Legitimate Dropbox Transfer Used to Phish Microsoft Credentials
As the COVID-19 pandemic continues, governments worldwide are providing relief funds for small business owners impacted by lockdowns and closures. This allows attackers to exploit current efforts by the government, particularly since applicants to these funds typically have to provide documents to prove their eligibility.
Since applicants are expecting email correspondence, this provides attackers with a unique opportunity to impersonate legitimate authorities and extract sensitive information from customers. In this attack, threat actors use a Dropbox link and landing page to do so.
Summary of Attack Target
- Platform: Office 365
- Victims: Small Business Owners
- Payload: Phishing
- Technique: Impersonation
Overview of the Dropbox Transfer Attack
The email itself is an automated message from the sender “no-reply@dropbox.com” which is an official Dropbox domain. The body contains a link to the file “COVID-19-Relief-Payment.PDF” with information about the size of the file, a brief description of the file, and the expiration date.
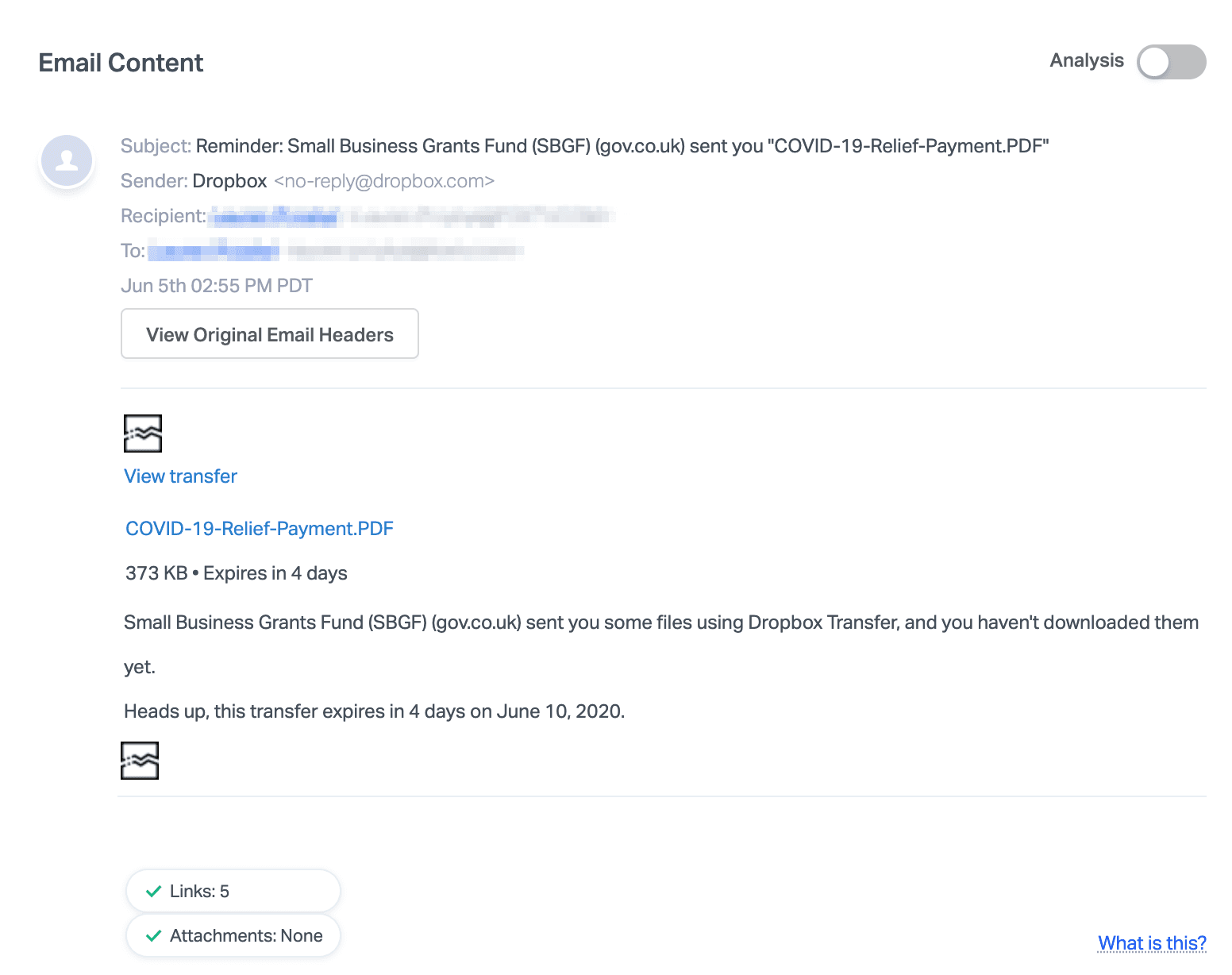
The attack itself is a two-step process. First, the recipient must click the link provided in the email, which leads to a standard Dropbox transfer landing page with the enablement to download the file.
