SurveyMonkey Used in Office 365 Phishing Attempt
SurveyMonkey is a survey service that is normally used to host legitimate surveys. However, sometimes attackers will utilize file sharing and surveying sites like SurveyMonkey to host redirect links to a phishing webpage. By using these legitimate services, attackers can bypass email URL detection systems deployed by many email security tools.
In this attack, attackers send emails through SurveyMonkey in order to steal the Microsoft credentials of employees.
Summary of Attack Target
- Platform: Office 365
- Email Security Bypassed: Office 365
- Payload: Malicious Link
- Technique: Spear Phishing
Overview of the SurveyMonkey Phishing Attack
In this attack, the email is sent from a real SurveyMonkey domain (surveymonkeyuser.com), but with a different reply-to domain. That reply-to domain was registered only one month ago. The email simulates an automated notification with a link to open the statement, or survey.
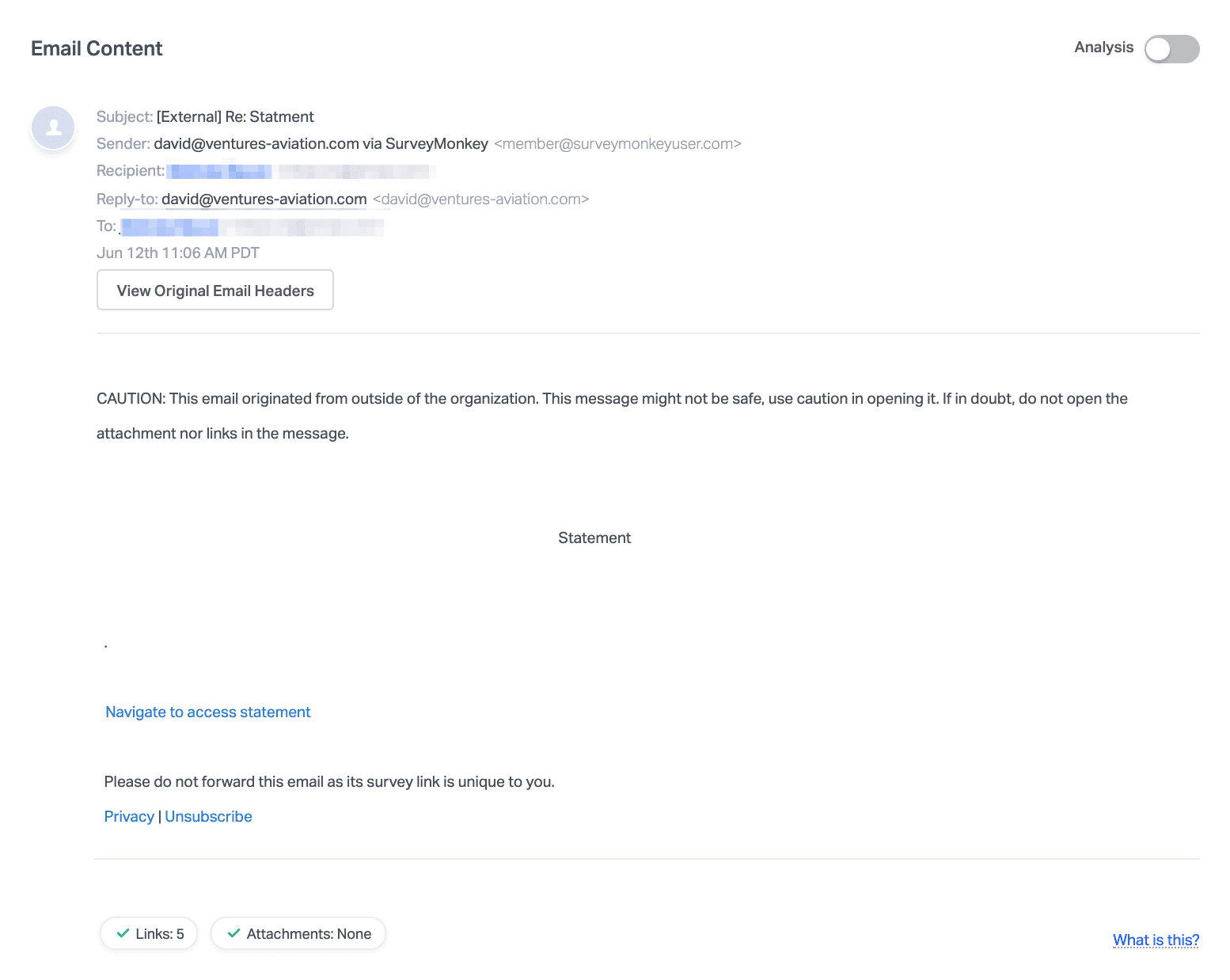
Within the body of the email is a hidden redirect link appearing as the text “Navigate to access statement” with a brief message “Please do not forward this email as its survey link is unique to you”. Clicking on the link leads to a real SurveyMonkey page with a link to a supposed Billing Statement.
