Amazon Impersonated in Phone Call Scam
During the pandemic, the e-commerce industry has not only seen a dramatic rise in sales, but also in consumer-targeted email attacks. This attack features an impersonation of Amazon, utilizing an increasingly popular vector for malicious engagement—phone calls.
In this attack, scammers impersonate Amazon to steal valuable account and payment information from targeted consumers.
Summary of Attack Target
- Platform: Office 365
- Payload: Text, Phone Number
- Technique: Impersonation
Overview of Amazon Phone Number Scam
In this attack, the cybercriminals send an email impersonating an Amazon delivery. Close inspection shows that the sender’s name is presented as “Arnazon” (with an "r" and an "n" rather than an "m")—an attempt by the attacker to both trick recipients and bypass other email security solutions that look for brand impersonations. Attackers anticipate such typos will go unnoticed, as sender information is often overlooked and only the email content is read thoroughly.
The email originates from the domain ‘consumerlivesupport.com’, a recently registered domain that is not associated with Amazon. Additionally, the links in the email body redirect the recipient to "consumerlivesupport.com" rather than to Amazon itself.
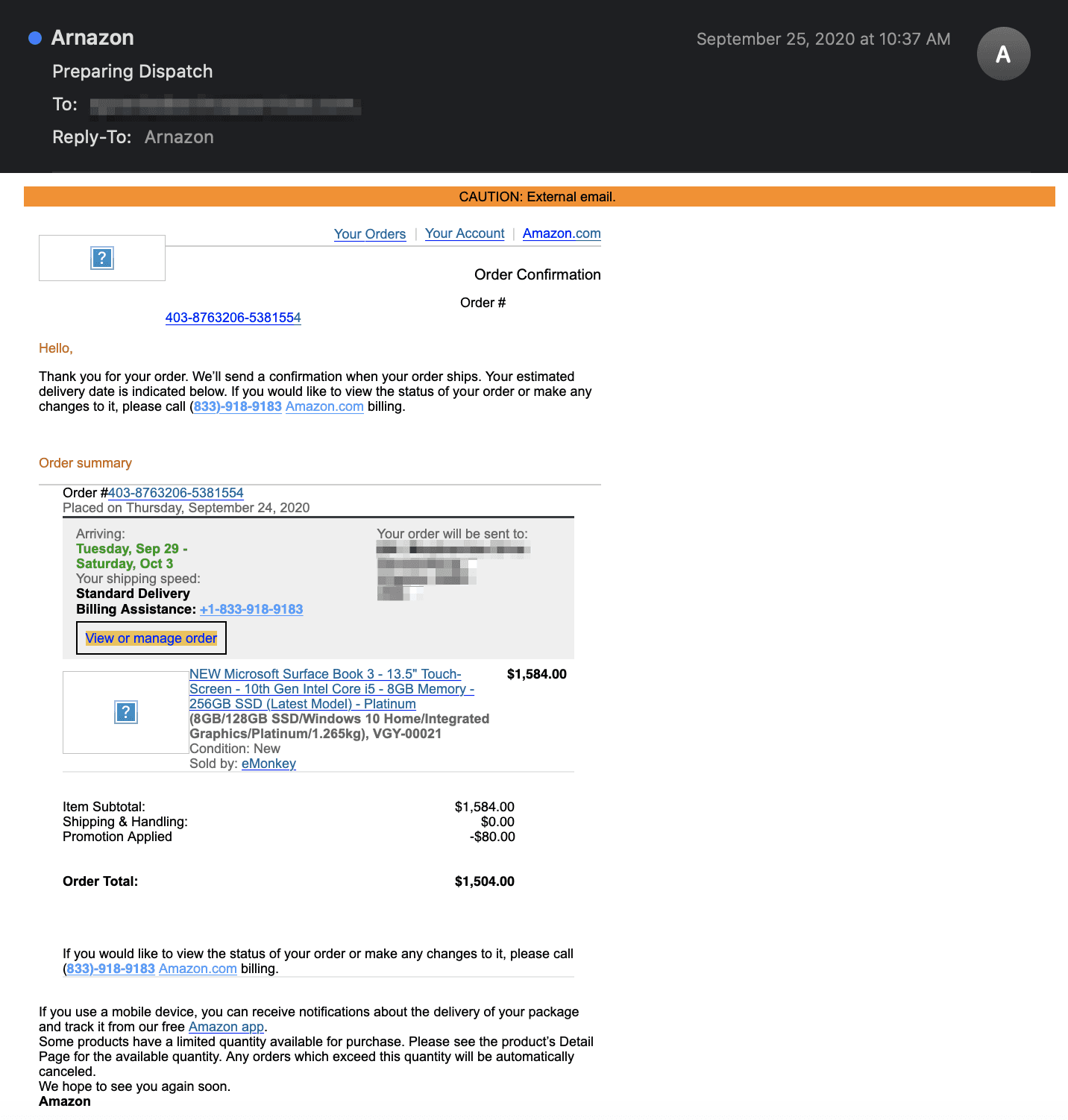
The email itself mimics the frequently seen Amazon order notification email at the price of $1,504.00—an astronomical sum for some. The text asks the recipient to contact the “Amazon Billing” phone number to resolve any issues. The fake order receipt is meant to spark concern, as the recipient did not place the order, leading them to call the provided billing support number.
However, further investigation reveals that this number does not match the customer support phone number found on the Amazon website. Instead, it is a misdirection so consumers release sensitive account information to phone scammers posing as Amazon support specialists.