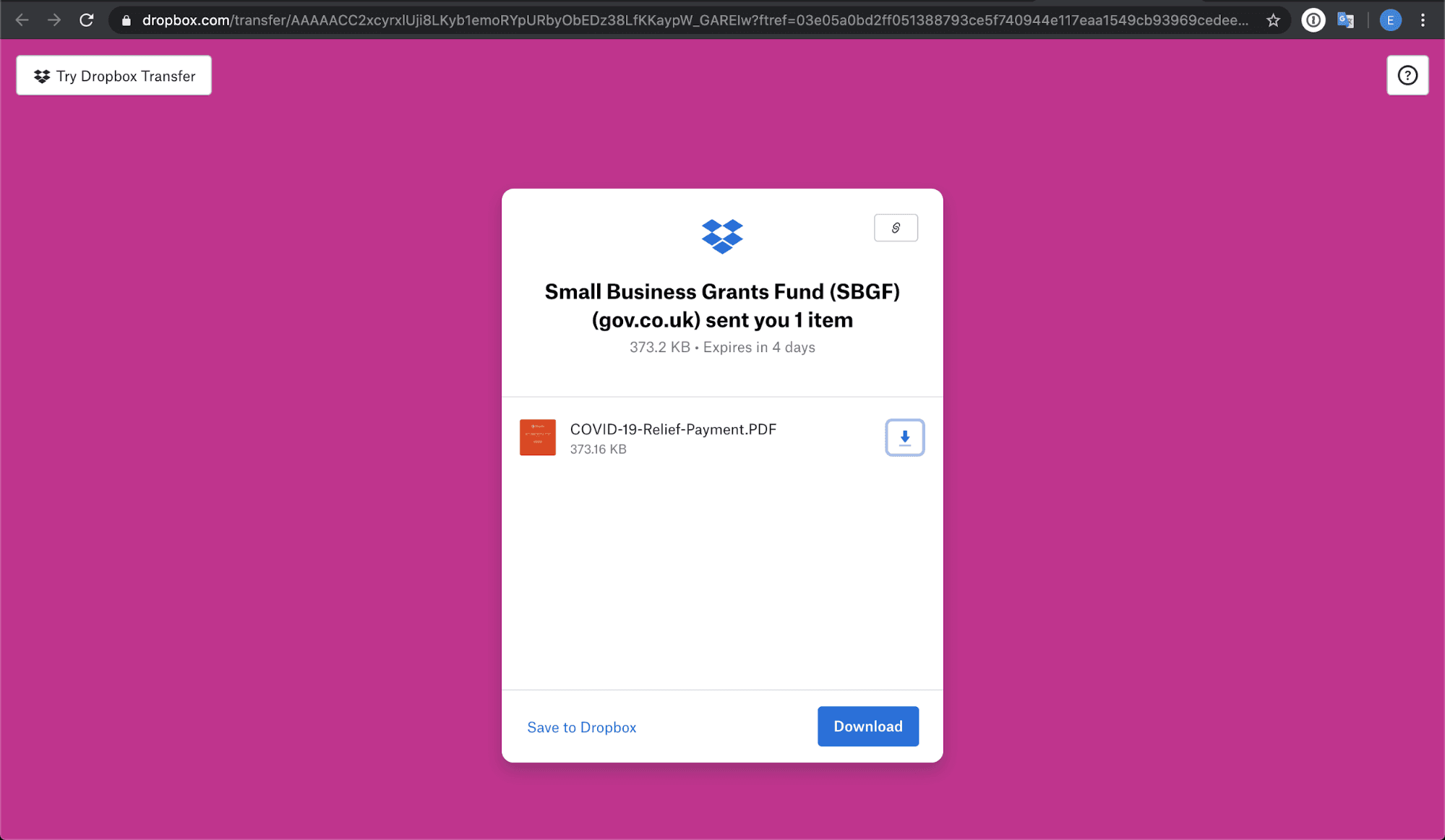
After clicking on the download button, the page is redirected to a phishing landing page. In the second step, the landing page contains an O365 image with a button to “Access Document”. This is where the intent is revealed, which is to gain access to the user's Microsoft credentials.