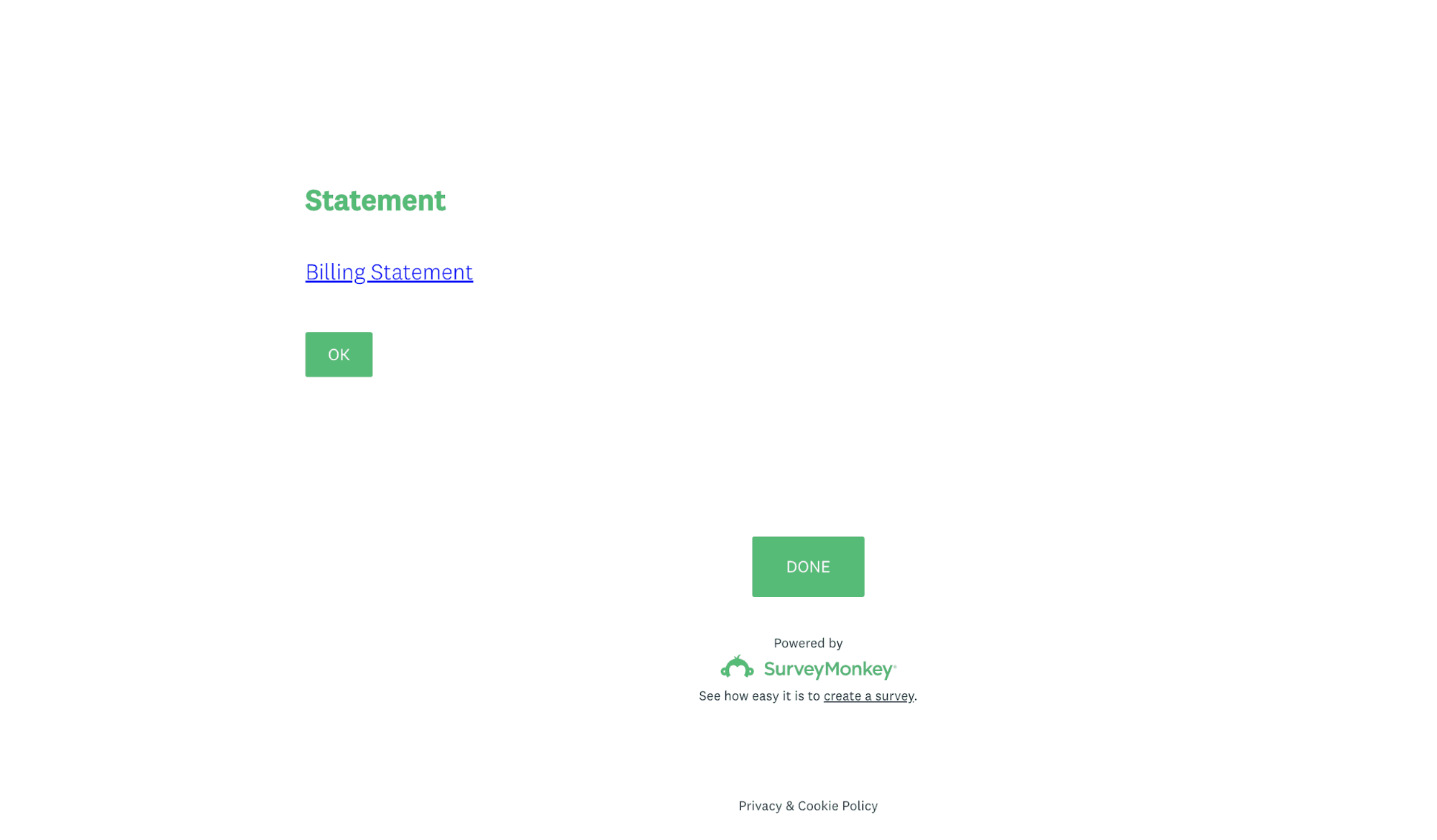
Clicking on the link within the SurveyMonkey page redirects to a site hosted on a Microsoft form submission page. This form asks the user to enter their Office 365 email and password.