If the recipient falls victim to this attack, they may ultimately release sensitive account details, as the attackers can leverage the credentials needed to access their account and the card to which their supposed refund would be directed.
Why the Amazon Impersonation Scam is Effective
The email is a fake receipt for a “recent Amazon purchase”, fostering a sense of urgency in the account owner to cancel the purchase and address a possible account breach before any other “orders” are made. The potential money loss will likely motivate the target to act quickly.
In addition, the email itself looks like a legitimate purchase notification from Amazon, displaying Amazon logos hosted on Amazon domains, as well as a detailed description of the purchased product. Additionally, the email is personalized, providing an address to where the supposed order is being sent and contact information for questions regarding the order.
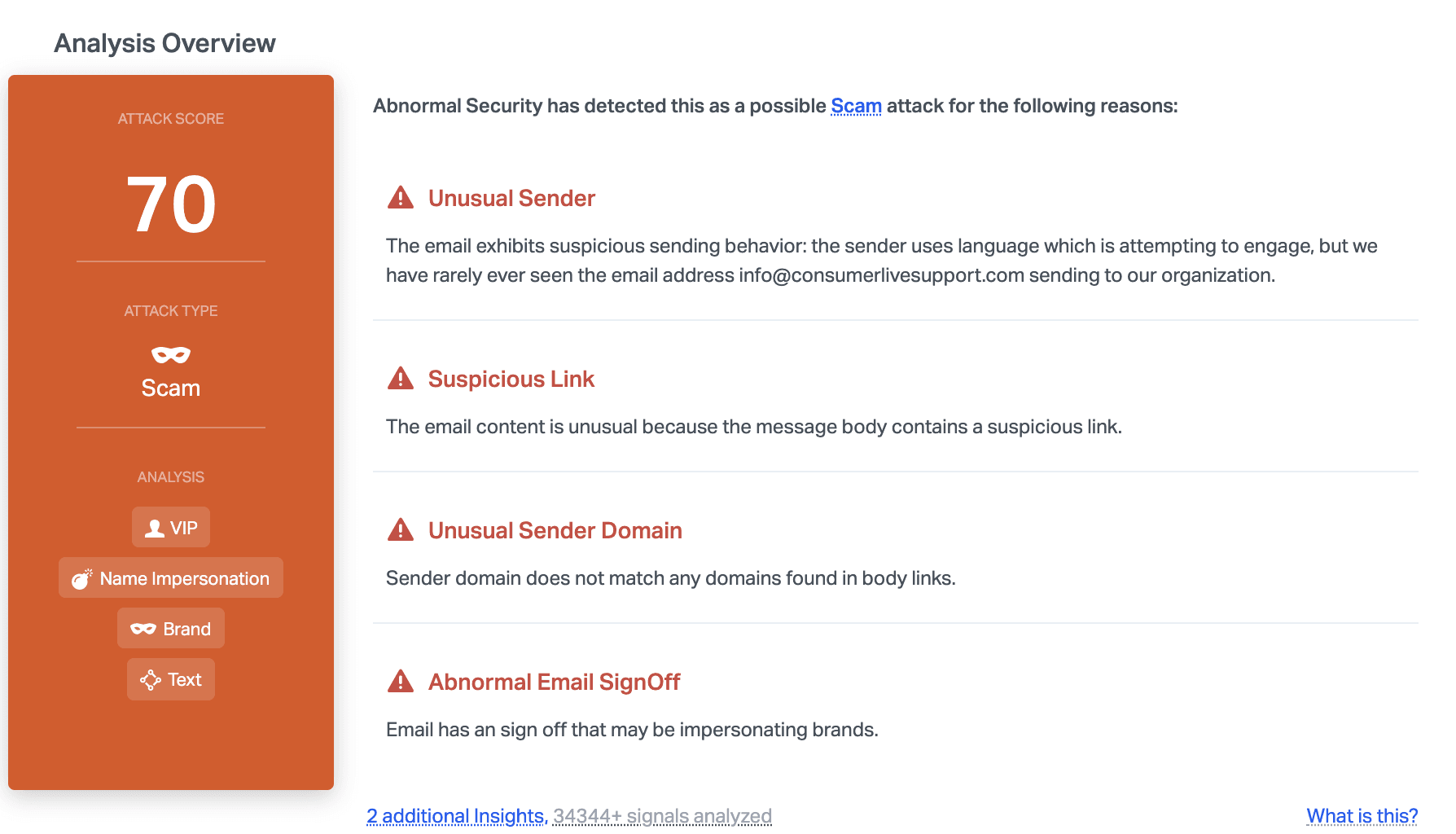
Abnormal can detect this malicious email due to the unusual sender information, the suspicious link, and the brand impersonation sign-off. When this is combined with the mismatched sender domain and the urgency included in the text, it provides the indicators needed to know that this email is malicious and block it before it reaches inboxes.
We have seen an increase in tech support scams that use a phone number as the attack vector, often going undetected by email security solutions. This is because, similar to social engineering attacks, this strategy for malicious engagement does not include easily identifiable threat vectors such as links or attachments. As the pandemic continues to push consumers toward online shopping, scammers may be seeing more success with this discrete vector approach and users should be wary of all attempts to transition to other mediums of communication.
To learn more about how Abnormal can stop these types of brand impersonation scams, see a demo of the platform.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