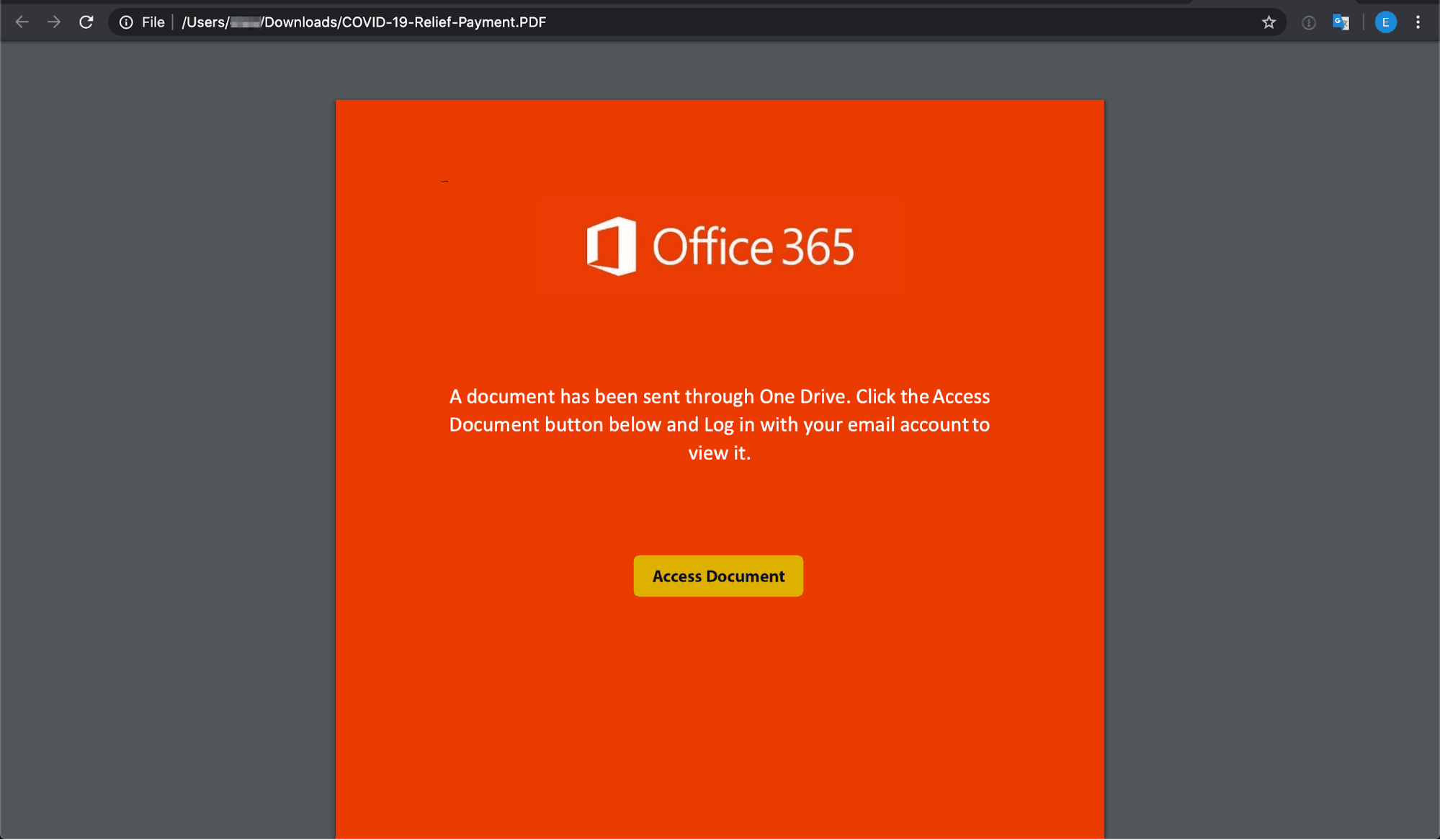
In order to access the fake document, the user must input their Office 365 credentials. The moment they do so, their Microsoft credentials on all accounts are compromised, providing access to Outlook, SharePoint, OneDrive, Teams, and other Microsoft applications. From there, this account takeover can lead to data or financial loss for the organization, and the account itself can be used to send additional attacks on employees, customers, or partners.
Why the Dropbox Transfer Attack is Effective
There is a sense of urgency in the message, which states, "Heads up, this transfer expires in 4 days on June 10, 2020.” It appears that if the recipient doesn't download the file within the given timeframe, the file will expire and they might assume that the opportunity to receive relief funding will be missed or delayed. And even for vigilant email recipients who check the sender address, an automated message from the dropbox.com domain does look innocuous enough to at least click on the links provided.