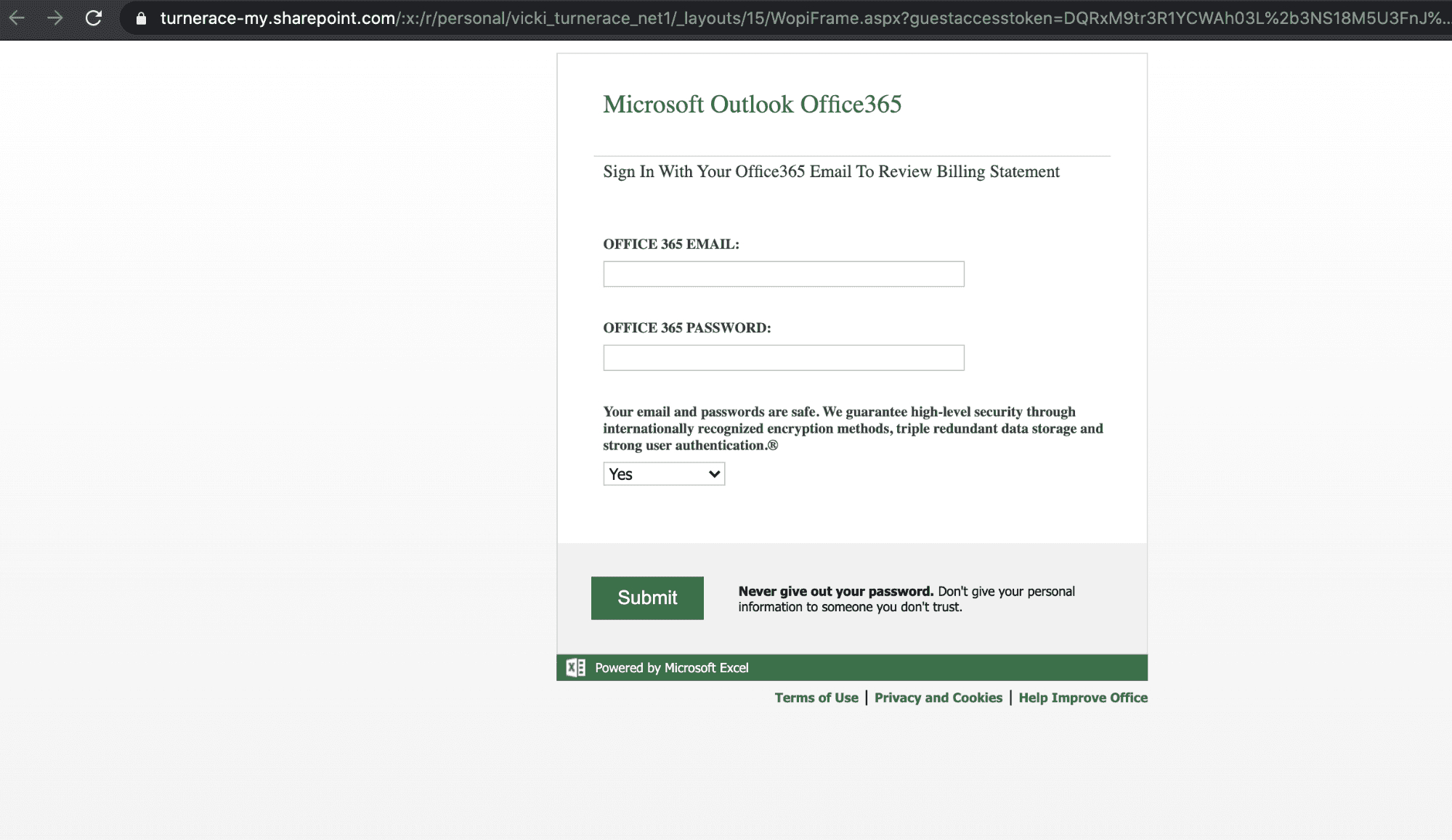
From here, the user is asked to enter their information. If they are not vigilant and provide their credentials, the user account would be compromised.
Why the SurveyMonkey Phishing Attack is Effective
Since the URL isn’t visible within the body text, it is easy to miss at first glance. The first link actually redirects to a real SurveyMonkey link, and then finally to the landing page of the phishing site. As these emails originated from the legitimate SurveyMonkey email address, and the body of the email contains a link to the real SurveyMonkey domain, one would easily believe the email to be benign.
