Bank Impersonated in Credit Card Phishing Scam
Cybercriminals are leveraging the uncertainty around the spread of COVID-19 as everyone focuses more on safety and security during these times. As markets crash, the attacker knows that people will look to protect their financial assets, and thus be vulnerable to attacks claiming to secure their bank accounts.
In this attack, attackers impersonate a major credit card provider and attempt to deceive victims into divulging their login credentials by sending COVID-19-themed emails that direct recipients to convincing landing pages.
Summary of Attack Target
- Platform: Office 365
- Email Gateway: Proofpoint
- Victims: Employees
- Payload: Malicious Link
- Technique: Impersonation and Email Spoofing
Overview of the Credit Card Phishing Attack
In this attack, the threat actor crafted a convincing email and landing page that appeared to come from a major credit card provider. The email masquerades as an important notification asking recipients to secure their bank accounts during this difficult time.
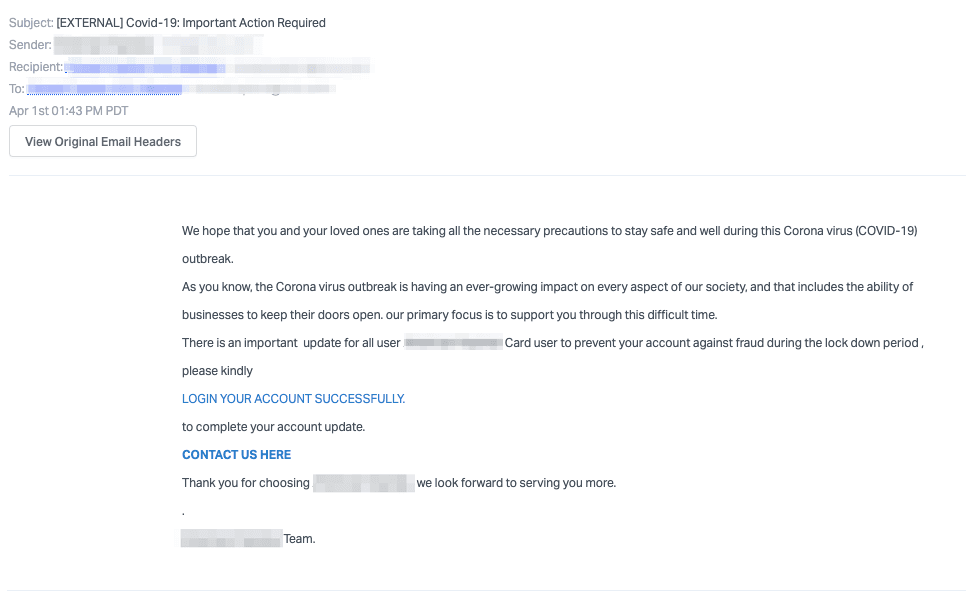
While the email contains several spelling errors and doesn't include the bank name, the attackers are relying on the pandemic to add fear to the situation. When clicking on the link, the phishing page is hidden behind a redirect which hides the true URL of the page, which attackers likely control and will use to steal the victim’s bank login credentials.
Should recipients fall victim to this attack, their bank account, credit card information, and other personal details stored on the bank’s website will be at risk.
Why This Credit Card Phishing Attack is Effective
The email and landing page that the attacker created were convincing and while the email contained some errors, the landing page nearly replicates the true credit card provider's landing page. Recipients would be hard-pressed to understand that this was, in fact, a site designed specifically to steal their credentials.
In addition, the URLs were wrapped with redirect links so the user would be unable to tell if the links redirected to the authentic credit card provider's webpage. Attackers likely expected that recipients would be too convinced by the landing page they created to double-check that the URL was valid.
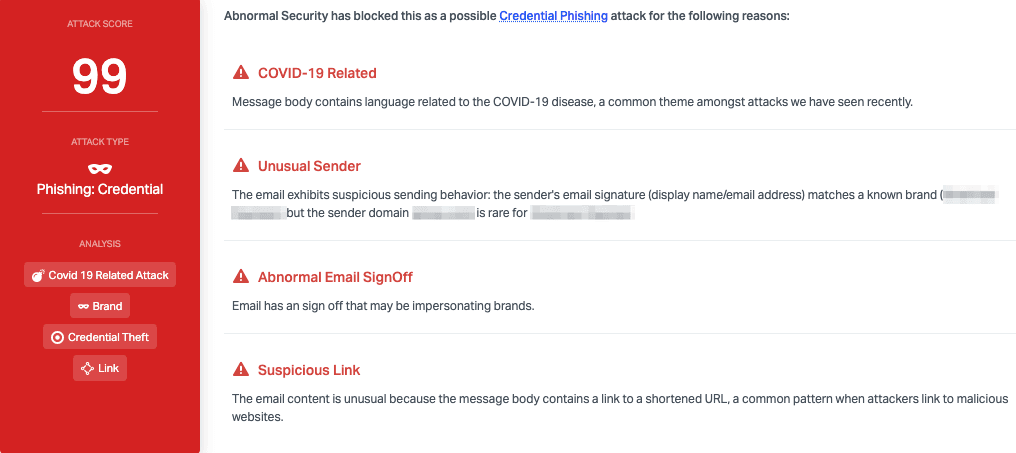
Abnormal stopped this attack due to a variety of factors, including the unusual sender domain, which does not typically send on behalf of this brand. In addition, the abnormal email signoff and the suspicious link were key indicators that the email was malicious and allowed Abnormal to block it before it hit inboxes.
Learn more about how Abnormal blocks credit card phishing and other brand impersonation attacks by requesting a demo today.
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.