This is a sophisticated attack because, by using Dropbox Transfer to send files, it is not necessary to spoof headers, as the sender name will come from the legitimate Dropbox domain. Not only does this bypass traditional mail filters, but it also goes undetected by any existing web proxy and firewall controls. This is also extremely convenient for attackers because they can send the payload without ever having to verify if the targeted network is allowing an inbound SMTP or testing firewalls/proxies.
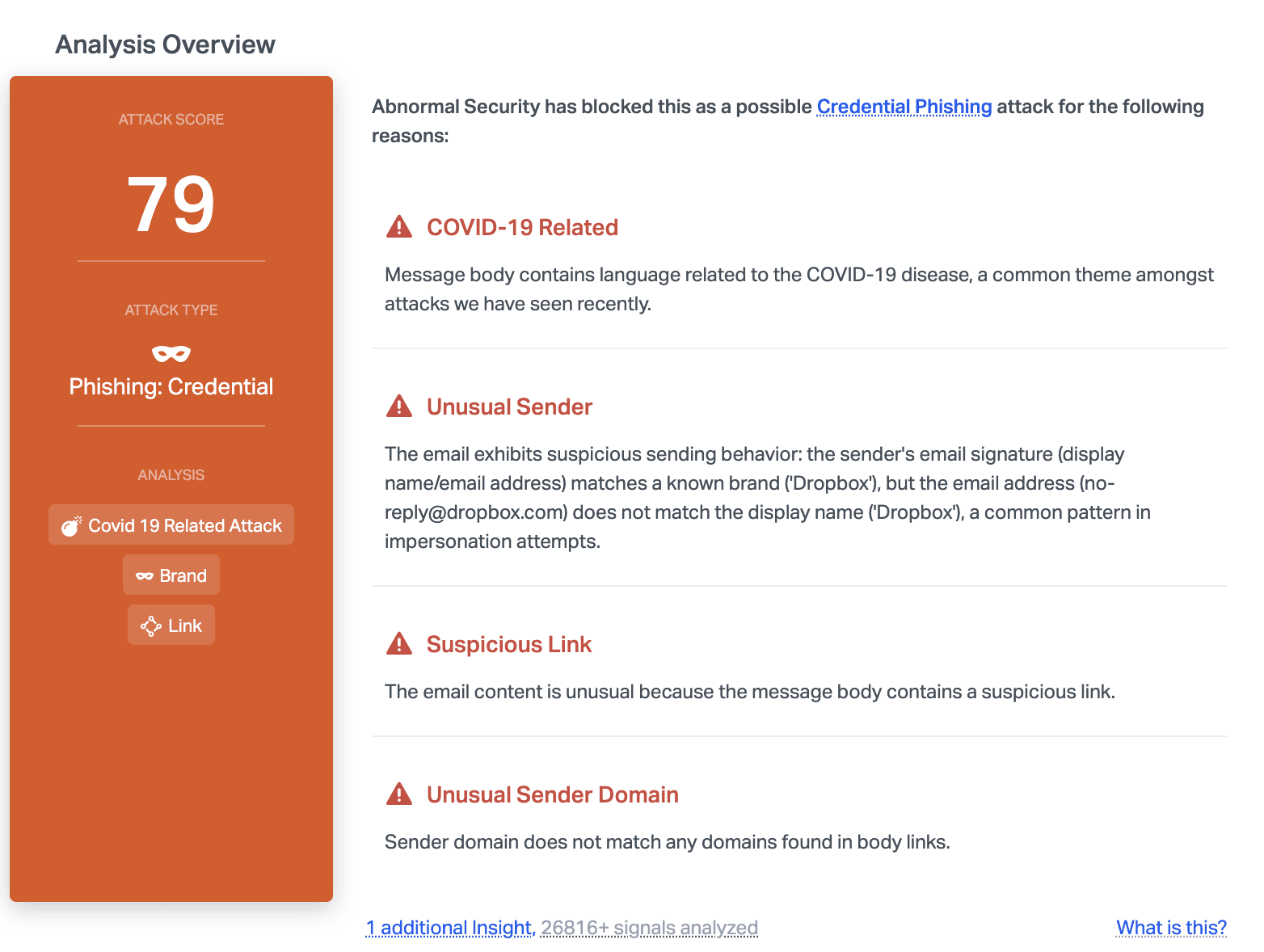
Abnormal can stop this attack due to the unusual sender domain where it does not match any domains found in body links. In addition, the content of the email is related to COVID-19, a common theme right now for cyber attackers who are looking to take advantage of the pandemic.
To learn how Abnormal can protect your employees from Dropbox transfers and other malicious emails, request a demo today.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.