Furthermore, because the email mentions that each survey link is unique to each recipient of the email, users may be primed to think that the login page is there to validate that their responses are from the legitimate recipient of the email. Thus, the behavior isn't unexpected, even if it's atypical—recipients should never enter their email credentials into a survey, regardless of which service is providing it.
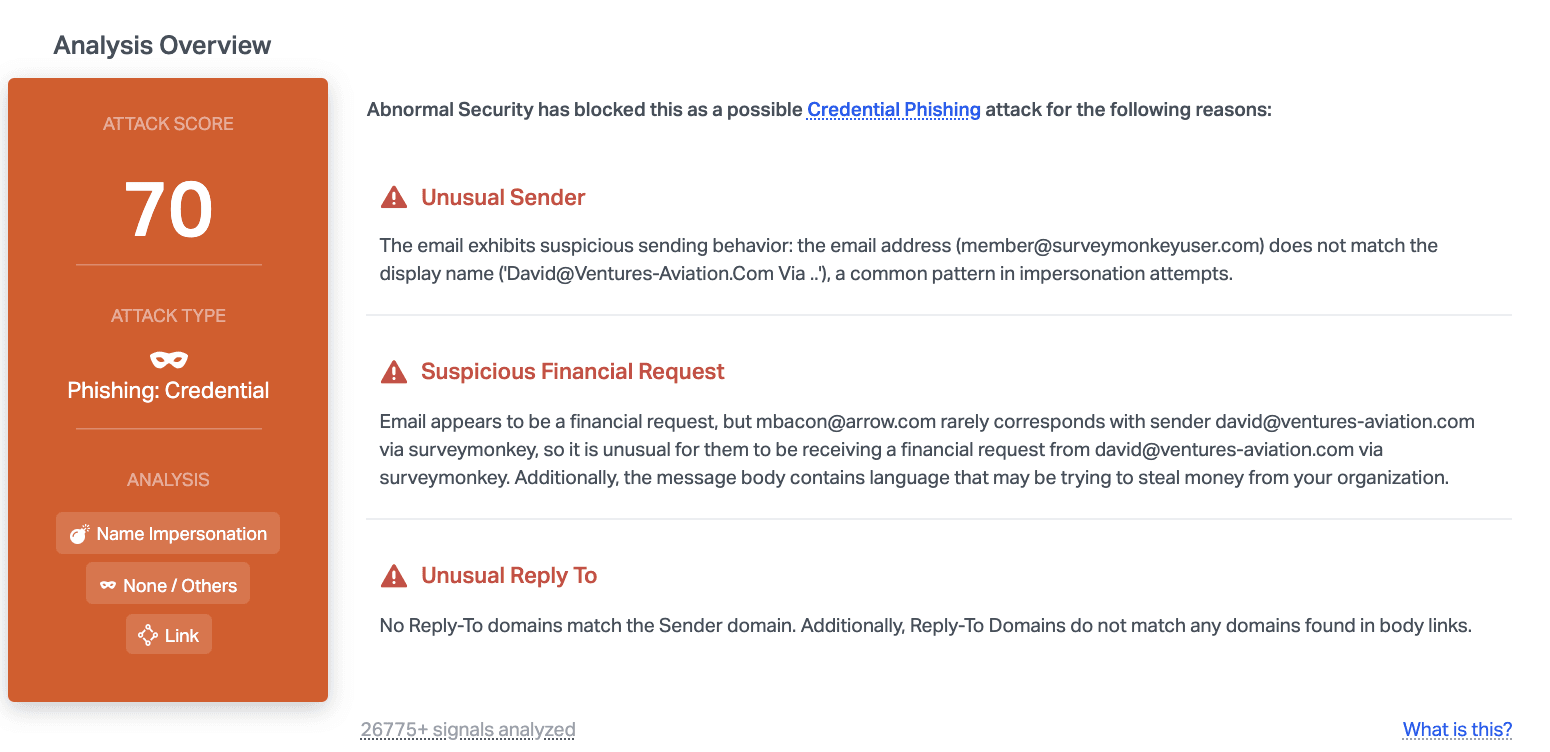
Abnormal is able to detect this attack due to the unusual sender information, unusual reply-to information, and the suspicious request. Because the email mentions a "statement" that takes people to a SurveyMonkey site, this is considered a suspicious financial request and when combined with other factors, indicates that the email is likely a phishing attempt.
To learn more about how Abnormal detects and stops credential phishing emails, request a demo today.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

