the phishing attempt.
Abusing the Azure Blob Storage platform to target Office 365 users is the perfect ruse seeing that the landing pages will automatically get their own secure page padlock because of the *.web.core.windows.net wildcard SSL certificate.
This way even the most suspicious targets could get tricked after clicking on the certificate and seeing that it is issued by a Microsoft CA to *.web.core.windows.net, automatically validating the phishing page as official Microsoft login forms in the eyes of potential victims.
"However, the URL of this site should not be trusted, and instead, users should only login from their main company affiliated webpage," Abnormal Security advises.
Phishing attacks targeting Office 365 customers
Azure Blob Storage subdomains being used to phishing pages is a known and highly effective tactic BleepingComputer reported about in the past [1, 2, 3].
These phishing attacks can easily be tackled if you set up custom Office 365 block rules to take advantage of the Office 365 ATP Safe Links feature to automatically block them.
If you don't configure block rules, the only way to be sure that attackers aren't trying to steal your credentials while entering them in an Office 365 login form is to remember that official login pages are hosted by Microsoft on the microsoft.com, live.com, or outlook.com domains.
Last month, Abnormal Security researchers discovered another highly convincing Office 365 phishing campaign that used cloned imagery from automated Microsoft Teams notifications attempting to steal credentials from almost 50,000 users.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now